One of the biggest concerns business and IT leaders alike share when it comes to anything to do with Internet of Things (IOT) projects is security. The more devices that get connected to the internet, the bigger the attack surface that needs to be defended becomes.
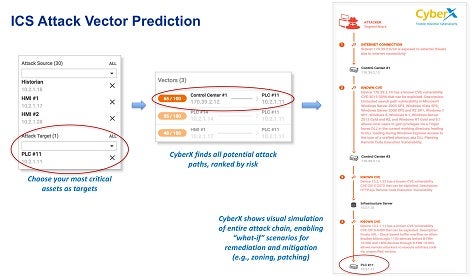
To help IT organizations better defend those environments, CyberX today unveiled simulation software that enables IT security teams to model industrial control system vulnerabilities using the latest attack vector and breach information available. Dubbed ICS Attack Vector Prediction software, the simulation software relies on data gathered via an agentless ICS security platform developed by CyberX that employs analytics on top of a deep packet inspection engine to identify ICS vulnerabilities. Armed with that information, CyberX is now in a position to create simulation software that can model and pinpoint potential attack vectors that cybercriminals might exploit.
Phil Neray, vice president of industrial cybersecurity for CyberX, says the challenge with the IoT in general and industrial control systems specifically is that there is no shortage of platforms that need to be defended. Most ICS platforms are based on proprietary operating systems. IT organizations are going to find themselves severely challenged in the years ahead as the number of potential IoT vulnerabilities that need to be tracked continues to expand exponentially, says Neray.
“It’s not a traditional IT environment where everybody is running either Windows or Linux,” says Neray.
ICS platforms are a particularly vexing security challenge because both cybercriminals and nation states have identified them as critical targets. In addition to trying to economically harm rival economies by sabotaging ICS platforms, those ICS platforms are often at the top of the target list in the event hostilities ever break out. Most IT organizations are severely overmatched when it comes to defending ICS platforms from those types of cyberwarfare attacks. Platforms such as CyberX will at least give IT organizations tasked with securing critical ICS platforms a much better idea of what they are truly up against.