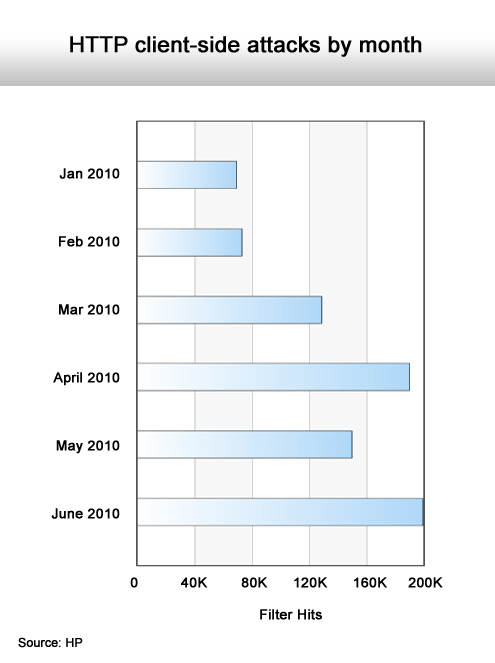While it's no surprise that systems on the Web are the primary targets for malware, it's troubling that attacks aimed at Apple QuickTime and Adobe Flash have tripled in the first six months of this year.
Those are the findings of a recent survey from Hewlett-Packard’s TippingPoint team, which came to HP in the recent acquisition of 3Com.
According to Mike Dausin, manager for advanced security intelligence for HP TippingPoint DVLabs, attacks not only are becoming more frequent, but more sophisticated as well. While the malware itself in many cases is “beautifully written,” the attacks themselves being aimed at software that is among the least secure on the Web.
This path-of-least-resistance approach is consistent with the history of malware. But now that Windows operating systems and network perimeters are generally more secure, malware distributors are simply moving on to the next easy targets.
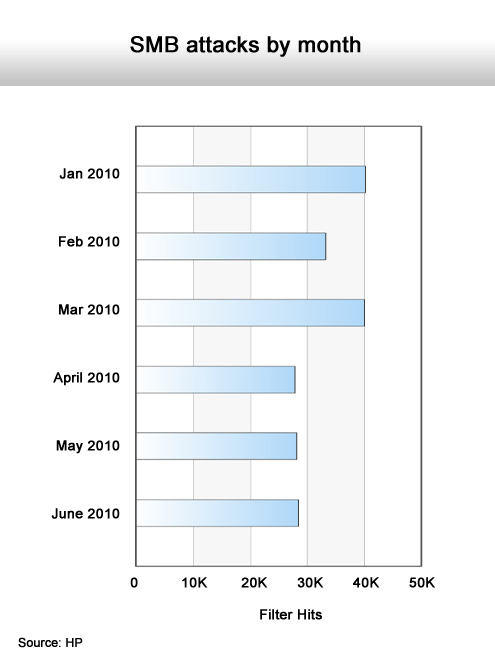
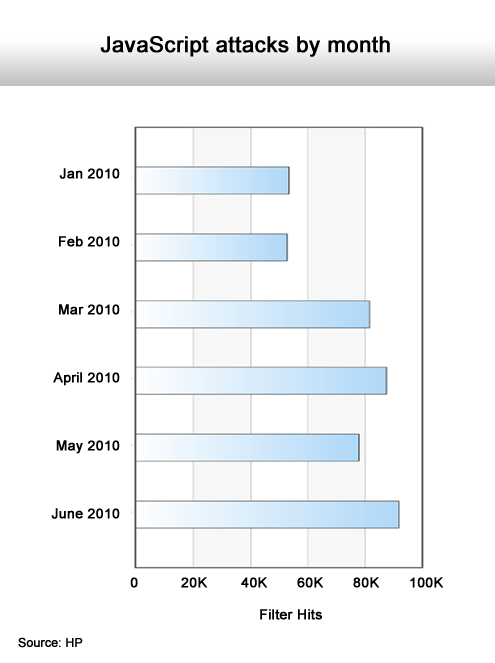
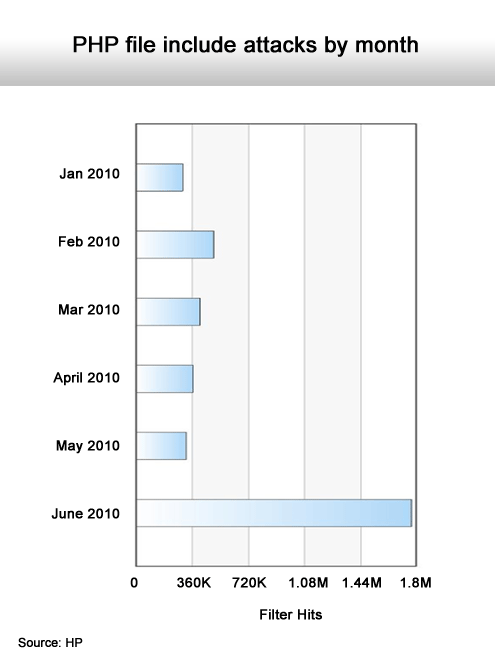
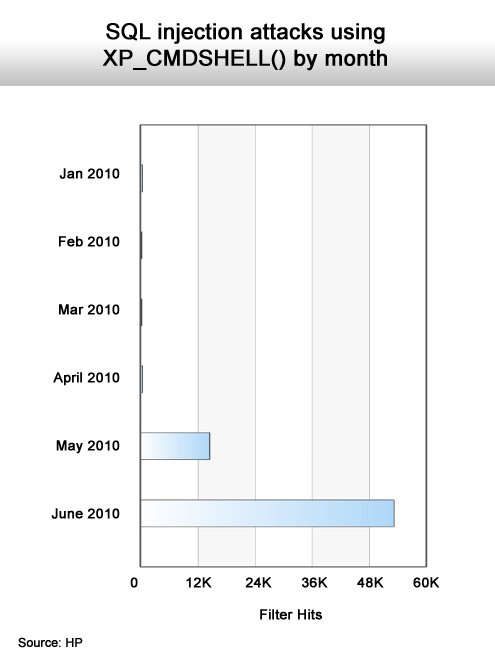
