A new survey from The Ponemon Institute that was funded by Aveksa, a provider of data governance tools, clearly highlights this issue in a survey of 728 IT executives that finds that a huge percentage of employees have access to information they don’t need for their roles in the company, thus introducing unnecessary risks in terms of how that data can either be accidentally or purposely compromised. (Be sure to check out our Mike Vizard’s deeper look at the survey.)
In general, the survey also finds that the majority of IT organizations are understaffed in the number of people they have on hand to manage data governance, while the number of sensitive documents and the requests to access that information appear to be increasing exponentially.
The good news is that progress is being made in some quarters concerning the adoption of more sophisticated tools for managing data governance, but Larry Ponemon, chairman of the The Ponemon Institute, warns that without a holistic approach to data governance that encompasses both the business side and the IT department, it’s only a matter of time before most companies experience a major security breach.
Click through for findings from a recent study conducted by the Ponemon Institute and sponsored by Aveksa.
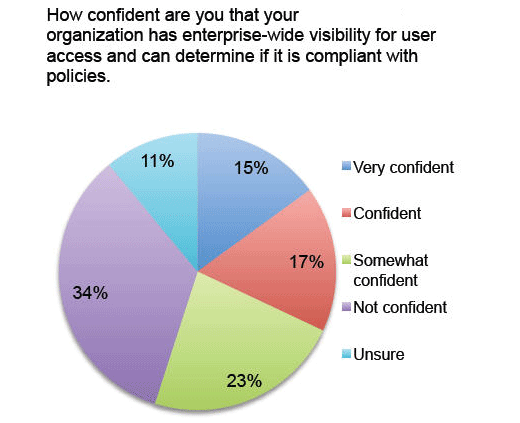
“Confidence levels are pretty shaky.”
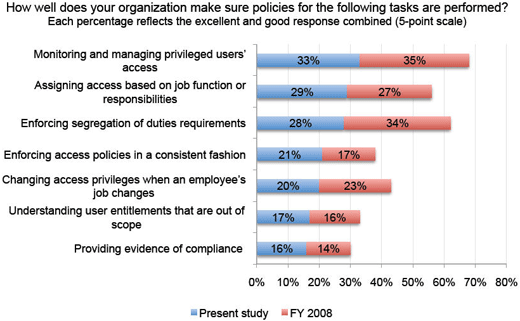
Not much improvement in the last two years.
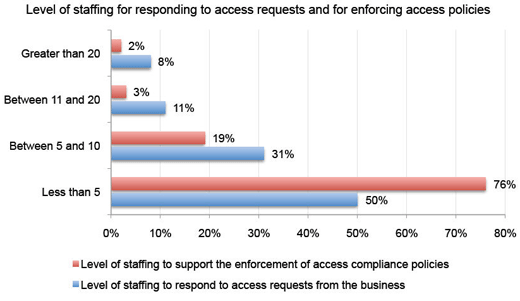
Throwing a few more bodies at the problem.
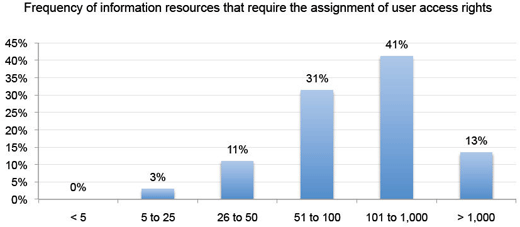
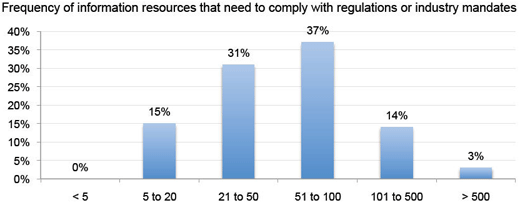
Most IT organizations are dealing with hundreds of information resources.
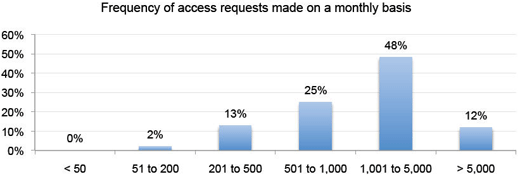
IT organizations spend a huge amount of time fielding routine requests for access.
And most of what people access is regulatory sensitive information.
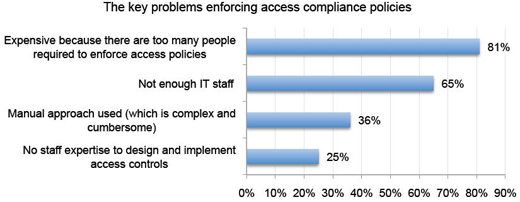
Too many people involved is the top issue.
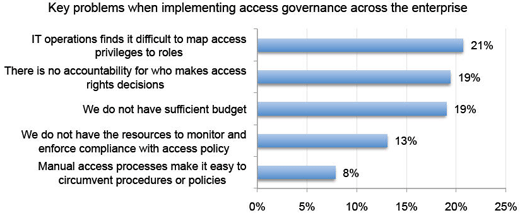
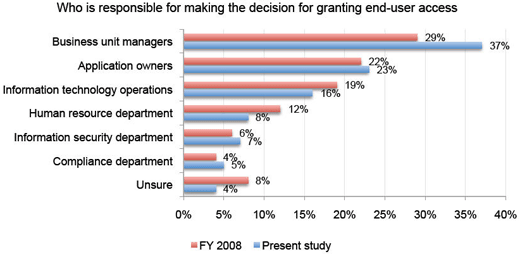
IT can’t be sure who should have access to what information.
