Past cyber attacks and the tools used to carry them out have led to new breaches this year, according to key findings in a new mid-year cyber crime trend report just released by cyber threat intelligence provider SurfWatch Labs. In a study of events that occurred in the first half of 2016, the stockpile of personal information garnered from old data breaches led to new compromises and lucrative payoffs for cyber criminals.
While the diversity of cyber threats can seem overwhelming when viewed in isolation, when viewed collectively, they paint a picture of an increasingly connected cyber crime world. Malicious actors excel at taking one piece of information and leveraging it to perform additional attacks, gain more information, and widen their reach. The stories so far in 2016 clearly demonstrate this method and capability, with numerous cyber incidents tied to previous data breaches. The effects of cyber crime continue to ripple outwards – affecting those in the supply chain and beyond.
Motivations behind the attacks ranged by industry and predictably, not a single sector was left untouched by the unscrupulous actors. The new report does indicate that the familiar company response to a breach — “We were breached by a sophisticated attack but it has now been contained” — actually contradicts what has really happened so far this year. In truth, the majority of tactics used were not new or sophisticated.
To compile this report, SurfWatch Labs collected tens of thousands of cyber event activities from open and Dark Web sources and then normalized, categorized and analyzed the data for impact based on the CyberFact information model. Knowing the breakdown of industries targeted, the effects of attacks and the tactics criminals employed provides better insight into what the bad guys are up to. This translates into more informed forecasts of how cyber crime will impact organizations similar to yours and consequently, what to do to minimize your risk.
In this slideshow, Adam Meyer, chief security strategist, SurfWatch Labs, has highlighted key findings from the report.

Mid-Year Cyber Crime Report 2016
Click through for highlights from a report on cyber crime over the first half of 2016, as identified by SurfWatch Labs.
Top Industry Target: IT
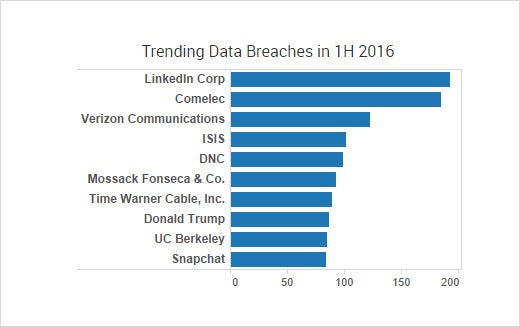
Information technology (IT) was the top targeted industry in the first half of 2016, accounting for 34 percent of all cyber crime chatter. That is an increase of four percent over last year. LinkedIn was the top trending cyber crime target across all categories, which stems from their 2012 data breach that, as announced in May of this year, actually impacted 100 million more users than originally thought. Reports continue to surface of secondary organizations now having their data stolen due to a combination of the LinkedIn breach, widespread user password reuse and remote access software from services such as GoToMyPC, LogMein and TeamViewer. Microsoft was another top trending target in the IT category, as was Android.
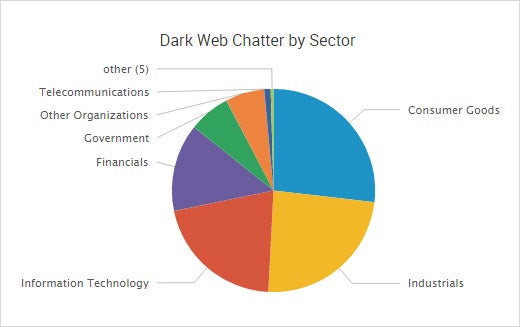
Top Industry Target on the Dark Web: Consumer Goods
In addition to public cyber crime information, SurfWatch Labs analysts found another 1,700 industry targets whose data was being bought, sold or otherwise discussed on the dark web in the first half of 2016. The consumer goods industry was the top targeted industry on the dark web, with groups such as consumer publishing, entertainment production, and retailers frequently falling into cyber criminals’ crosshairs — in addition to the many high-profile incidents being discussed on the public web involving the BBC, Hyatt Hotels, Wendy’s and others.
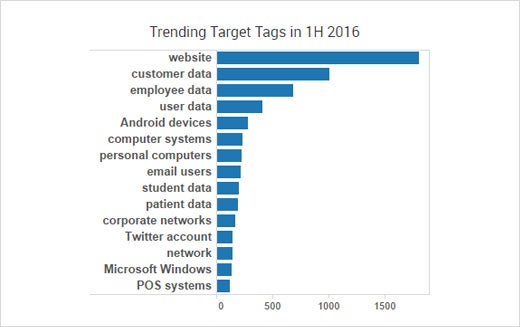
Leading Cyber Crime Target: Website Havoc
Cyber criminals choose their victims for a variety of reasons. While bad actors’ goals and motivations vary across industry group, the top goal in aggregate so far this year has been related to websites. Much of this effort is focused on malvertising campaigns, which most affected publishing specifically, but also prevalent were web attacks aimed at banks and central government that led to web defacement and downtime. Malvertising, DDoS attacks and general vandalism-related acts all increased.
