 While there may have been a time when IT organizations could dictate which devices and applications end users could use, employees are increasingly spending their own money to not only buy devices, but also contract to use software-as-a-service applications. Of course, sometimes the definition of their own money is fluid. They may not be using the IT budget, but in many instances they are using budget dollars allocated to the business unit they work for.
While there may have been a time when IT organizations could dictate which devices and applications end users could use, employees are increasingly spending their own money to not only buy devices, but also contract to use software-as-a-service applications. Of course, sometimes the definition of their own money is fluid. They may not be using the IT budget, but in many instances they are using budget dollars allocated to the business unit they work for.
A new study from International Data Corp., conducted on behalf of Unisys, finds that this creates a lot of potential risk in the form of corporate data on any number of unmanaged devices and applications that are beyond the reach of most data governance policies. Coming down hard on this practice is not an especially savvy political move for most IT leaders. And most of them don’t have the internal expertise to manage these devices.
Will the consumerization of IT be the final nail in the internal IT support desk, or is there some middle ground to be had between end users rebelling against the status quo and IT organizations that are ultimately responsible for the corporate data?

Click through for results from an IDC study, conducted on behalf of Unisys, regarding the consumerization of IT and subsequent security risks.
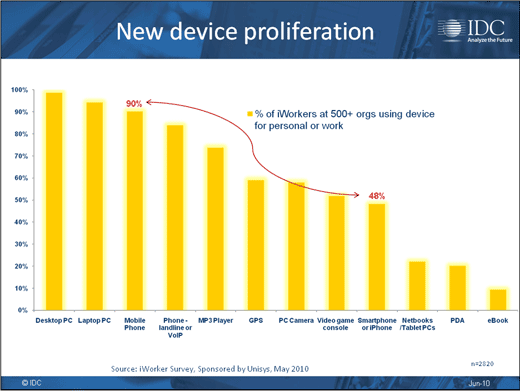
Smartphone adoption is particularly rampant.
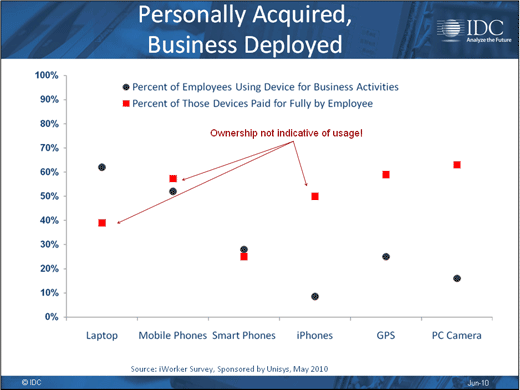
Employees are paying for the privilege.
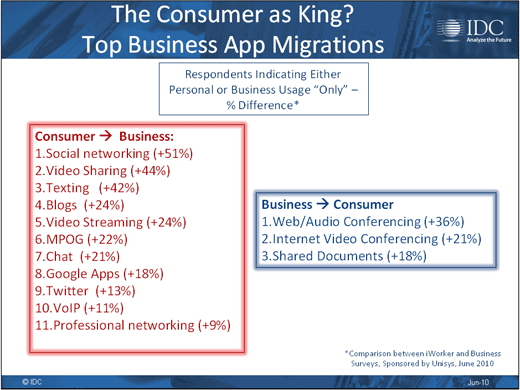
Social networking and video are the most business-centric applications.
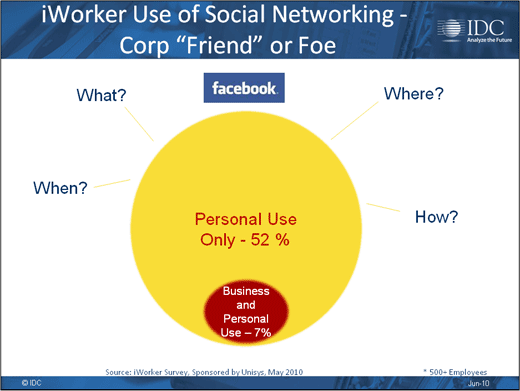
Business enabler or time waster?
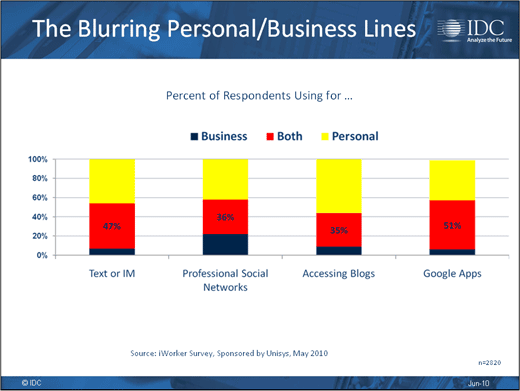
Over one-third of respondents use devices for both.
