Managing endpoint security in the age of BYOD has become a major problem for IT organizations. Most of them do not have the security systems in place that can scale to handle a brave new world of computing where every employee has two or three devices that can randomly connect to the corporate network at […]
Managing endpoint security in the age of BYOD has become a major problem for IT organizations. Most of them do not have the security systems in place that can scale to handle a brave new world of computing where every employee has two or three devices that can randomly connect to the corporate network at any time.
To address that specific issue, Promisec has come up with an agentless approach to managing endpoint security that Promisec CEO Dan Ross says not only scales better, but can also quickly identify the presence of any unsanctioned applications such as Dropbox.com.
This week Promisec released an upgrade that not only adds support for Windows 8 and UNIX devices, but can also recognize fingerprint identification systems on mobile computing devices. In addition, the new release adds support for PCI DSS reports, with plans to incorporate support for HIPAA, SOX and other industry-standard formats.
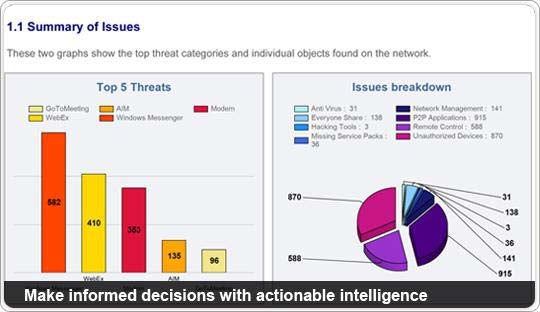
Ross says what differentiates Promisec most is the care the company took to eliminate false positives when it comes to generating security alerts. The company’s software performs a number of cross checks on the each system before issuing an alert, rather than just sending an alert based on when raw data exceeds one threshold or another.
With the rise of BYOD, organizations not only need security systems that scale, they need an approach that requires the least amount of intrusion possible on devices the organization may not own even though they are attached to the corporate network. By definition that would seem to require more dependency on an agentless approach that is not only easier to deploy, but just as importantly generates fewer false alarms that consume invaluable amounts of IT time.
MV
Michael Vizard is a seasoned IT journalist, with nearly 30 years of experience writing and editing about enterprise IT issues. He is a contributor to publications including Programmableweb, IT Business Edge, CIOinsight and UBM Tech. He formerly was editorial director for Ziff-Davis Enterprise, where he launched the company’s custom content division, and has also served as editor in chief for CRN and InfoWorld. He also has held editorial positions at PC Week, Computerworld and Digital Review.









