When it comes to data security, most IT organizations don’t have a handle on how often and to what extent their data is compromised.
A recent survey of 1,176 IT professionals conducted by the market research firm Securosis on behalf of Imperva, a provider of a range of data security technologies, found that the vast majority did not know how many times they may have experienced a major attack either eternally or internally, nor did they know what type of data had been stolen.
According to Imperva CTO Amichai Schulman, most IT organizations are not very effective in assessing the scope of the damage incurred by a security breach even when they are aware of the breach. And as the number of these breaches increases along with attacks aimed at the application layer, too many IT organizations are still overly dependent on a single line of defense at the security perimeter.
This situation not only makes it hard to justify security budgets, it frequently means that IT organizations during tough times are making hard choices in how to apply those budgets. Although applications are increasingly the primary point of attack, fear and inertia result in most of the IT security budget being spent on defending the network perimeter.
The Securosis survey shows that most IT professionals believe that most of the security technology they acquire is effective to one degree or another. It also shows that USB media encryption and data loss prevention technologies are at the top of the IT shopping list. In addition, the survey finds that the most effective security controls are full-drive encryption, access management tools, e-mail filtering and data loss prevention systems on the network. Survey participants also identified e-mail filtering and USB media encryption as the top two least effective security controls.
In the meantime, Schulman notes that the people launching these attacks are becoming more sophisticated by the day thanks to the influx of funding from organized crime syndicates. The end result is that IT organizations are increasingly outgunned when it comes to security.
Therefore, the challenge going forward, says Schulman, is figuring out how to size the appropriate level of security to the value of the data threatened. Unfortunately, many IT organizations don’t have a handle on the value of any given piece of data because they tend to manage all data as if it were of equal value. And until that situation changes, it’s only a matter of time before something bad happens that the IT organization may or may not know anything about.

Click through for IT security survey results from Securosis.
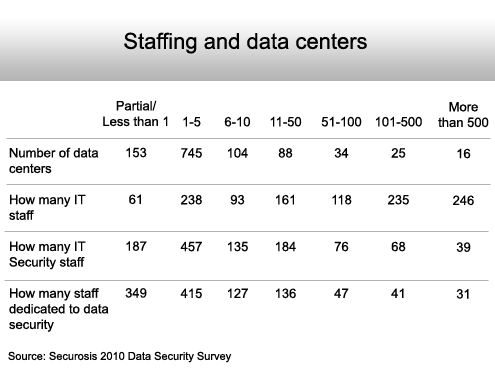
There is no correlation between the number of data centers and the size of the IT staff.
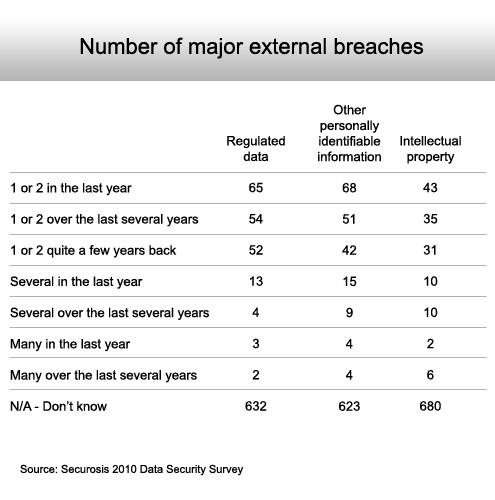
The majority have no idea.
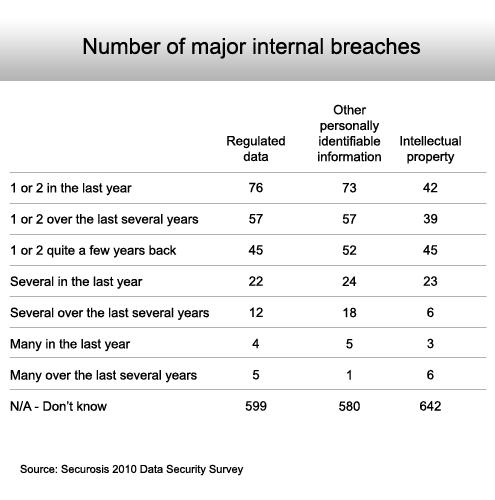
The same goes for internal breaches.
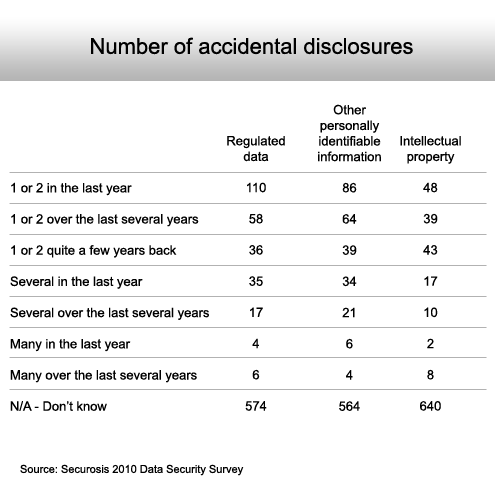
Again, ignorance appears to be bliss.