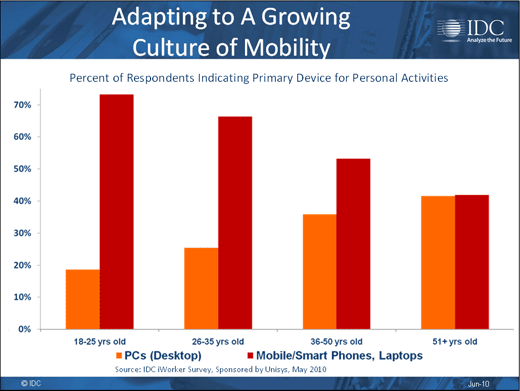
The younger the worker, the more mobility there is.
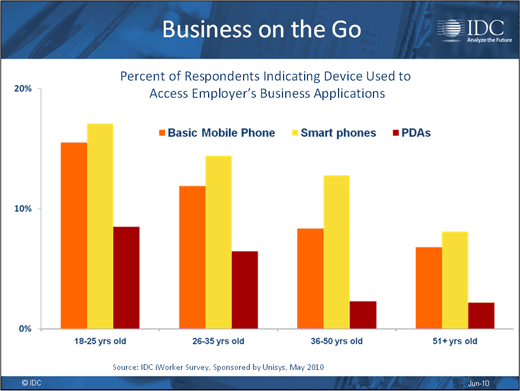
And many of those workers are increasingly accessing business applications.
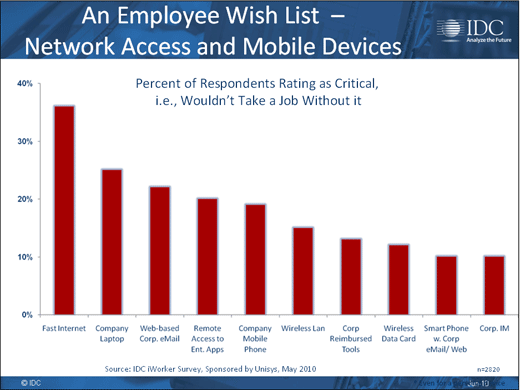
It’s the new world of standard-issue equipment.
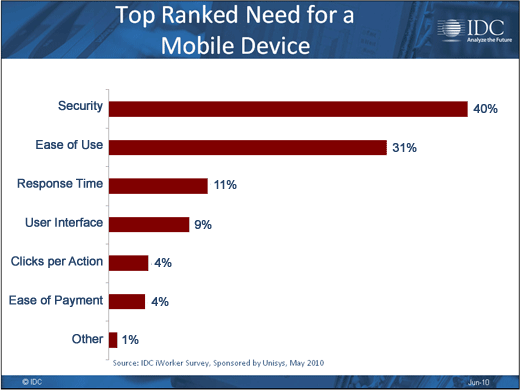
Users are getting more mature about security.
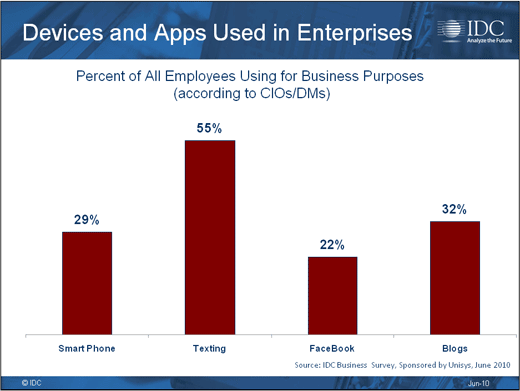
Most usage today is still relatively rudimentary.
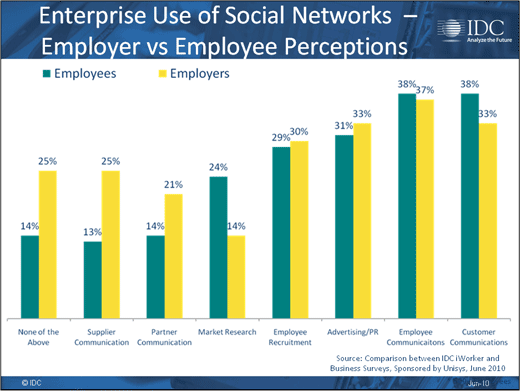
Some convergence between business and end users seen.
