Today’s threat landscape offers attackers a much larger selection of attack points in the form of open firewall ports for business traffic, Web or other servers behind the firewall, along with all applications running internally on the network, including PCs and servers. This gives the bad guys a wealth of attack methods to find vulnerabilities in your network. Attackers even have applications that take all the difficulty out of hacking into your network. These programs can be used to run high-speed automated attacks that were unthinkable a few years ago.
External threats are now the minority attack method. Attacks targeting internal systems are more lucrative financially and more effective than external attacks. Spam, phishing, social engineering, malware, Trojans, portable media devices, and other methods are commonly used to compromise systems while completely subverting traditional security solutions such as firewalls, intrusion detection systems, and even previous external vulnerability scans.
Bottom line: It is easy to be a hacker, and hard to stay ahead of them. One silver lining is that many of these attack methods rely on the system being vulnerable in some way. A lot of attacks are looking for weaknesses or misconfigurations in browser and Web applications. Malicious websites, whether used in conjunction with spam, phishing, search engine manipulation or any of several other attack types, often require a vulnerable system in order for the hackers to be successful. Identifying and remediating these vulnerabilities becomes one of the methods we can use to stay ahead of criminals.
Here, Perimeter Chief Architect Kevin Prince offers up eight steps you should take to protect your organization.
You can check out other slideshows from Perimeter: Data Breach Trends of 2009, Tracking Data Breaches by Incident, and Top Security Threats for 2010.
Click through for 8 essential elements to help reduce your vulnerability to hackers.
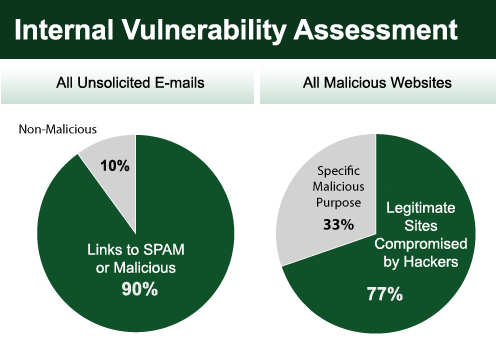
A vulnerability scan is the process used to identify exploitable operating systems, services and applications. This is primarily done by taking a database of scripts that can detect known vulnerabilities and running those scripts against systems. The result is a report that enumerates which systems are vulnerable, in what way they are vulnerable, and the criticality of the vulnerability. These scan reports are known as a vulnerability assessment report. Scans run against Internet-accessible devices are known as External Vulnerability Assessments (VAs), while scans run against systems on the inside of the network are known as Internal Vulnerability Assessments.
External VAs have always been considered the most critical because Internet-accessible devices such as firewalls, Web servers, e-mail servers, and so forth are most exposed to attackers. These systems also typically expose the ports and services where most vulnerabilities have been discovered, namely port 25, which e-mail runs on, and port 80, where Web sites are hosulted.
According to a University of Maryland study, systems accessible to the Internet are scanned by hackers for vulnerabilities on average every 38 seconds. Many of these scans could result in the compromise of vulnerable systems. Vulnerability scanning from hackers happens so frequently, and from so many different sources (often other compromised systems), that it is impossible to react to these attacks. Most IT administrators view this type of malicious traffic as background noise.
As companies attempt to offer their customers more services and establish partner and trade relationships, all in an effort to stay competitive, they have been forced to open more ports on their firewalls and expose access to more systems to the outside world. As a result, more chinks in the armor can be exploited.
Hackers have also developed methods of compromising the vulnerabilities that exist on systems that reside on the internal network. These attacks are usually a combination of a type of social engineering and malware. For example, a website hosted by a hacker has malicious software loaded on it. The hacker lures a user out to their site through any number of methods including pharming, phishing, search engine manipulation, redirection techniques and more. A vulnerable system that simply accesses that website can be compromised by Trojan horse-type software without the user ever knowing. This attack can also be done with popular websites that have been infected with malware, such as MSNBC.com, ZDNet.com, history.com or Walmart.com.
Internal threats don’t just come from malicious or compromised sites either. Worms spreading via mobile device, e-mail viruses, infected USB drives, and many other threats rely on systems being vulnerable for attack.
With attackers stepping up the frequency of their external scans, organizations need to test more frequently for vulnerabilities than they have in the past. Historically, organizations would run external vulnerability assessments either quarterly or annually. With the rate at which new vulnerabilities are discovered and how quickly hackers use them against targets, a 3- to 12-month period between tests is far too long. It is recommended that vulnerability scans be run weekly for optimum security, and monthly for at least best practice. Organizations should be allowed to purchase VA services that offer unlimited scanning ability for the optimal security. Otherwise, you run the risk of spending more money than the benefit the service will provide. Internal scans can be run less frequently than external scans. Optimal security suggests monthly and best practices would be quarterly.
