Data Lakes: 8 Enterprise Data Management Requirements When it comes to data management, there are two major challenges. The first is figuring out a way to cope with massive amounts of Big Data that are now routinely being sourced. The second is keeping track of where the organization’s most sensitive data is actually being stored. […]

Data Lakes: 8 Enterprise Data Management Requirements

When it comes to data management, there are two major challenges. The first is figuring out a way to cope with massive amounts of Big Data that are now routinely being sourced. The second is keeping track of where the organization’s most sensitive data is actually being stored.
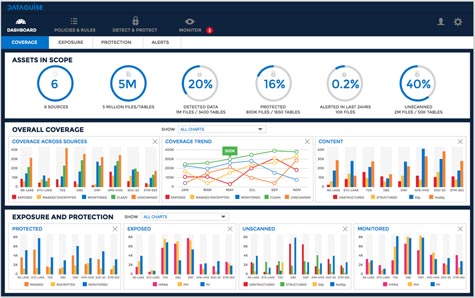
To address that latter issue, Dataguise has made available a Dataguise DgSecure Dashboard that enables IT administrators to keep track of where sensitive data is being stored regardless of the type of database being employed.
Venkat Subramanian, vice president of engineering for Dataguise, says thanks to the rise of more stringent regulations, IT organizations are now being held accountable for being able to identify and track where sensitive data is not only located at present, but also where it might have been at any given time.
Perhaps just as significantly, the Dataguise DgSecure Dashboard also captures metadata that can be invoked via an open application programming interface (API). Via that API, any number of third-party applications can discover and access critical enterprise data regardless of whether it’s stored in a relational database or a so-called NoSQL database.
Finally, Subramanian says Dataguise DgSecure provides a mechanism through which IT organizations can control who gets to access which data when inside the organization.
“Organizations are building these massive data lakes,” says Subramanian. “But people should only be able to access data that they directly manage.”
Of course, IT teams don’t always have a lot of clarity into who inside the organization should be allowed to access which data. That’s usually an exercise in data governance that requires the participation of individual business units. But in terms of enforcing those policies at a time when employees have access to more data than ever, it’s clear IT organizations need a more centralized approach that can be applied to as many data sources as possible.
Save
Save
Save
MV
Michael Vizard is a seasoned IT journalist, with nearly 30 years of experience writing and editing about enterprise IT issues. He is a contributor to publications including Programmableweb, IT Business Edge, CIOinsight and UBM Tech. He formerly was editorial director for Ziff-Davis Enterprise, where he launched the company’s custom content division, and has also served as editor in chief for CRN and InfoWorld. He also has held editorial positions at PC Week, Computerworld and Digital Review.