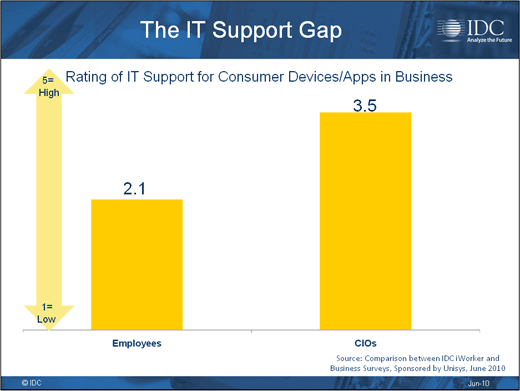
IT thinks it is a lot better at mobility than most users.
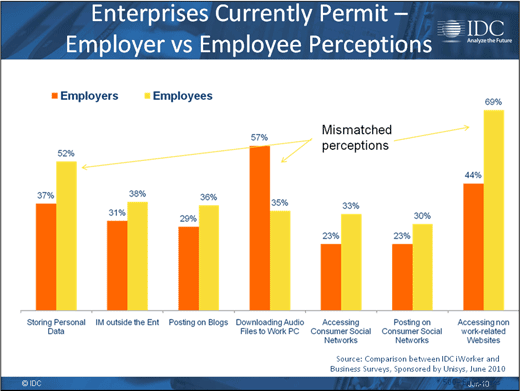
The business thinks it’s disallowing more activity than users realize.
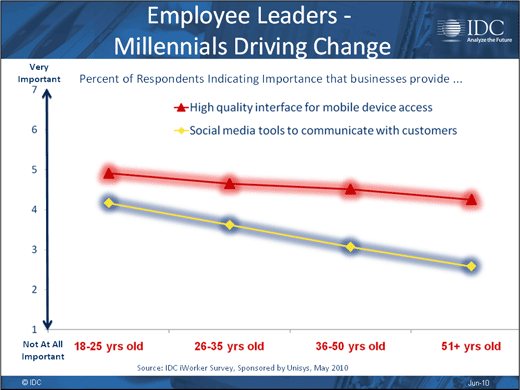
Younger workers are changing the way we all work.
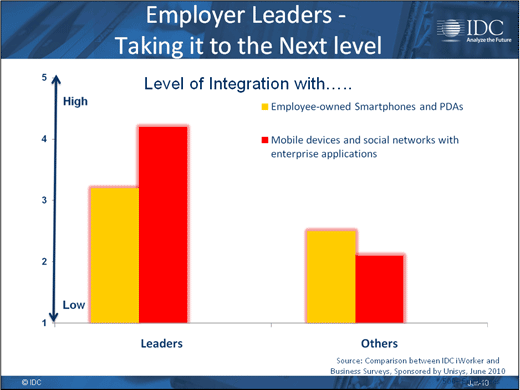
Everybody sees where this is all heading.
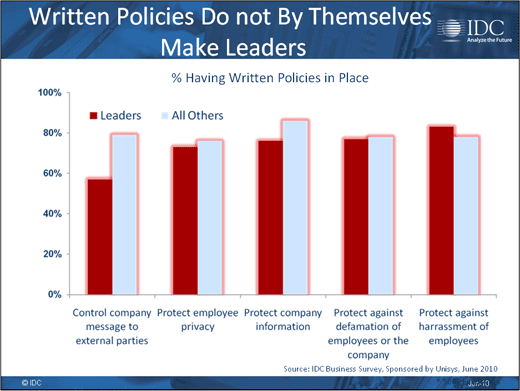
Words without actions are empty.
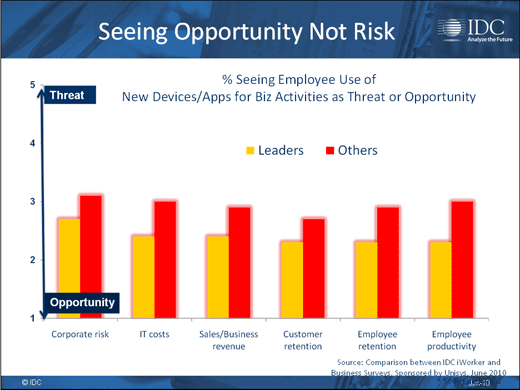
Many times IT organizations don’t want to know.

 While there may have been a time when IT organizations could dictate which devices and applications end users could use, employees are increasingly spending their own money to not only buy devices, but also contract to use software-as-a-service applications. Of course, sometimes the definition of their own money is fluid. They may not be using the IT budget, but in many instances they are using budget dollars allocated to the business unit they work for.
While there may have been a time when IT organizations could dictate which devices and applications end users could use, employees are increasingly spending their own money to not only buy devices, but also contract to use software-as-a-service applications. Of course, sometimes the definition of their own money is fluid. They may not be using the IT budget, but in many instances they are using budget dollars allocated to the business unit they work for.
























