By now, most organizations are at least familiar with the concept of “ransomware”: cybercriminals using social engineering to fool unsuspecting end users into downloading malware that winds up encrypting all of their data and then demanding a ransom in return for the keys needed to de-encrypt that data.
The only real defense against these attacks is to train end users to recognize the bogus emails and Web sites that digital criminals use to spread their malicious payloads in the first place. The simple fact of the matter is that some end users are more prone to fall victim to these attacks than others.
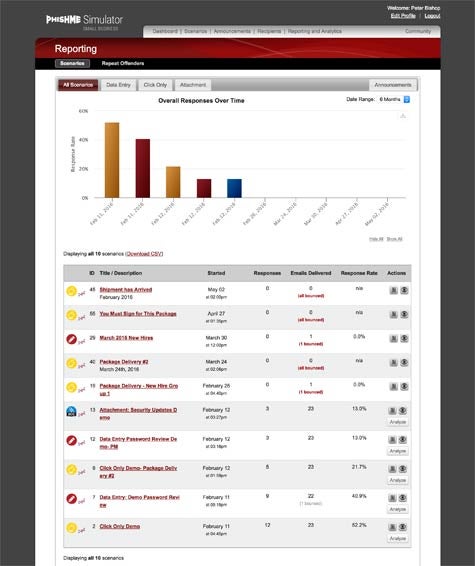
PhishMe Inc., has created a Simulator cloud service that copies social engineering techniques commonly used by cybercriminals to send phony messages to end users. The service then keeps track of which employees download content attached to those messages. This identifies employees who are the most susceptible to ransomware attempts. PhishMe COO Jim Hansen says IT organizations armed with that data then know where to focus their end-user training efforts using tools and services provided by PhishMe. In addition, PhishMe makes available an application programming interface (API) through which the security intelligence it captures can be shared with, for example, security information and event management (SIEM) systems.
Originally designed for large enterprise IT organizations, PhishMe is now extending the reach of its Simulation service to include a small business edition priced at $3,500.
Obviously, the best defense against ransomware is to regularly back up data. That way, if data winds up being encrypted, the amount of potential lost data is usually minimized. Of course, if your organization does fall victim to ransomware, it’s up to each organization to figure out whether it makes sense to pay the ransom or not.
The one thing organizations should remember is that ransom payments don’t come with any guarantees that digital criminals won’t ask for even more money the next time they succeed in taking your data hostage.