A new survey of 583 IT and security practitioners that was conducted by The Ponemon Institute on behalf of Juniper Networks finds that not only are the number of actual security breaches increasing dramatically, IT organizations are losing confidence in their ability to deal with them.
Larry Ponemon, director of The Ponemon Institute, says the lack of confidence stems from three core issues facing IT today. The first is the rise of mobile computing, which is giving rise to more unprotected employee-owned devices being used to access corporate networks. The second is that as business processes continue to expand across the Internet, lax security at third-party business partners can easily lead to a security breach. And finally, the complexity of the overall IT environment makes it too hard to defend.
Karim Toubba, vice president of product marketing and strategy for the Security Business Unit at Juniper Networks, says the survey results show there is a clear need for a more holistic approach to security, which Juniper would argue needs to start at the network layer.
While vendors debate the merits of various approaches, it’s becoming increasingly clear that the IT security measures in place are not up to the task. They can typically defend against well-known, low-level attacks, but any targeted security attack has a reasonably high chance of being successful. The only thing that seems to be working to the advantage of many IT organizations is that there are so many potential targets, and hackers appear content to prey upon the weakest members of the enterprise IT herd.
Alas, that won’t be the case for much longer. We’ve already seen how corporations are now being targeted as part of a larger cyber war that crosses national boundaries. More often than not, the targets of those attacks are intellectual property in the hands of private corporations.
It may take a major international event that will push governments to require corporate entities to put more stringent security measures in place. But at the moment, it seems like IT organizations are being left to their own devices when it comes to defending their organizations from cyber criminals who appear to be getting more organized and sophisticated with each passing day.
Click through for results from a security survey conducted by Juniper Networks and the Ponemon Institute.
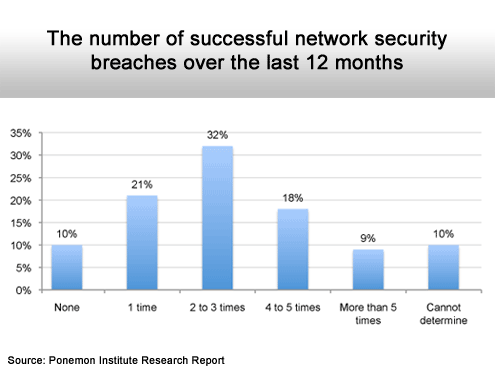
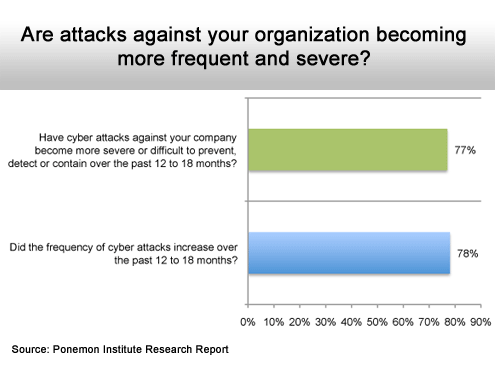
It’s becoming more common.
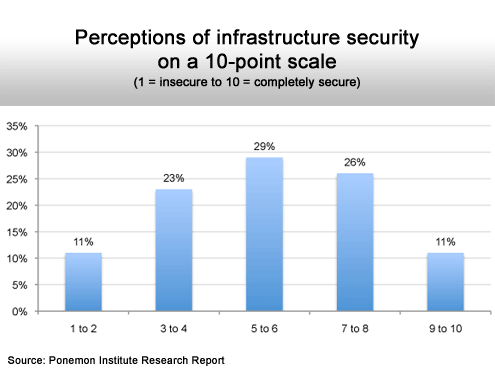
Most everybody is in the middle of the pack.
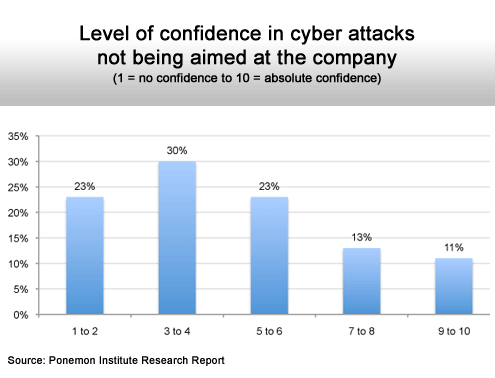
This is a rising concern.
