Not all data is created equal so when it comes to IT security, there’s a need to prioritize levels of risk. There’s certainly value in being able to search a Big Data repository to identify anomalies. But often it’s more important to know of any potential threats targeting specific types of high-value data such as […]
Not all data is created equal so when it comes to IT security, there’s a need to prioritize levels of risk. There’s certainly value in being able to search a Big Data repository to identify anomalies. But often it’s more important to know of any potential threats targeting specific types of high-value data such as credit card numbers or any form of personally identifiable information.
With that issue in mind, CSPi, a provider of managed security services, has developed a Myricom nVoy Series 10Gbit Packet Recorder and Myricom nVoy Series 1-100Gbit Packet Broker that allows organizations to monitor who is accessing specific types of data.
Gary Southwell, general manager of Myricom business at CSPi, says the Myricom appliances come with a built-in indexing engine that in many instances will eliminate the need for a dedicated security information and event management (SIEM) platform.
“You just need to watch your most critical data,” says Southwell.
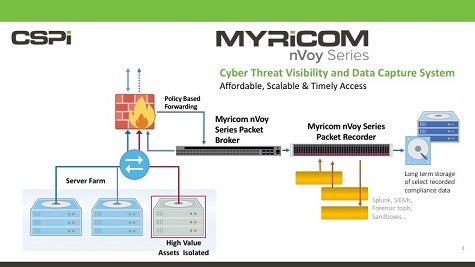
All the other data flows can then be passed on to a Big Data analytics platform such as Splunk to identify any anomalies that might signal an attack on less critical data.
The nVoy Packet Broker, meanwhile, makes it possible to aggregate, replicate, tag, strip, filter and load-balance network traffic coming to or from any port on the appliance.
They say to defend everything is to defend nothing. Given the sheer size of the attack surface that needs to be defended within most organizations, there’ a pretty clear need to defend some classes of data more than others, especially when any compromise of that data might lead to fines and penalties being levied by a regulatory body. The real challenge is to make sure that the organization’s most sensitive data isn’t being accessed by someone or some entity that shouldn’t have access to that data in the first place.
MV
Michael Vizard is a seasoned IT journalist, with nearly 30 years of experience writing and editing about enterprise IT issues. He is a contributor to publications including Programmableweb, IT Business Edge, CIOinsight and UBM Tech. He formerly was editorial director for Ziff-Davis Enterprise, where he launched the company’s custom content division, and has also served as editor in chief for CRN and InfoWorld. He also has held editorial positions at PC Week, Computerworld and Digital Review.