Everyone intuitively knows that applications have become the primary target of cyber criminals around the globe, but it’s another thing to see confirmation of it.
Cisco this week released the latest edition of its Global Security Threat report. Beyond identifying Kazakhstan as a major source of malware on the Web, the report clearly shows that a growing amount of malware is aimed as applications. In particular, Adobe Reader and Flash software are favored targets, while at the same time we’re seeing a surprising resurgence in SQL injection attacks.
According to Mary Landesman, a senior security researcher for Cisco, while there is an increasing number of sophisticated attacks being developed, cyber criminals prefer the path of least resistance, which in many cases means relatively rudimentary approaches to breaching application software.
The problem, says Landesman, is that with so much focus on network security at the perimeter, not enough attention is paid to securing application software. This issue stems from the fact that developers continue to think of security as an afterthought, while many internal IT organizations have yet to rethink their security posture in light of these threats.
As a result, Landesman says many IT organizations need to assess the value of various types of data within their organization in order to prioritize their security efforts. That’s especially important in the age of the borderless Web, she said, because every application out there in some form or another interacts with an externally focused application that is a primary target for hackers around the globe.
Unfortunately, as Windows and network infrastructure have become more secure, too many IT organizations have grown complacent about security at a time when cyber criminals are shifting their strategies to exploit long-standing application weaknesses.
Click through for results from a survey conducted by Cisco on the evolving security landscape.
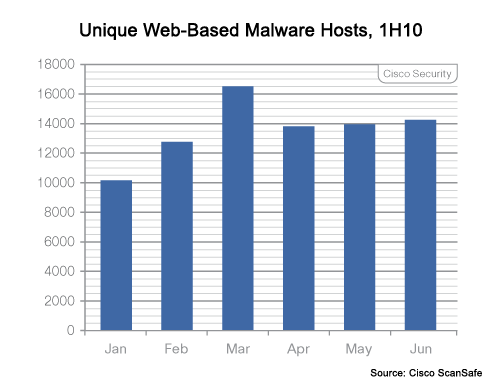
Malware hosts are holding steady.
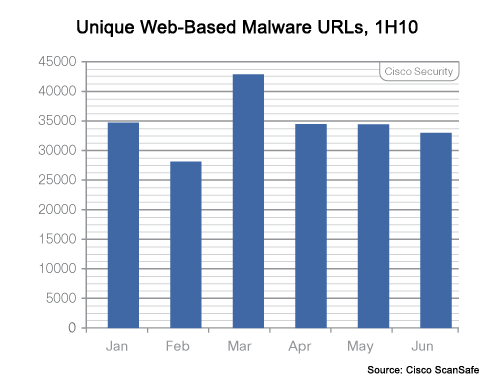
As are the number of URLs.
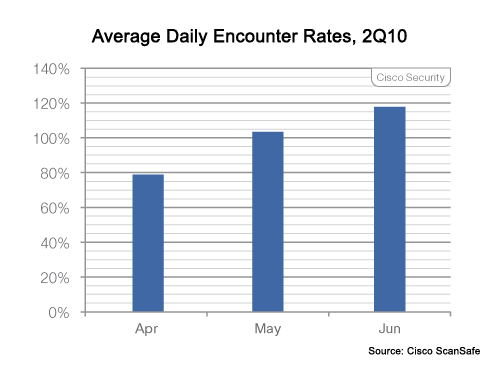
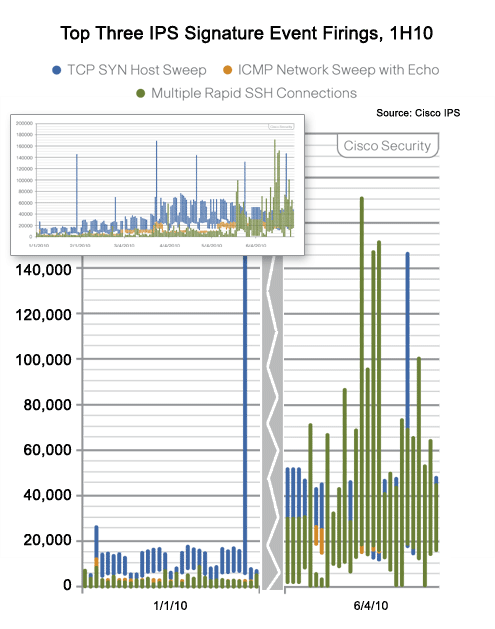
But the number of incidents is increasing.
