 If you’re getting the feeling that your IT staff is spending more time than ever patching software because of security issues, you’re probably right.
If you’re getting the feeling that your IT staff is spending more time than ever patching software because of security issues, you’re probably right.
The latest X-Force security report from IBM shows that 2010 had the largest number of security vulnerabilities, 8,562 to be exact, in history. That’s a 29 percent increase over 2009. But worse yet, the severity of those vulnerabilities is increasing, while the amount of time it takes for hackers to exploit them is decreasing.
Unfortunately, the IBM report also shows that by the end of 2010, 44 percent of all the vulnerabilities disclosed had yet to be patched. No doubt many of those vulnerabilities are now being patched in 2011, but Tom Cross, IBM X-Force threat intelligence manager, says the report clearly shows the need for continuous security vigilance. That may mean a move to rely on a security service because IT organizations can no longer keep pace with all the vulnerabilities that can now manifest themselves on a number of platforms.
The IBM report makes it clear that the vast majority of the vulnerabilities being disclosed affect Web applications, which in 2010 were particularly prone to attacks being made through either Adobe PDF and Flash vulnerabilities or SQL Injection and Cross-Site Request Forgery attacks. Regardless of the method, the report notes that 49 percent of vulnerabilities disclosed in 2010 affected Web applications.
Some would say that the increase in vulnerability disclosures represents progress in terms of making our systems more secure. But others would argue that it highlights deeply flawed application development processes that result in huge post-production deployment costs that are pushed onto customers.
The good news is that there has been progress in terms of combating spam and phishing, but the report does acknowledge that this may be as much a result of the purveyors of malware deciding to opt for more efficient mechanisms for delivering payloads. For instance, while there were some high-profile takedowns of botnets in 2010, overall botnet activity began to rise again by the end of the year. That suggests that the builders of malware have created new, more efficient ways of automating the delivery of malware.
No matter how you look at it, security management is getting more complex with each passing day. The question that IT organizations need to ask themselves is given the ever-increasing attack surface that needs to be defended, can they really afford to go it alone anymore? Odds are that the answer is going to require higher levels of security automation just to keep pace with the sophisticated attack methods that the bad guys are using.

Click through for results from an IBM security study.
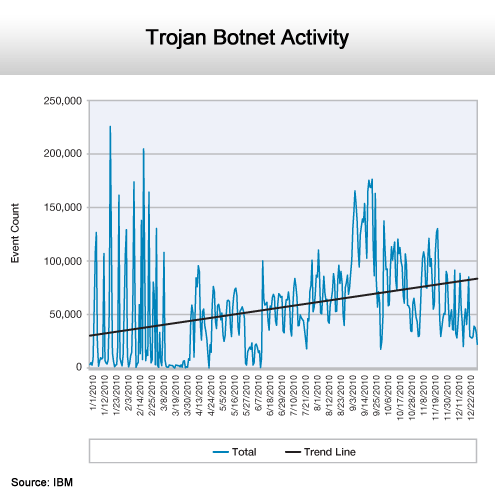
Despite best efforts it’s on the rise.
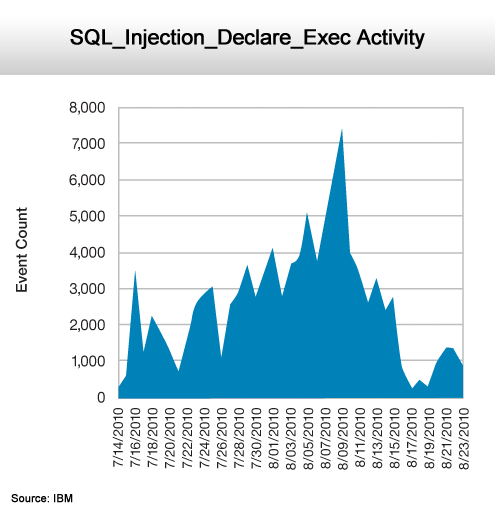
The rise and fall.