Dausin says HP has also documented a sharp rise in JavaScript and PHP File attacks and that older attacks, such as SQL Injections, are making a comeback.
HP highly recommends that IT organizations make sure they are running the latest version of common Web applications, such as version 9 of Adobe Reader, that are inherently more secure.
But dealing with these attacks effectively will require more resources to be allocated to application security. In many cases, that may mean consolidating network perimeter security appliances to save money that can be reallocated to application security. In other cases, it might mean allocating more of the applications budget to deal with security issues.
There may never be the perfectly secure Web application. But one thing that is for certain, if an IT organization makes it easy to compromise a Web application, in all probability it has already happened.
Click through for results from a security threat survey conducted by HP.
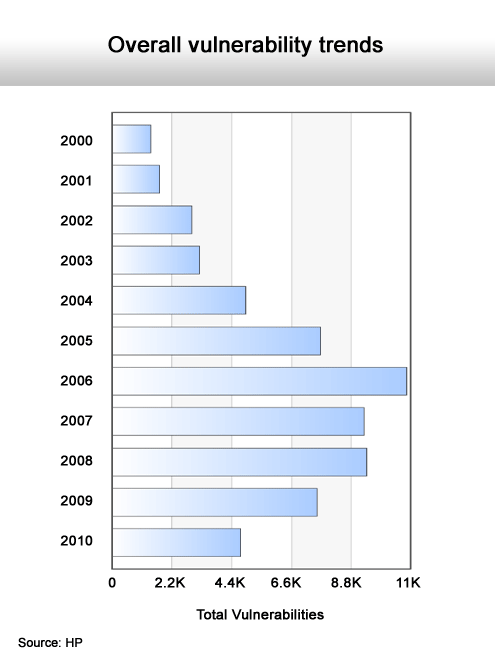
Web application vulnerabilities remain at a constant high level.
