When it comes to virtualization security in the enterprise, the times are definitely changing.
According to a survey of over 200 IT professionals conducted during the recent VMworld 2010 conference by Altor Networks, a provider of firewall software that runs on top of a hypervisor, the number of application workloads running on top of virtual machines that need to be secured is increasing.
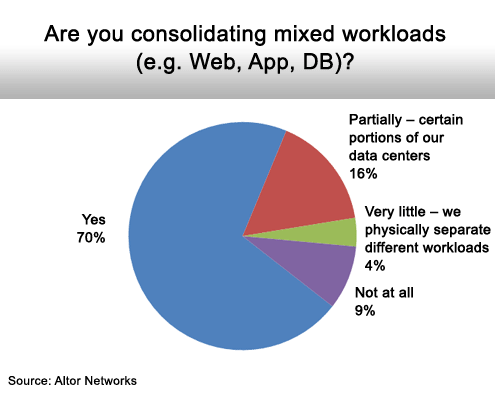
The bad news, says Johnnie Konstantas, vice president of marketing for Altor Nertworks, is that many IT organizations are violating best practices when running those application workloads. Instead of making sure that all the virtual application workloads are running on a particular physical server, most IT organizations report they are running mixed application workloads on top of virtual machines that share the same physical server.
That may be more economical in terms of increasing server utilization rates, but as Konstantas points out, it increases security risks should any one of those application workloads be compromised.
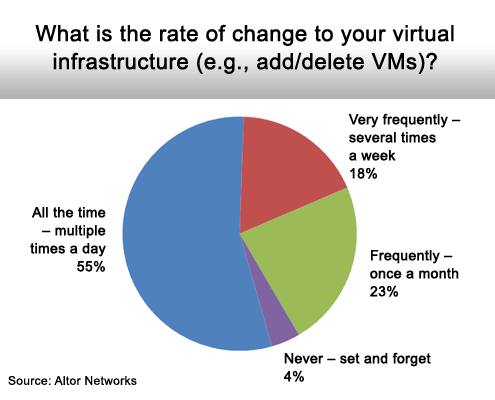
The other major challenge with virtualization security is that the workloads are becoming more dynamic. As more virtual machines are spun up across the enterprise, it’s more difficult for security professionals to keep pace with the infrastructure changes. Inevitably, this leads to some period of time when new application workloads are going to be left unprotected.
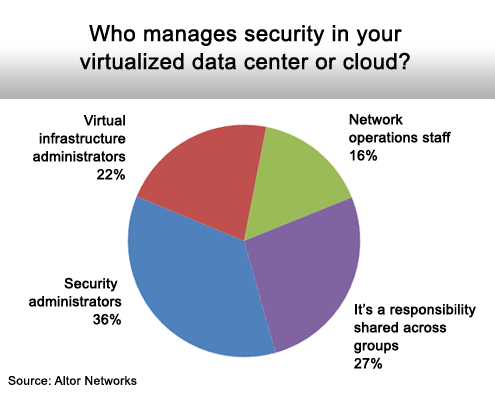
Finally, it’s not at all clear if the security teams and the people charged with running the virtual machine environments are cooperating more or if the types of people in charge of securing the virtual environment differ from company to company.
IT organizations are becoming more conscious about security issues related to virtualization in general and just because an application workload is running on top of a virtual machine doesn’t mean it’s secure.
Click through for results from a virtualization survey conducted by Altor Networks.
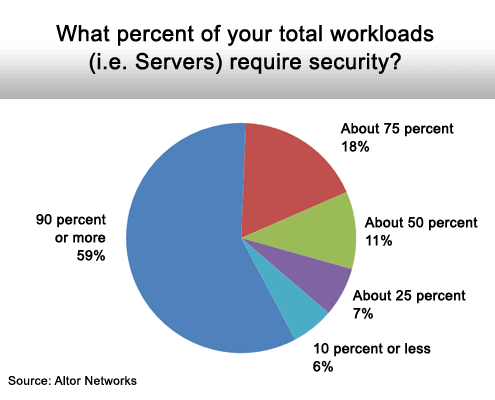
This number keeps climbing.
This is becoming the rule in spite of best practice advice.
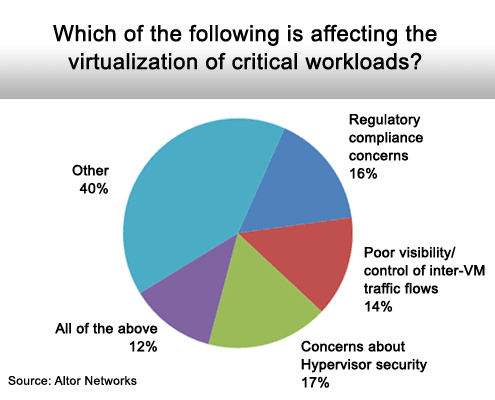
A range of virtualization security issues is in play.
The task is increasingly shared.
Change is becoming a constant.
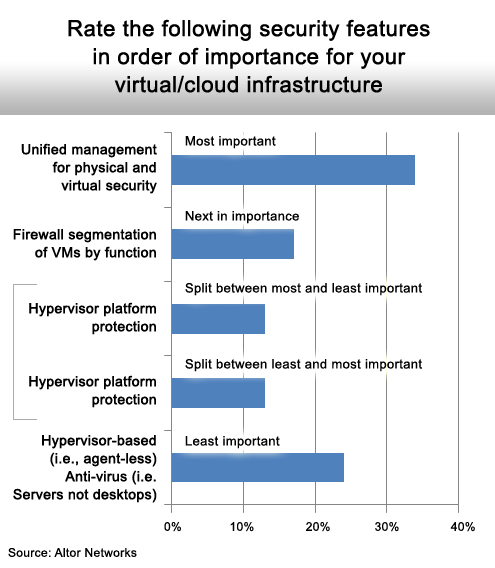
There is a need for a holistic approach to security.