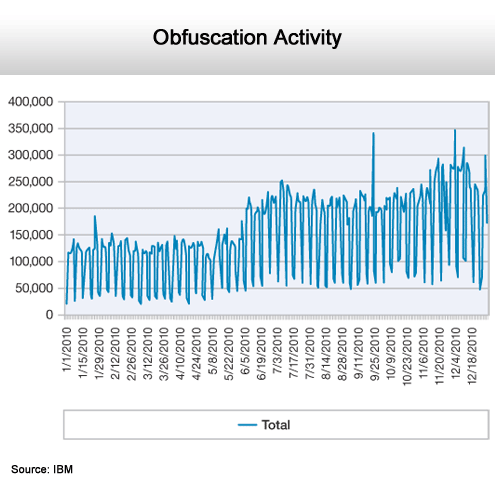
The bad guys are getting sneakier.
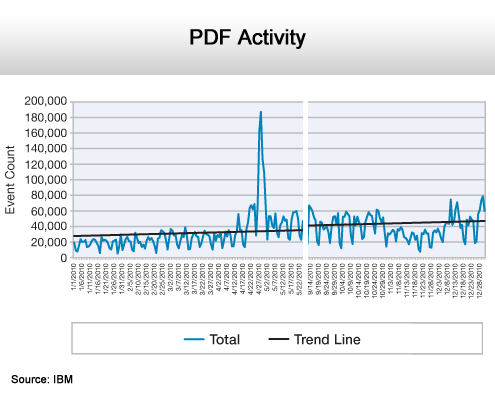
A much favored line of attack.
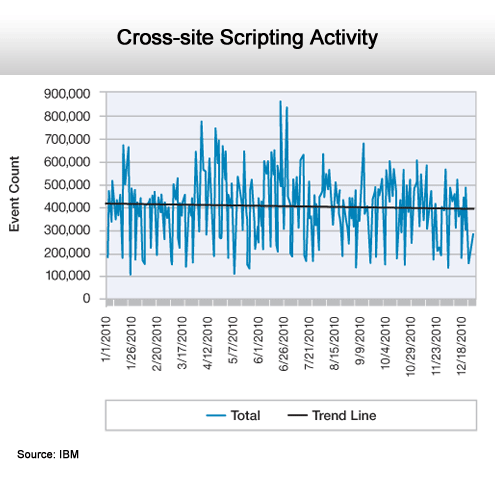
A popular way to compromise Web applications.
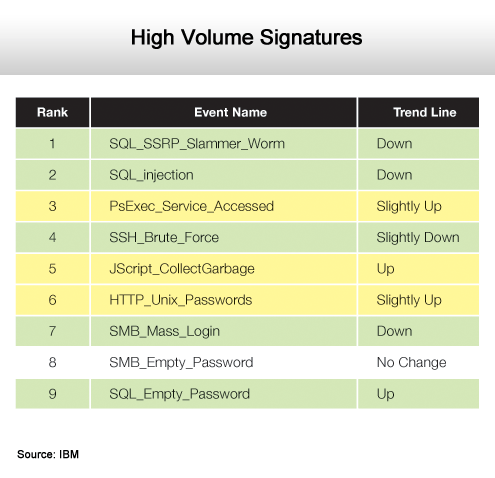
Lots of usual suspects.
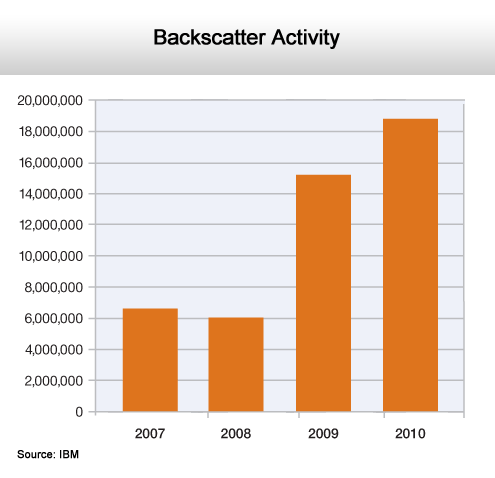
It's definitely on the rise.