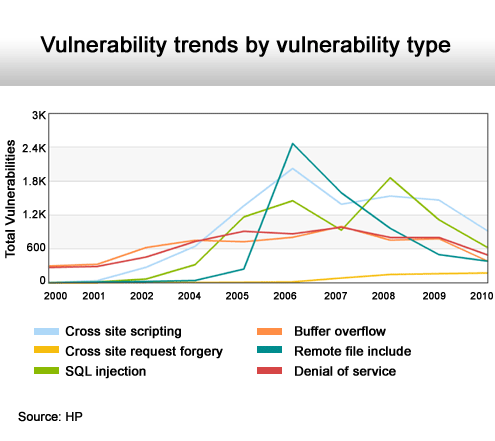
Cross-site request forgeries are rising.
The number of these instances is getting higher.
A rise after a period of marked improvement.
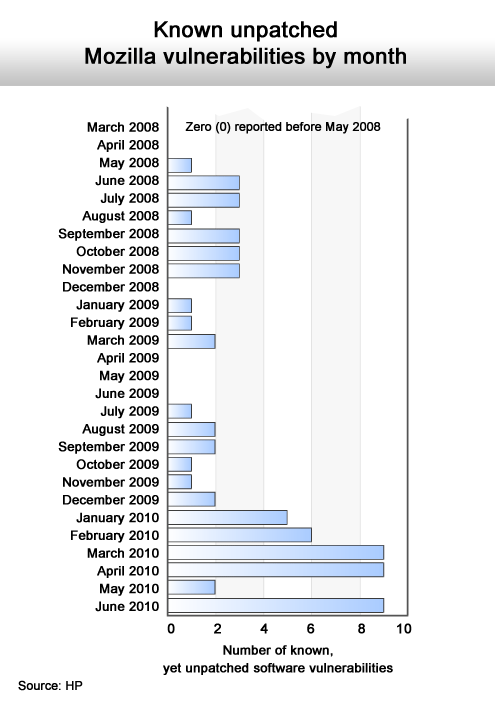
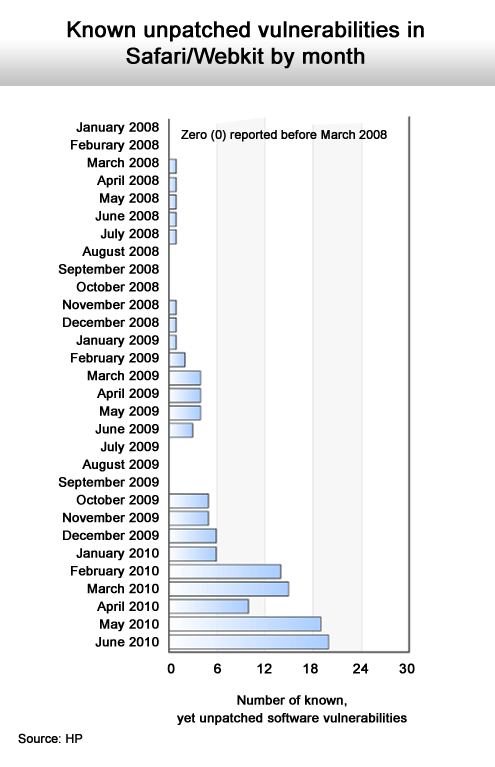
As Apple gains popularity, the number of known security issues rises.