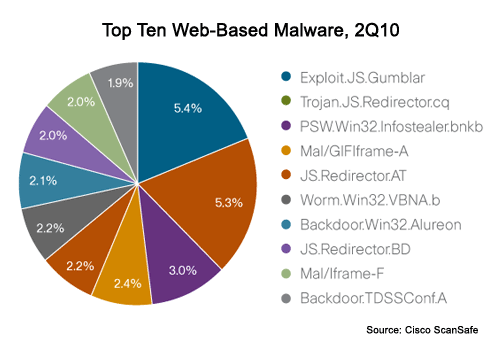
The threats are shifting to target applications.
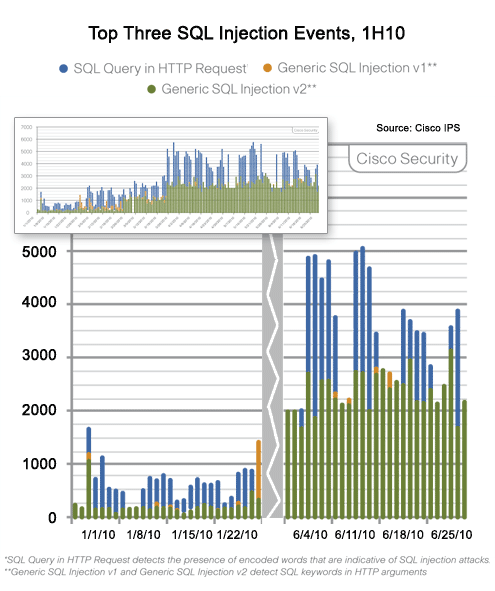
Surprisingly, SQL Injection attacks are on the rise again.
The rate of these attacks is increasing.
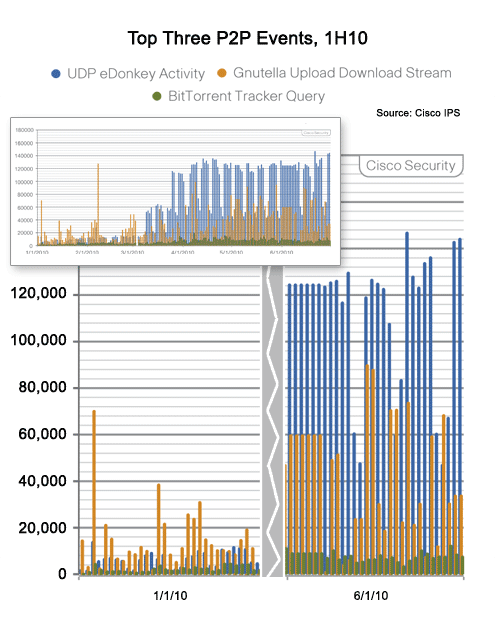
BitTorrent is no longer the worst offender.
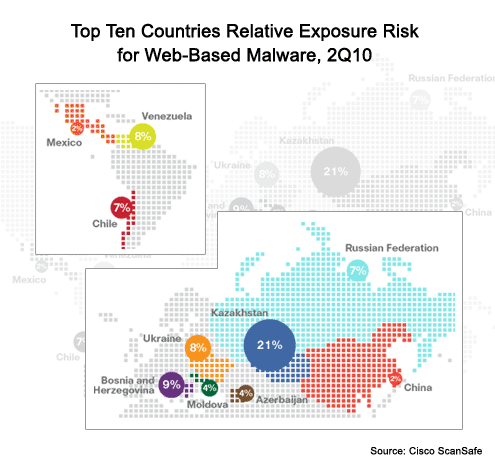
Kazakhstan is now at the top of the list.