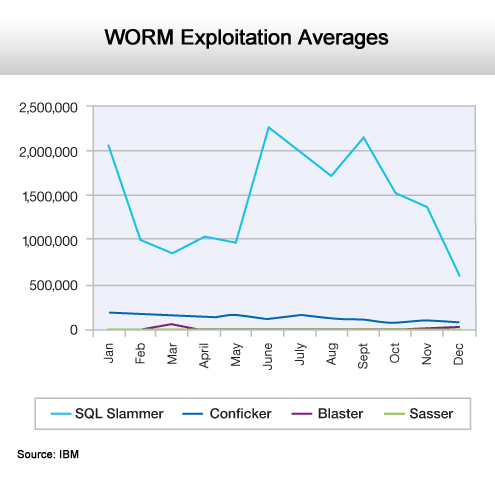
SQL Slammer dominates.
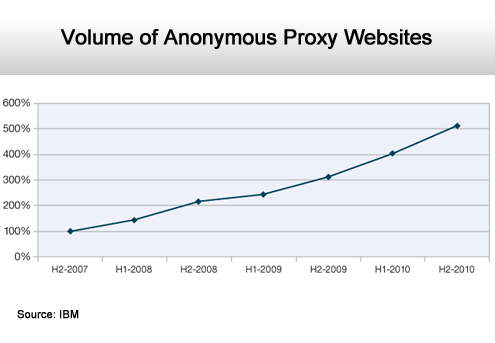
A major shift up and to the right over the years.
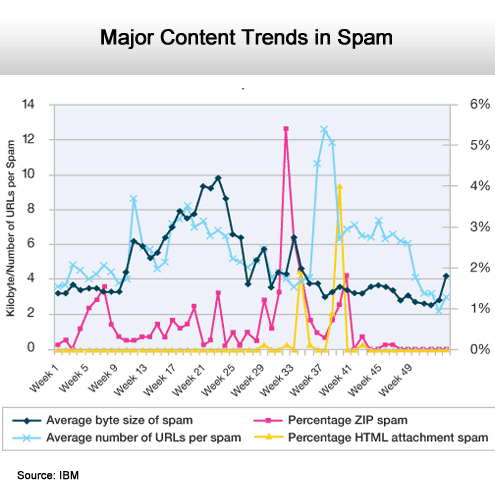
The size of Spam messages is increasing.
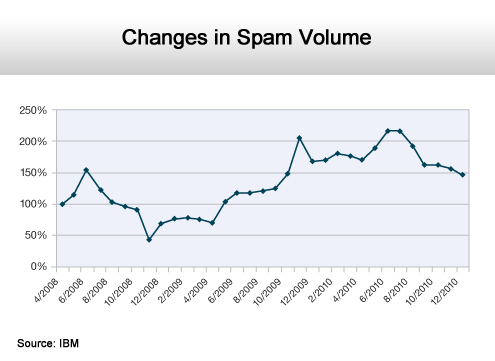
Spammers are relying less on volume.
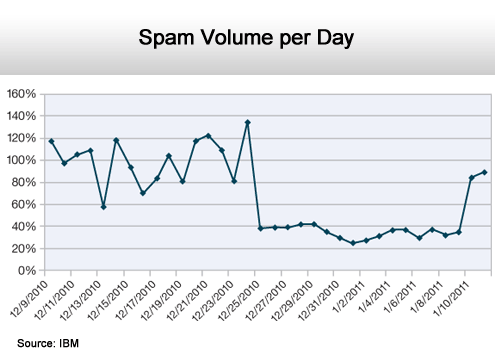
But there was a sudden spike at the end of the year.