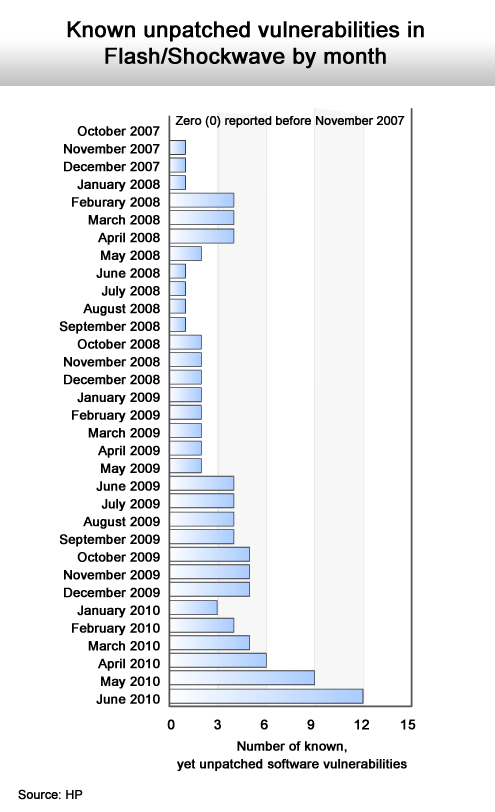
Adobe Flash is now a favorite target.
Another marked increase.
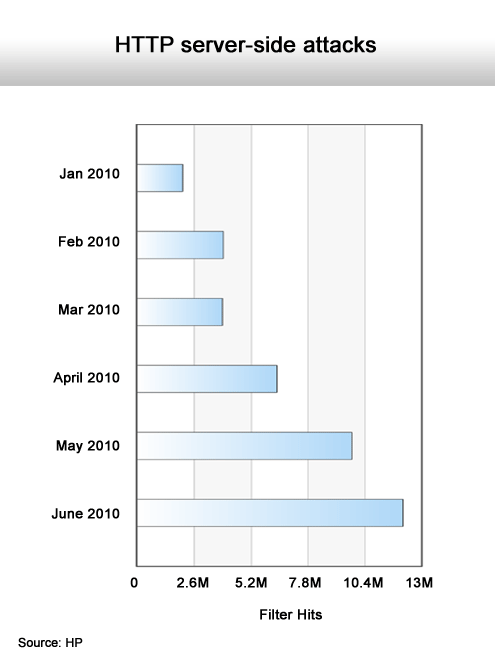
And a corresponding increase on the server side.
A noticeable decline.
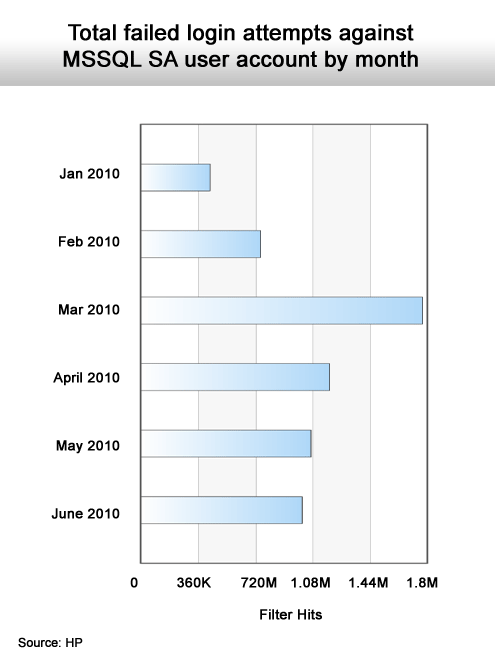
A definite rising trend.
A sharp rise in is this type of attack as well.
A sudden increase in an old method.
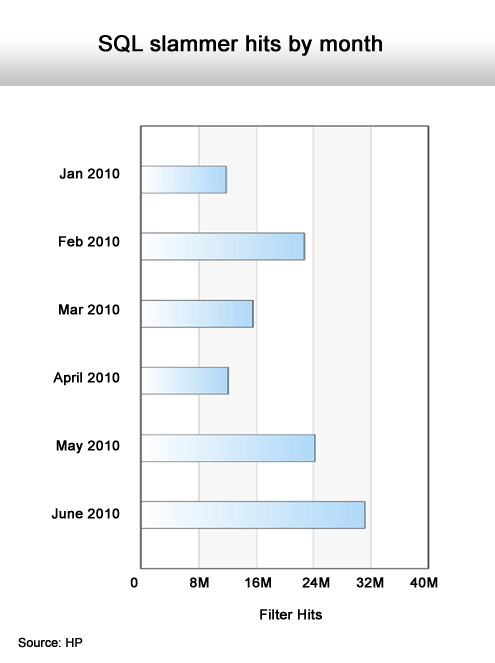
Another increase in SQL-based attacks.
