How the Data Center Will Grow Up in Three Years With more enterprise IT organizations relying on software-as-a-service (SaaS) applications than ever, securing the data that flows in and out of those applications has become a major challenge and concern. To give IT organizations more control over that data, Protegrity today unveiled the Protegrity Cloud […]

How the Data Center Will Grow Up in Three Years

With more enterprise IT organizations relying on software-as-a-service (SaaS) applications than ever, securing the data that flows in and out of those applications has become a major challenge and concern.
To give IT organizations more control over that data, Protegrity today unveiled the Protegrity Cloud Gateway, a virtual appliance that, once deployed on a server, enables organizations to apply policies to the flow of data moving in and out of multiple SaaS applications.
Protegrity CEO Suni Munshani says it applies a mix of encryption and vaultless tokenization to make sure data residing in a SaaS application can only be viewed by users that have been given explicit rights to see that data. Those rights are assigned using a “configuration-over-programming” (CoP) methodology that allows administrators to configure the gateway without having programming skills.
Support for SaaS applications is provided by accessing the public application programming interfaces (APIs) those applications expose, with support for each additional SaaS application that Protegrity supports taking a few days or weeks to add, depending on the complexity of the project.
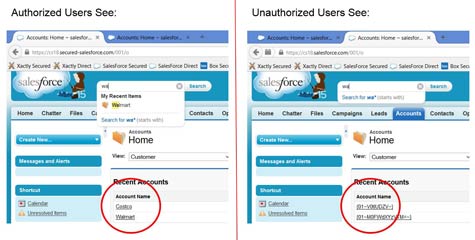
The Protegrity Cloud Gateway is based on a stateless architecture that enables the gateway to scale up on a server or scale out across multiple servers.
With enterprise IT organizations now building complex business processes that span multiple SaaS applications, finding a way to both manage and secure data as it flows across those applications is a major security and compliance headache. More challenging still is finding a way to apply those controls without actually compromising the performance of those applications.
MV
Michael Vizard is a seasoned IT journalist, with nearly 30 years of experience writing and editing about enterprise IT issues. He is a contributor to publications including Programmableweb, IT Business Edge, CIOinsight and UBM Tech. He formerly was editorial director for Ziff-Davis Enterprise, where he launched the company’s custom content division, and has also served as editor in chief for CRN and InfoWorld. He also has held editorial positions at PC Week, Computerworld and Digital Review.