DevOps can turn a slow, sclerotic app development and support framework into a lean, lithe operation that lowers costs and provides better service to users. But if you are not careful, it can also introduce vulnerabilities to a data environment that is already susceptible to quickly evolving security threats.
This is why many experts are starting to sound the alarm on DevOps, or, at least, the tendency to view DevOps only in terms of all the wonderful things it can accomplish without conducting a proper assessment of the risks it entails.
But since DevOps is all about agile development and continuous alterations to application code, how can anyone ensure that dynamic changes to any aspect of the app or service will not produce unforeseen consequences for security, governance, operations, or a host of other factors?
According to Tim Buntel, DevOps advocate at XebiaLabs, the most significant change that DevOps brings to the security equation is where and how it is implemented in the now-combined development/operations workflow. He and others are advocating a “shift-left” approach in which security is implemented as a core requirement early in the process, giving it a stature equal to performance and basic functionality.
“Shift-left comes from the idea that traditional security has been an afterthought, tacked on at the end of the process,” he said. “The goal of DevOps is to create organizations that are cross-functional and are running processes that are fast-moving and automated, so the idea of something like security being handled by a completely separate team is anathema to DevOps.”
To take security and shift it to the left, therefore, is to place it earlier in the continuous development pipeline along with other previously separate functions like quality assurance and testing. In this way, the entire development team assumes shared responsibility for security and, hopefully, it will remain a key consideration throughout the entire lifecycle of the project – from initial concept to development and in the feedback loop that powers the continuous integration/continuous deployment (CI/CD) model.
But is this just a matter of taking today’s security functions and adding them to the development cycle? Not exactly, says Buntel. The speed at which DevOps projects are initiated and completed all but mandates a higher level of automation, as well as other capabilities such as lightweight static analysis, advanced threat modeling and real-time alerting to ensure team members are made aware of vulnerabilities, even potential ones, as quickly as possible.
“The reason why we are having such problems with security breaches these days is that no one is really owning it except the security folks,” Buntel said. “Most enterprises have 1.6 security professionals for every 100 developers and are experiencing somewhere on the order of 500 days for a given open window of opportunity. By shifting security into the development process, the likelihood of a security problem is reduced because developers can find out about it early, build the solution into code and test it right in the CI cycle.
“It also means that if a vulnerability gets into production and someone takes advantage of it, there is a much tighter feedback loop between discovery and resolution,” he added.
At the same time, organizations will have to implement security on the new forms of virtual infrastructure that are evolving in the DevOps world. Many applications and services, in fact, are already transitioning to containers, which offer vastly improved portability and resource utilization over standard virtual machines. This involves ensuring that the base container images are secure, kernel access is locked down, and the orchestration layer is well-monitored to prevent vulnerabilities from emerging during the normal interplay of services and microservices.
If anything, transitioning to a DevOps model should significantly enhance enterprise security simply because it supports a proactive response to emerging threats, not the reactive solution that exists today. As organizations learn the nuances of keeping applications and services up-to-date and forward-leaning, the ability to constantly tailor security postures to ever-changing conditions should emerge as well.
This isn’t to say that the new enterprise will be immune to breaches, but it does set the bar significantly higher than it is today. At the same time, organizations should be able to minimize the damage that does occur and restore applications and infrastructure to their normal states much faster.
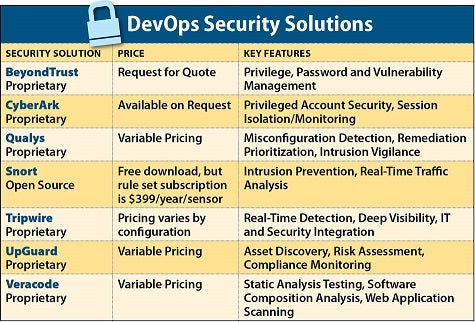
Below are some of the leading security solutions for DevOps environments:
BeyondTrust
BeyondTrust provides a unified solution that reduces risk throughout the IT supply chain. It includes automated device discovery, validation and management, as well as identification and remediation of Docker vulnerabilities and full visibility over account usage. The system adheres to a “secure cloud first” strategy and includes a full API library to streamline access management across the entire DevOps process.
CyberArk
CyberArk focuses on preventing attacks through insider privilege vulnerabilities. The platform features tools such as an enterprise password vault, privileged session management, threat analytics, and both application and endpoint identity management. The system is designed to integrate seamlessly into legacy environments using an advanced discovery process and an enterprise-class integration API.
Qualys
Qualys is an integrated security and compliance solution for on-premises and cloud-based applications. It aims for two-second visibility across all IT assets regardless of location using a combination of cloud agents and virtual, appliance and internet scanners. It provides native integration with AWS, Google Cloud, Azure and other clouds, providing vulnerability assessment and remediation, web app protection, systems monitoring and other functions.
Snort
Snort can be configured as a basic packet sniffer/logger or as a full-blown network intrusion detection system (NIDS). It can also perform protocol analysis, content search and match, and spot a variety of attacks and probes, such as buffer overflows, stealth port scans and OS fingerprinting attempts.
Tripwire
Tripwire aims to build a solid security foundation through file integrity monitoring, system hardening, compliance enforcement and other functions. The platform also provides security automation and remediation by automating workflows through integration with SIEMs, IT-GRC and other change management systems. It also provides investigation and root cause analysis.
UpGuard
UpGuard provides security and compliance for on-premises and cloud-based infrastructure, including servers and network devices. It uses a universal blueprint for any node type, as well as agentless monitoring and customizable benchmarks for automated tests. Change monitoring oversees files, packages, ports and other elements.
Veracode
Veracode is a cloud-based solution that aims to provide a secure application environment from inception to production. The system stresses automation and speed to locate and correct software vulnerabilities at the most efficient point in the development process, regardless of whether the app is based on open or commercial code.
Arthur Cole writes about infrastructure for IT Business Edge. Cole has been covering the high-tech media and computing industries for more than 20 years, having served as editor of TV Technology, Video Technology News, Internet News and Multimedia Weekly. His contributions have appeared in Communications Today and Enterprise Networking Planet and as web content for numerous high-tech clients like TwinStrata and Carpathia. Follow Art on Twitter @acole602.