As we prepare for a new year, we often look at the things we have learned from the current year. 2014 may very well become known as the year of the data breach (that is, unless 2015 is bigger). From JPMorgan Chase to Target to Jimmy Johns to the most recent Sony hack, 2014 was the year that the state of data security was compromised.
While hackers have many points of entry – point-of-sale devices, phishing emails, malware, etc. – the long reach of mobile to mission-critical apps and data has exponentially increased the potential for a breach. According to Check Point Software Technologies, 47 percent of organizations have experienced a security breach as a result of a compromised mobile device, and Symantec estimates the average cost of a mobile incident at a staggering $429,000. In 2015, the situation will only get worse.
In this slideshow, Bluebox Security, a mobile data security company, has provided key stats from the year in mobile security, including major vulnerabilities, mobile security, spending and user behavior.
Mobile’s Wild West
Click through for a closer look at mobile security and the risk it poses to the enterprise, as identified by Bluebox Security.
Basic Security Failures
According to Gartner’s “Predictions 2014: Mobile Security Won’t Just Be About the Device,” 75 percent of mobile apps will fail basic security tests in 2015.
How Secure Are Your Mobile Apps?
Well, 75 percent don’t use proper encryption when storing data on a mobile device, 97 percent have access to private data without appropriate security measures, and 75 percent of mobile security breaches will be the result of exploiting poorly developed apps.
User Behavior
User behavior is a major cause for concern, and IT pros know it. According to a Check Point survey, 87 percent of IT pros worry about careless employees. Is it any surprise when mobile users in the U.S. lose an average of 113 smartphones per minute – yes, minute, download an average of 26 apps from the cloud, and 34 percent take no security measures whatsoever?
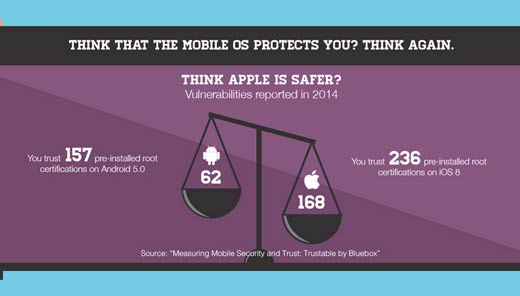
Protected OS? Think Again
Think Apple is safer? According to a Bluebox mobile vulnerabilities report, in 2014 Apple outpaced Android vulnerabilities by a wide margin.
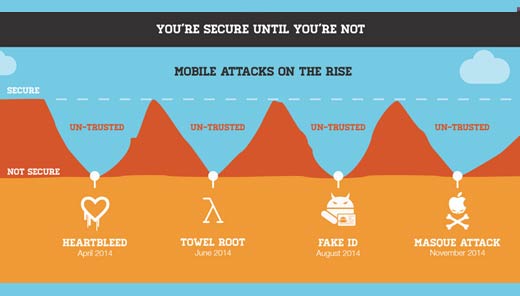
Mobile Attacks on the Rise
Mobile attacks continue to rise. This year alone, mobile users have faced major threats from Heartbleed, Towel Root, Fake ID and Masque Attack. It’s critical to ensure mobile data is protected and that proactive action is taken when threats emerge.