Pay attention to polls like the one that HyTrust announced today if you are still wondering how your customers would react if your company were to suffer a breach of personal information. Most coverage of breaches describes the event and the missteps or malfeasance that led up to it. What really happens after that can […]
Pay attention to polls like the one that HyTrust announced today if you are still wondering how your customers would react if your company were to suffer a breach of personal information. Most coverage of breaches describes the event and the missteps or malfeasance that led up to it. What really happens after that can be harder to discern, since most involved parties won’t or can’t discuss it.
HyTrust’s snap poll of 2,000 consumers found that people, not surprisingly, are aware of recent high-profile breaches, and are prepared to change their behavior if they are affected by one.
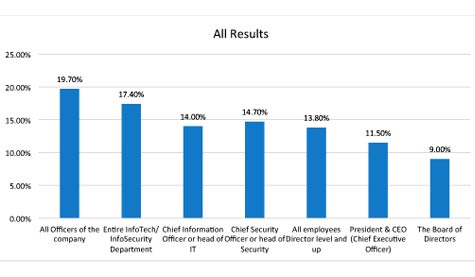
Plenty of blame will go around the company after a breach. When asked, “Who do you think should pay the price and be held ‘ultimately accountable’ for negligence involved in a data breach (e.g., where unprotected customer information is stolen)?” nearly 20 percent answered, “all officers of the company.” The board of directors seems to receive the least blame, at 9 percent.
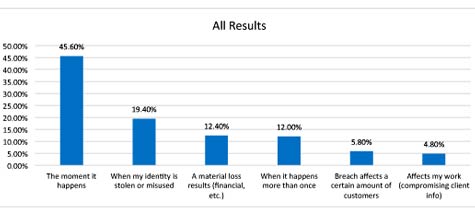
And one answer was overwhelmingly popular when customers were asked, “At what point should a vendor you do business with – bank, retail outlet, Internet Service Provider – be considered criminally negligent when your digital information is breached?”
Over 45 percent said “the moment it happens.”
And finally, keep in mind that demographics make a difference: Fifty-one percent of respondents will take their business elsewhere after a data breach; in the 35-44 age bracket, over 60 percent say the same. Whether those types of differences help or hurt your company in the event of a breach could be key.
Kachina Shaw is managing editor for IT Business Edge and has been writing and editing about IT and the business for 15 years. She writes about IT careers, management, technology trends and managing risk. Follow Kachina on Twitter @Kachina and on Google+