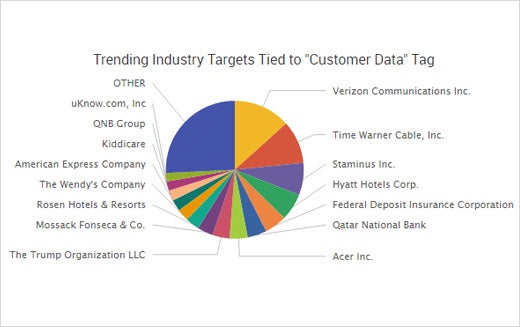
Leading Cyber Crime Target: Customer Data
The second most common effect of cyber crime was loss of customer data. Interestingly, nearly half of the CyberFacts tied to customer data were in telecommunications and consumer goods. Specifically, criminals went after Verizon Enterprise Solutions, which had a database of 1.5 million clients’ personal information put up for sale, and Time Warner, which announced as many as 320,000 customers may have had their email passwords compromised. According to Time Warner, the company wasn’t breached so the root cause was either phishing or a third-party, supply chain compromise.
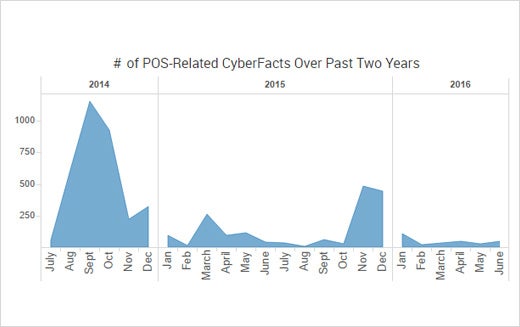
POS Compromise Still Down, Relatively Speaking
Conversely, point-of-sale (POS) activity that took center stage in 2014 and 2015 has overall been down this year. Payment card data remains very valuable but, proportionately, there were a handful of costly financial institution breaches. This category has not reached the magnitude of years past. Hotels, motels and cruise lines were once again the top trending industry group related to POS targets.
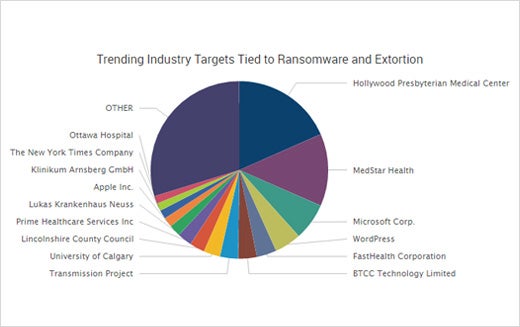
Unwelcome Trend: Extortion
Sometimes criminals stockpile data for future attacks. Other times, they use what they have to extort. The numerous attacks this year – from ransomware infections to DDoS extortion to company data being ransomed – have added to the growing shift towards malicious actors seeking payout directly from victims. Why is there such an increase in extortion-related attacks against businesses? As the saying goes, follow the money. Falling victim were Hollywood Presbyterian Medical Center, Circle-Sport Leavine Family Racing, and numerous high-profile news websites, including The New York Times, BBC and AOL.
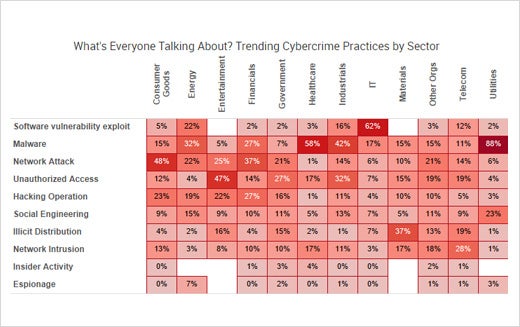
Software Vulnerabilities, Malware and Network Attacks
Nothing New: Software Vulnerabilities, Malware (Ransomware) and Network Attacks
Attack methods are not new; they aren’t overly sophisticated. The top trending tactics employed by cyber criminals this year are software vulnerability exploits, malware and network attacks. In the malware category, five of the top 10 trending tags were related to ransomware: Locky Ransomware, TeslaCrypt ransomware, Cerber ransomware, and KeRanger ransomware.
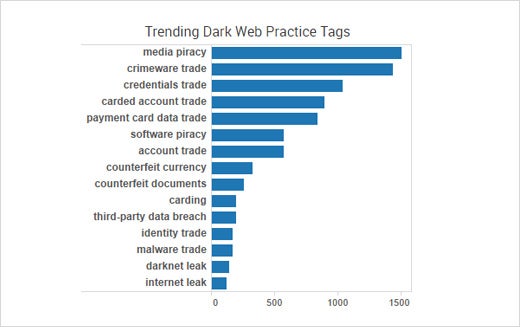
Top Trending Dark Web Practices
The dark web is where many cyber criminals go to buy and sell illicit goods and services. So far this year, media piracy was the top trending practice, followed by crimeware trade, credentials trade, carded account trade (such as Netflix accounts) and payment card data trade.

