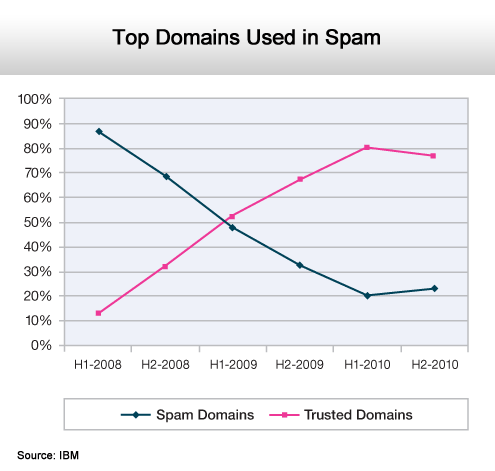
As a source, trusted domains are leveling off.
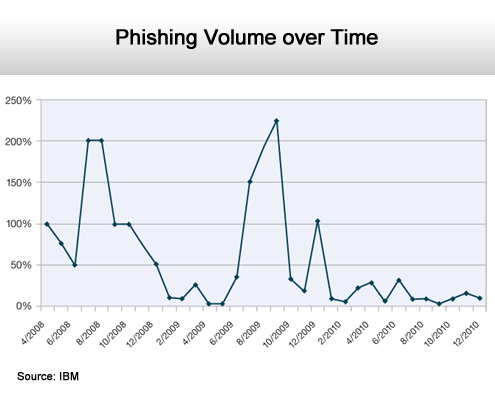
Numbers are dropping.
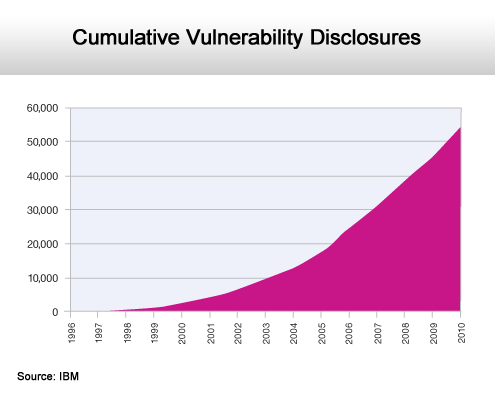
More in 2010 than any other year.
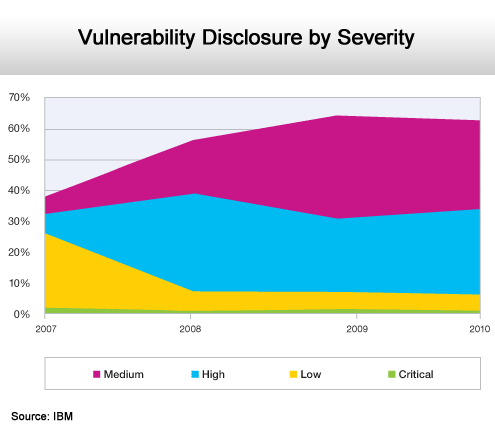
Things are getting worse.
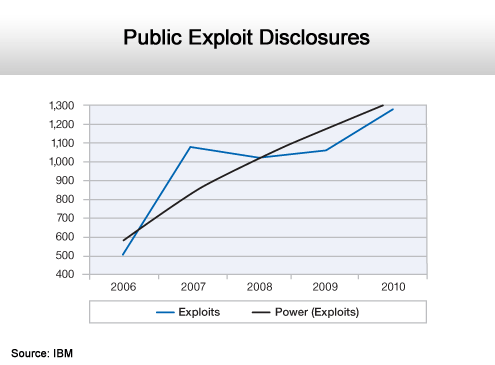
Disclosures of exploits are coming faster than ever.
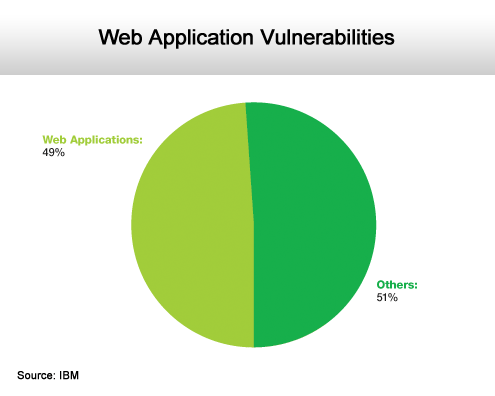
Just about half are related to Web applications.