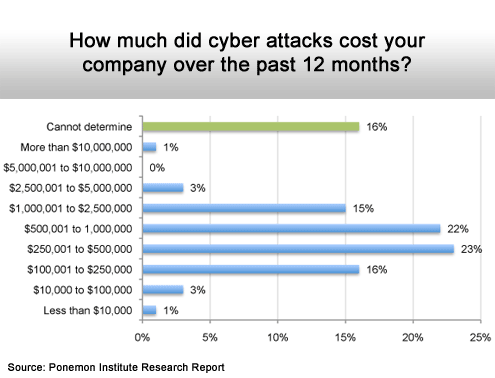
Starting to really hurt.
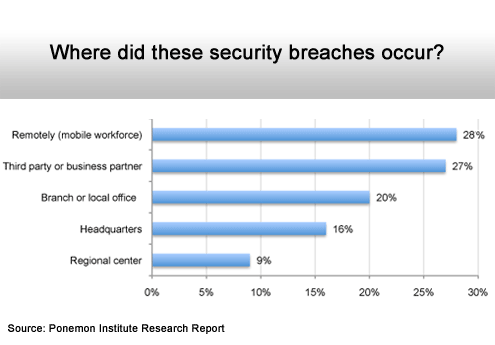
Remote networks and third-party connections are the biggest issues.
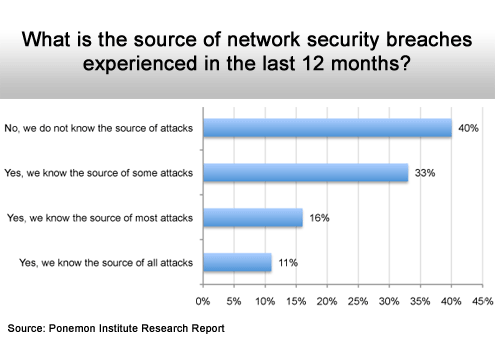
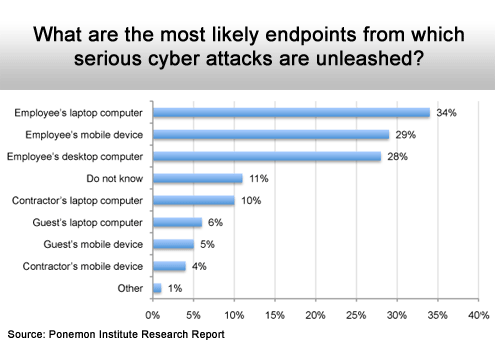
Hard to fight what you can’t see.
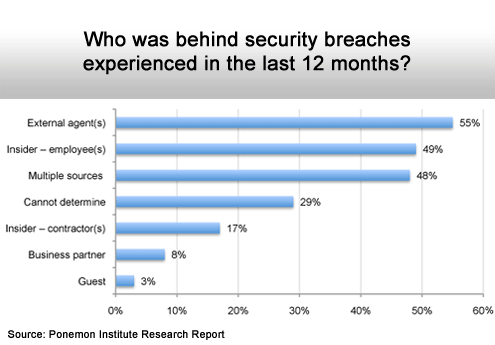
Threats are everywhere.
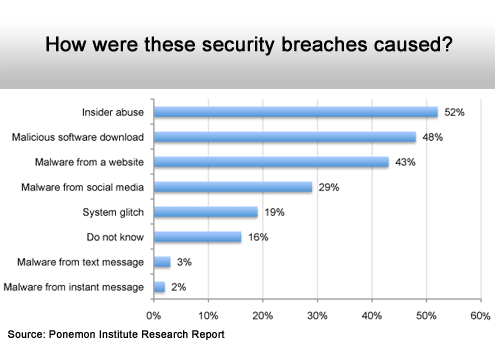
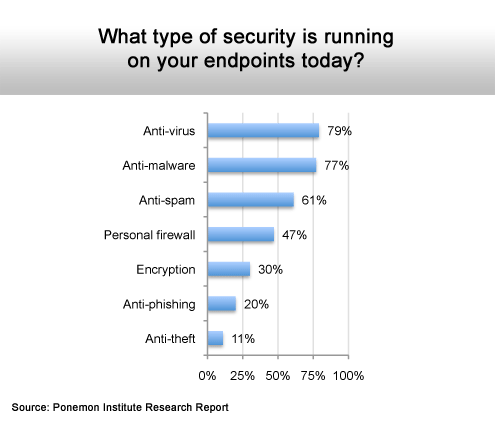
Malware still dominates overall.
Mobile computing devices are easy to compromise.