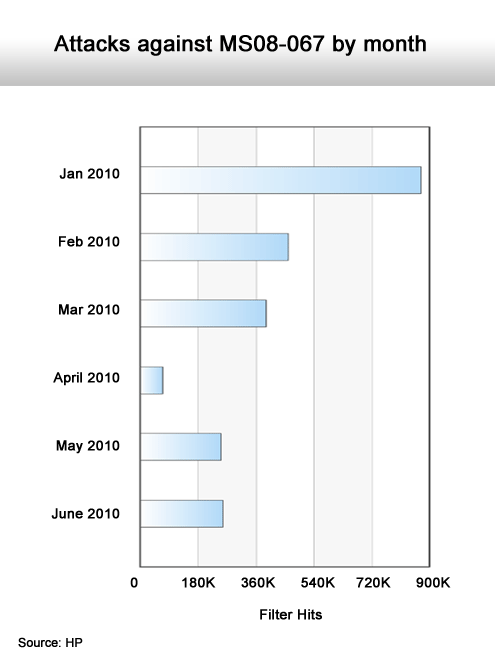
Used primarily by the Conficker worm.
A welcome decline.
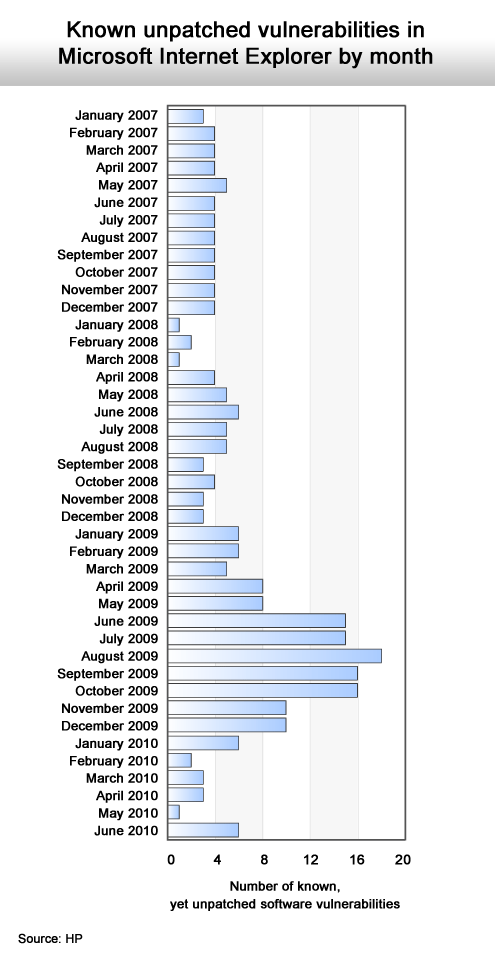
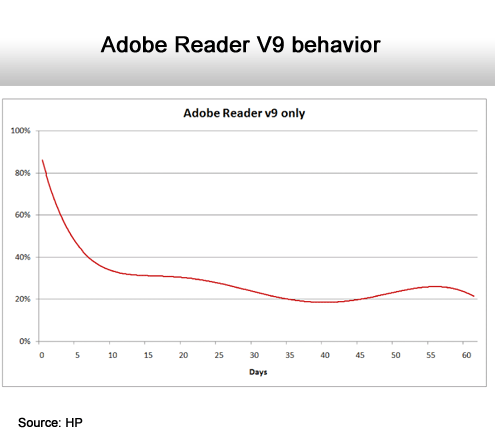
A major security improvement of previous versions.