Top Barriers to Effective Vulnerability Risk Management Taking the whole concept of data security to its most logical conclusion, Secure Islands has come up with a method that automates the application of security to any piece of data, depending on how it’s classified, as that data is being generated. Secure Islands CEO Aki Eldar says […]

Top Barriers to Effective Vulnerability Risk Management

Taking the whole concept of data security to its most logical conclusion, Secure Islands has come up with a method that automates the application of security to any piece of data, depending on how it’s classified, as that data is being generated.
Secure Islands CEO Aki Eldar says version 5.0 of the IQProtector Suite (IQP) adds what the company describes as a Data Immunization process. IQProtector automatically assigns security controls to data at the point that data is actually created, regardless of location. Those controls then attach themselves to that data wherever it is consumed.
Based on rights management technology developed by Microsoft, Secure Islands has different renditions of IQProtector for endpoints, servers, clouds and applications to make sure that wherever data is created, a security policy gets enforced.
Historically, Eldar says IT security professionals have been chasing their tails. Massive amounts of data are created every day. Sometime after that data is created, IT security professionals are then expected to assign and apply security controls. IQProtector is designed to allow IT organizations to assign security policies to various classes of data that are then automatically applied any time that type of data gets created. As part of those policies, the IT organization is determining who has permissions to actually view that data once it is created, regardless of where that data travels, says Eldar.
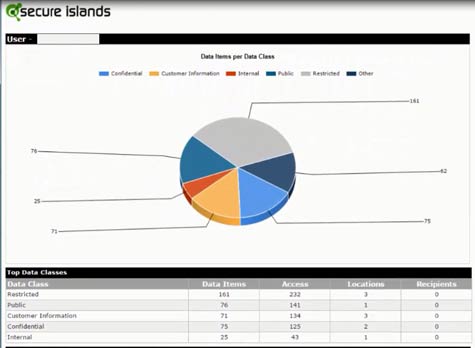
In the wake of several high-profile data security breaches, it’s clear that the IT security focus is finally shifting from mainly trying to defend a network perimeter to securing enterprise data itself. The challenge from an IT security perspective, of course, is finding a way to keep up with all the data being generated that enables data security policies to be enforced before digital criminals even know the data exists.
MV
Michael Vizard is a seasoned IT journalist, with nearly 30 years of experience writing and editing about enterprise IT issues. He is a contributor to publications including Programmableweb, IT Business Edge, CIOinsight and UBM Tech. He formerly was editorial director for Ziff-Davis Enterprise, where he launched the company’s custom content division, and has also served as editor in chief for CRN and InfoWorld. He also has held editorial positions at PC Week, Computerworld and Digital Review.










