Even though a $635 million acquisition of the company by Cisco is pending, OpenDNS is plowing ahead with new security intelligence services designed to make it simpler to identify where malware is being generated, consumed and distributed.
Bobby Guhasarkar, director of product marketing at OpenDNS, says the Investigate service being made generally available today on the OpenDNS cloud is a security analytics application that organizations can access using a set of search tools or programmatically using a set of application programming interfaces (APIs) that OpenDNS has exposed.
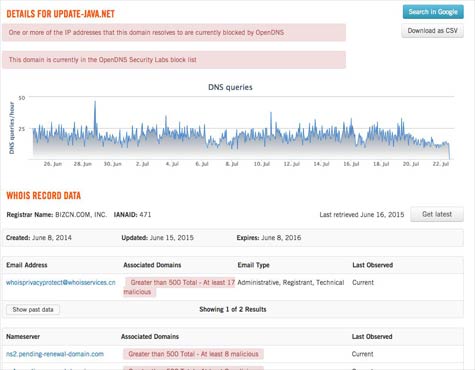
In either scenario, Guhasarkar says OpenDNS is trying to simplify the analysis of the terabytes of DNS data and BGP route information gathered from its DNS servers and more than 500 peering partners, in order to provide a fairly comprehensive view of the malware activity taking place across the Internet.
OpenDNS currently uses that information to identify sites that are distributing malware. Investigate now opens those data sources to security professionals using over a dozen modeling tools that have been created by the OpenDNS Security Labs team.
Obviously, Cisco intends to use OpenDNS data to not only bolster its own security intelligence, but also automate as much of the security vulnerability process as possible. If security professionals can better identify potential threats before they infect their systems, then that information can be used to patch security holes in the applications and systems that malware is intended to exploit.
It may still be a while before that level of security automation is achieved. In the meantime, though, Guhasarkar says that thanks to advanced analytics manifested in applications such as Investigate, it’s getting a lot easier to determine exactly how any given piece of malware found its way into those applications and systems in the first place.