Most people think this is an IT issue, when it’s really a business issue.
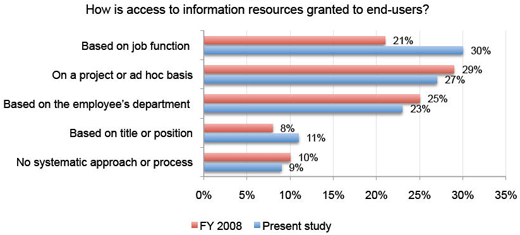
Job role is finally starting to be the defining characteristic.
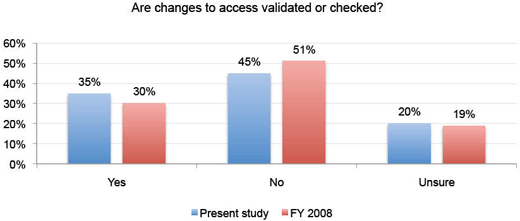
Not nearly as often as they should be.
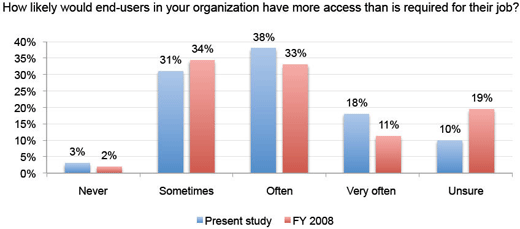
More often than not, this is the case.
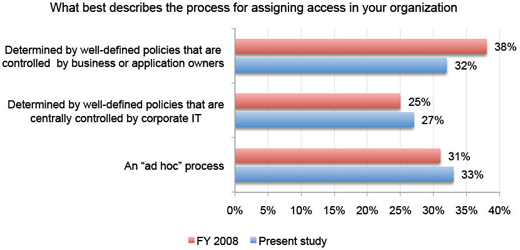
Processes are inconsistent across various organizations.
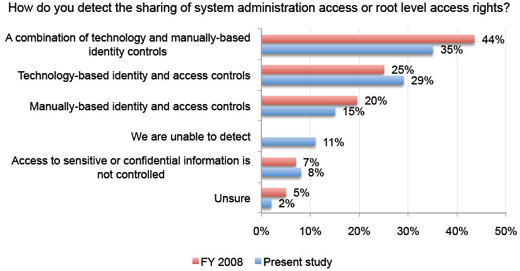
A mix of automated and manual processes.
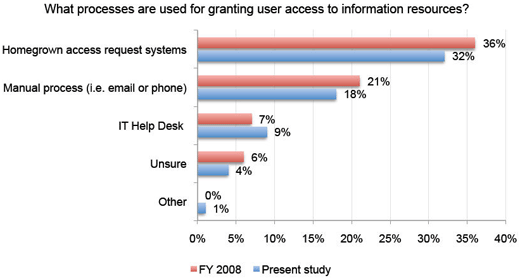
Homegrown systems dominate the IT landscape.
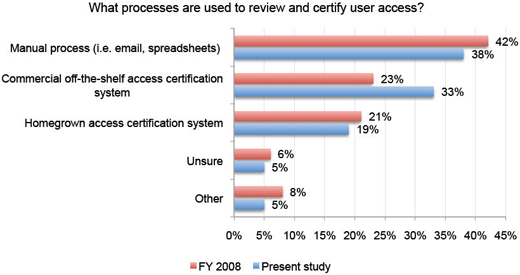
More automation is starting to be applied here.
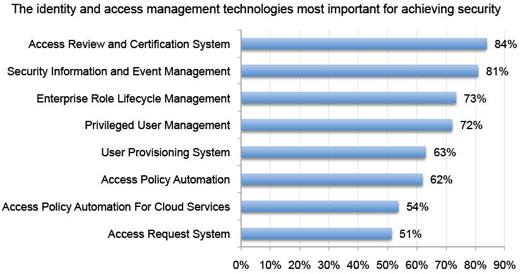
No one single technology provides a silver-bullet solution.
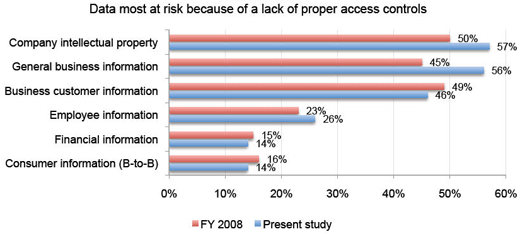
Intellectual property theft is feared most.
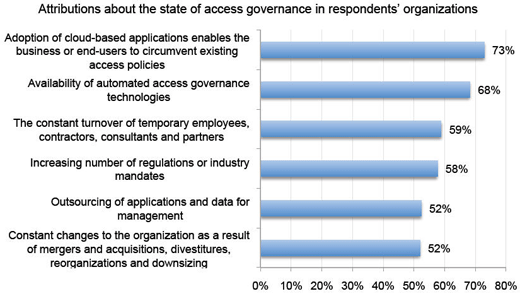
Cloud computing will present some real challenges.