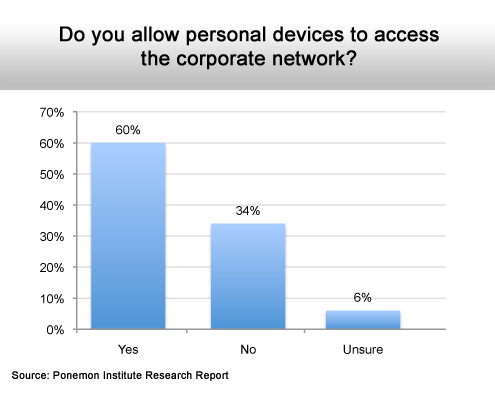
Most do, despite security issues.
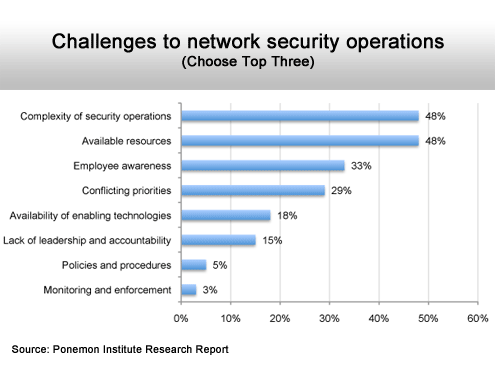
Complexity and available resources top the list.
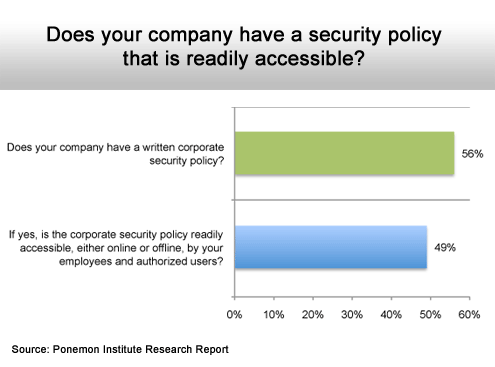
A little more than half do.
Definitely heading in the wrong direction.
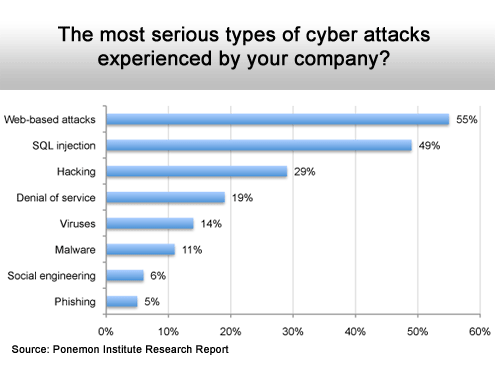
Web-based attacks followed by SQL Injections top the list.
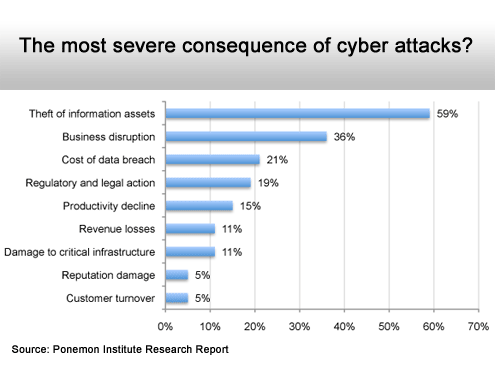
Intellectual property is now the primary target.
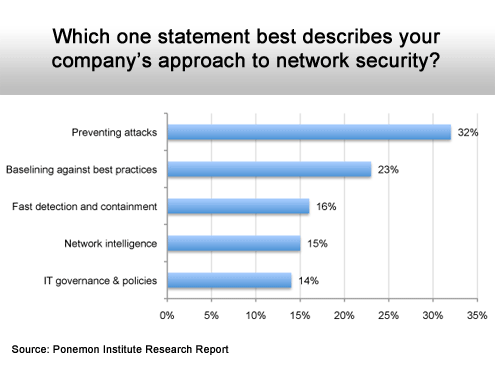
Prevention is worth a pound of cure.
The end run around the firewall.
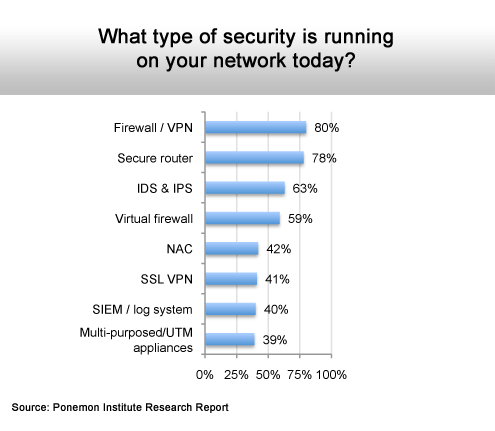
Most rely on the basics.