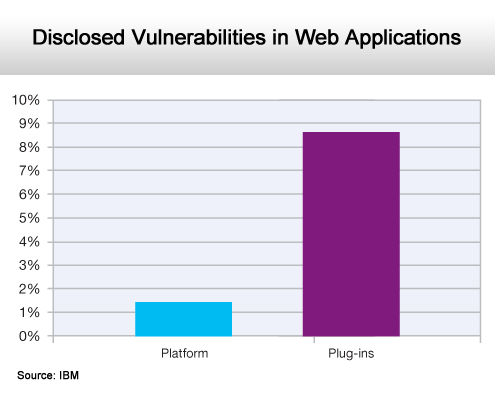
Plug-ins are often the culprit.
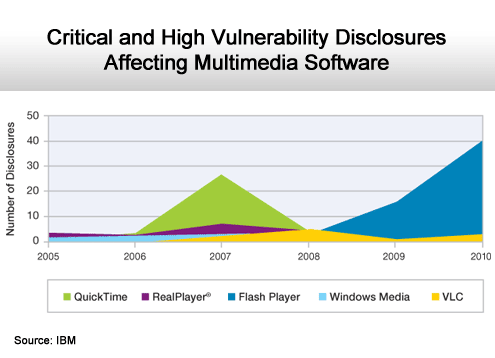
Adobe Flash Player has emerged as a problem.
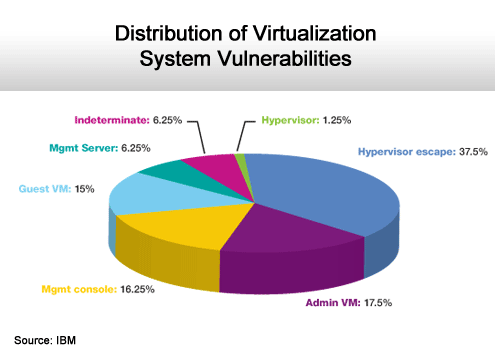
Everywhere but the Hypervisor.
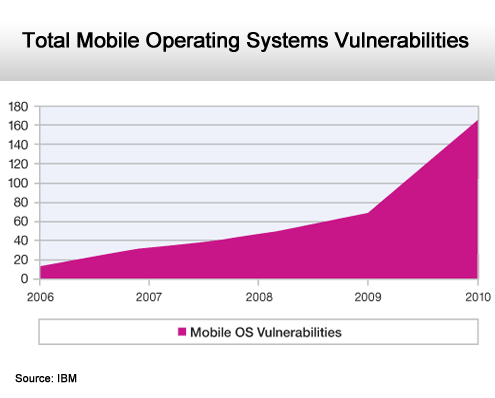
A major spike in 2010.
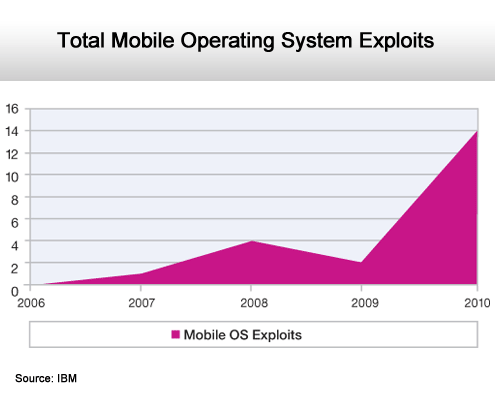
Expect this number to keep rising.

 If you’re getting the feeling that your IT staff is spending more time than ever patching software because of security issues, you’re probably right.
If you’re getting the feeling that your IT staff is spending more time than ever patching software because of security issues, you’re probably right.






