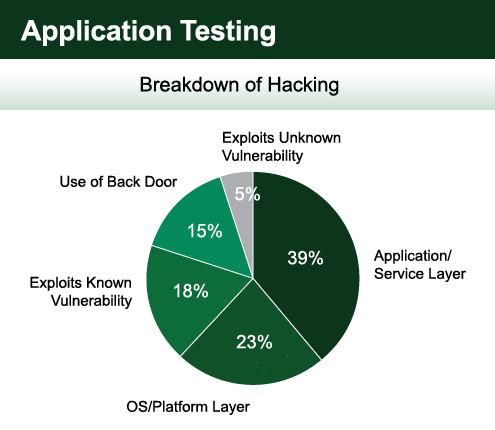
Traditional scanning of operating systems, ports and basic services is no longer adequate. Attackers have moved upstream in their attacks and now often exploit applications that are running on these systems. For example, for a financial institution, rather than compromising the Microsoft 2007 server, or the IIS version 6.0 Web software, they may attack the online banking software. The trick for criminals is that there are a limited number of operating systems and common services, but applications are plentiful. Many applications have not gone through serious (if any) code review or security analysis and often have common programming flaws that can be exploited. The attackers then use Google or another search to find other companies that use the same or similar flawed software that they can compromise.
Extensive application testing usually requires more than your standard external or internal vulnerability assessment. This should be consulting engagements where more sophisticated software is used along with limited access granted to systems so thorough testing may be performed.
Another recommended step beyond scanning internal systems for vulnerabilities is to check those same systems for their adherence to security policy, procedures and best practices. Policy scanning goes beyond vulnerability scanning and connects to each system and performs a review of system settings, administrative access, system integrity and password settings. IT administrators can determine which systems are not conforming to best security practices and outlined policies. One example might be how many systems still have the default password of ‘password’ or ‘admin’ on the network.
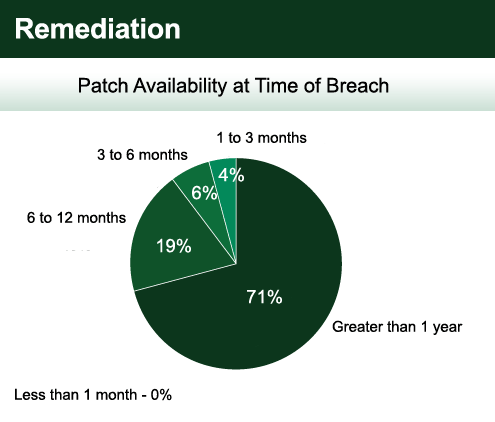
Internal and external assessments along with policy scanning are all about giving valuable information to the IT administrator, who can then remediate identified security weaknesses. Some believe that with a patch management solution, there is no need for vulnerability scanning. Patch management is the most common way of fixing identified vulnerabilities, but it isn’t the only way. Identified vulnerabilities may be caused by misconfigurations or the natural outcome of doing business a particular way. Only about half of discovered vulnerabilities can be remediated through a patch management solution. That leaves 50 percent or more vulnerabilities still being a concern for you. Additionally, vulnerabilities may be discovered long before a patch or fix is available. While it may be difficult to protect systems against these 0-Day attacks, knowing they exist offers IT administrators the foreknowledge to add other security layers to protect vulnerable systems.
When using a patch management system, be sure you are updating all operating systems that you use in your network, as well as any third-party applications installed on your systems. Most organizations do a good job of keeping Microsoft operating systems and applications up to date, but don’t fare nearly as well when it comes to Linux, UNIX, Mac, and third-party applications such as Adobe. This is often due to the use of Microsoft’s system update service (SUS), which is the free Microsoft patching program. It only offers updates to Microsoft applications and operating systems and leaves all others exposed and vulnerable to exploit.
Misconfigurations of systems, servers and firewalls also lead to the compromise of networks. Vulnerability assessments can help identify some of these configuration problems. Qualified security and IT experts should be making changes to systems as needed to ensure existing vulnerabilities can be filled and new weaknesses are not exposed. This is one major advantage of using a third-party provider for security services. Providers can use economies of scale to have qualified security engineers apply their skills across many customers rather than each individual company having to maintain this level of security expertise in house.