In the rush to virtualization, security seems to be an afterthought, according to a survey of 302 IT professionals by security vendor Prism Microsystems. Though these pros seem aware of the dangers that come with virtualization, many are using get-by strategies and failing to heed best practices. Those practices could prove to be costly in the end – especially if there’s a data breach. That’s why, with money so tight, Prism Microsystems’ Steve Lafferty, VP of marketing, advocates for a “single point of control to seamlessly monitor the entire IT infrastructure, from the physical to the virtual.”
Click through to see eight key findings from a recent survey by Prism Microsystems.
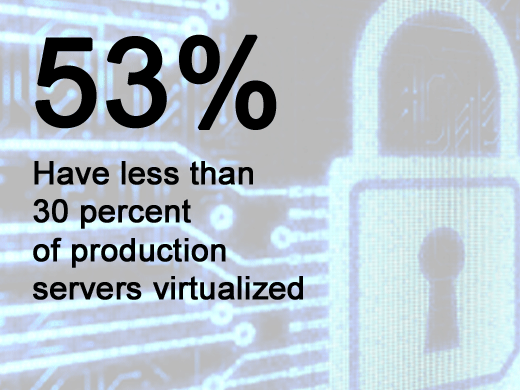
Though 85 percent have adopted virtualization to some degree, for the majority (53 percent) that meant 30 percent or fewer production servers virtualized. That is expected to increase to more than 60 percent of servers by the end of 2011 for most respondents.
A majority (86.3 percent) agreed that securing the virtual infrastructure was as important as securing the physical environment. Almost 60 percent used traditional security tools to secure the virtual environment, though 51.3 percent felt traditional solutions were not adequate for the task and 24.5 percent weren’t sure about it.
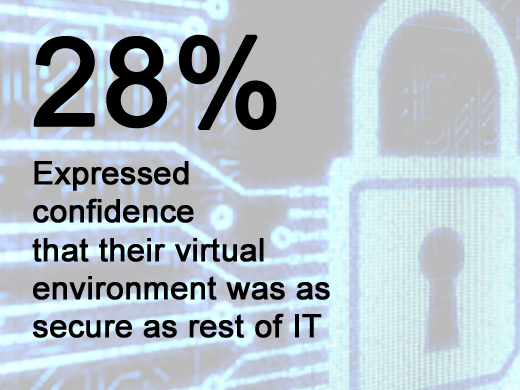
Only 28 percent expressed confidence that their virtual environment was as secure as the rest of their IT architecture. However, 52 percent of respondents disagreed with the statement that virtual environments are inherently less secure than their physical counterparts.
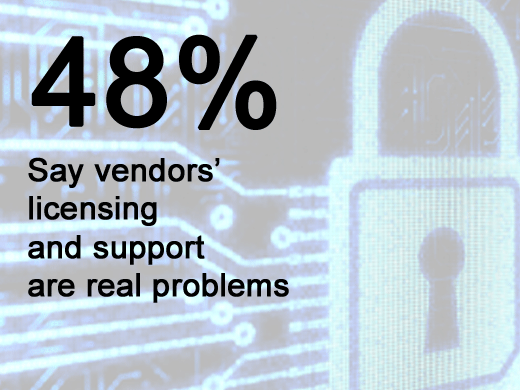
Though lack of budget was the most-cited (51 percent) reason keeping IT from adequately securing the virtual infrastructure, lack of staff expertise (48.1 percent) and vendors’ licensing and support models (40.2 percent)followed closely behind (Multiple answers were allowed.)
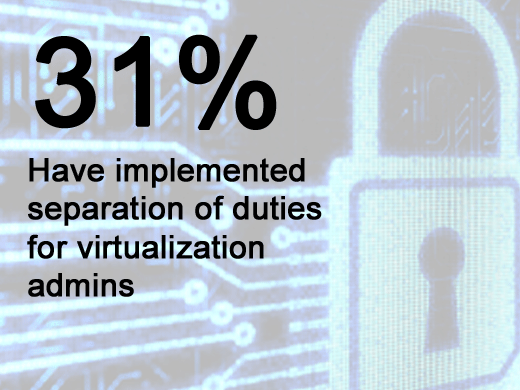
Of those using virtualization, only 31.2 percent have implemented the best practice of separation of duties between IT personnel responsible for the provisioning of virtual infrastructure and other administrator groups. This raises the risk from privileged insiders.
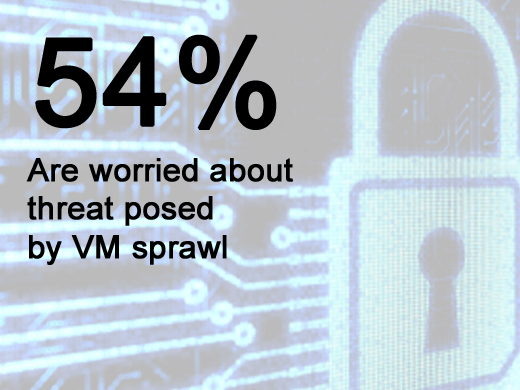
Though the top two security concerns were ‘The potential for the hypervisor to create a single-point of entry into multiple machines instances’ (58.1 percent) and ‘The introduction of a new layer that can be attacked’ (56.6 percent), the threat of VM sprawl and the potential to create invisible machines (53.9 percent) was almost as worrisome.
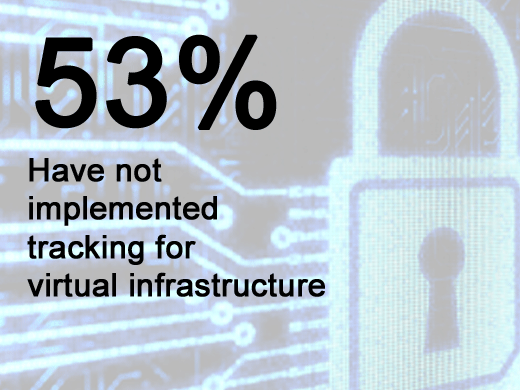
While a majority agreed that it’s important to monitor (79.5 percent) and track (89.3 percent) the virtualization layer, nearly 25 percent were not collecting logs at all, nearly 35 percent were not monitoring user activity, nearly 47 were not monitoring access to critical data and nearly 40 percent were not reporting on access and controls for compliance purposes. In fact, a majority (52.70 percent) have not implemented tracking procedures for any layer of the virtual architecture.
Only 19.5 percent were satisfied with the logging and auditing capabilities for their virtual environment compared with 53.1 percent satisfied with the logging and auditing in the non-virtual environment.