One of the dirty little IT secrets that most organizations prefer not to talk too much about is the lack of visibility and control they have over who can share what information via any specific means. The proliferation of cloud-based communications and content repository services makes it a trivial matter for end users to share […]
One of the dirty little IT secrets that most organizations prefer not to talk too much about is the lack of visibility and control they have over who can share what information via any specific means. The proliferation of cloud-based communications and content repository services makes it a trivial matter for end users to share even the most sensitive of documents.
To make it possible to apply some governance and control over those communications channels, Egnyte today unfurled Egnyte Protect, a cloud-based service that applies both machine and deep learning algorithms in real time to classify content residing in multiple public and private repositories. Based on the classification of those documents, Rajesh Ram, chief customer officer for Egnyte, says Egnyte Protect generates an alert any time there is any unusual activity involving an organization’s most sensitive documents.
“We can identify what is in those documents and where it is,” says Ram. “That gives companies a single unified view of their risk.”
Egnyte initially developed a file and synchronization service that works across multiple storage systems. Egnyte Protect, says Ram, extends the reach of the company’s core technologies into the most widely used content repositories, which Ram says Egnyte will continue to expand the number of based on customer demand.
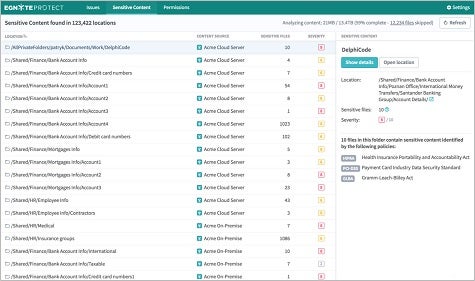
At a time when intellectual property worth billions of dollars is regularly being pilfered either by cybercriminals or trusted insiders, organizations of all sizes have a pressing need to be able to identify what content is being accessed by whom. But the biggest threat most organizations need to combat today is not some malevolent force bent on its destruction. Rather, it’s the carelessness of employees who, in the name of productivity, try to circumvent a secure means of communications simply because they find it cumbersome to use.
Of course, most IT organizations naturally have policies about when and how those alternative communications channels can be employed. But without some form of visibility into and control over those channels, most of those policies are not worth the paper they were printed on.
MV
Michael Vizard is a seasoned IT journalist, with nearly 30 years of experience writing and editing about enterprise IT issues. He is a contributor to publications including Programmableweb, IT Business Edge, CIOinsight and UBM Tech. He formerly was editorial director for Ziff-Davis Enterprise, where he launched the company’s custom content division, and has also served as editor in chief for CRN and InfoWorld. He also has held editorial positions at PC Week, Computerworld and Digital Review.