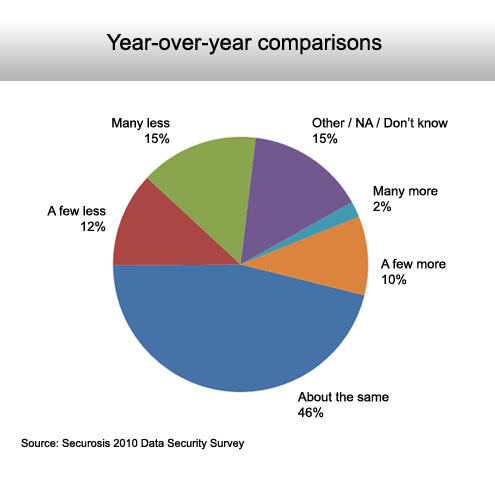
Most appear to be staying even when it comes to security.
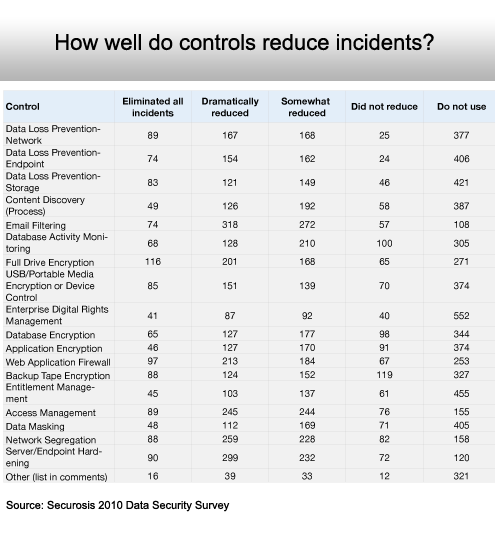
When used, most security technologies have a positive impact.
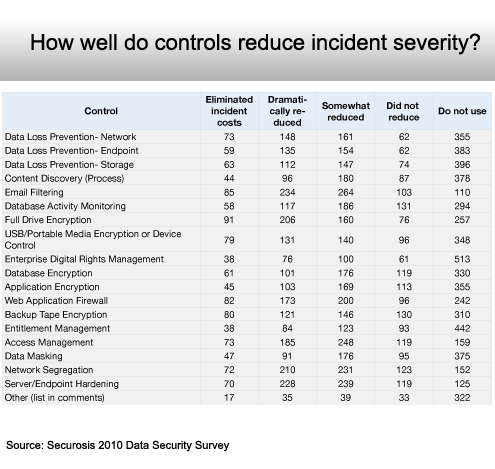
And things would be much worse without them.
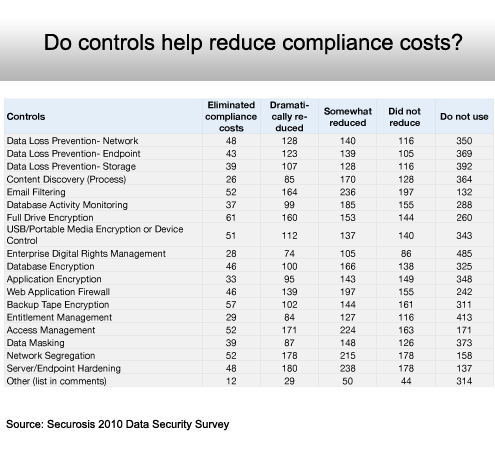
Opinions lean toward the positive.
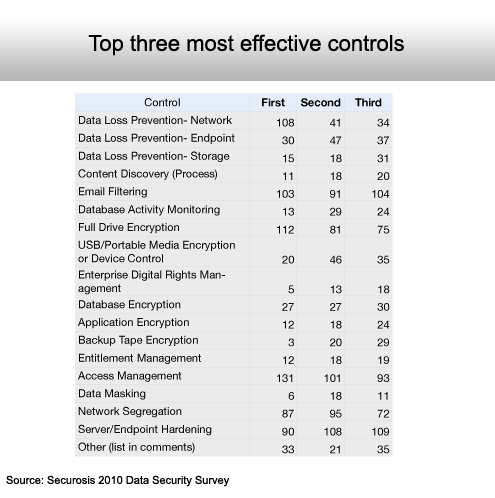
Access management tops the list.
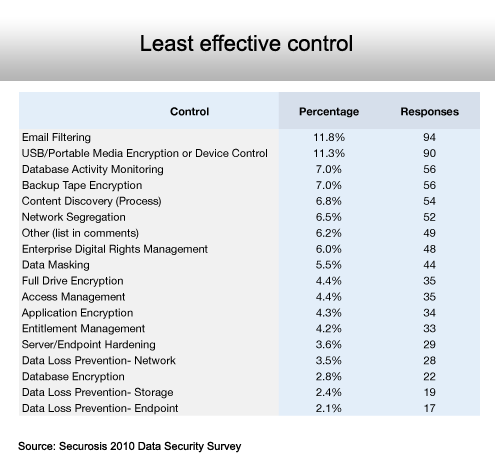
Email filtering and USB drive encryption top the list.
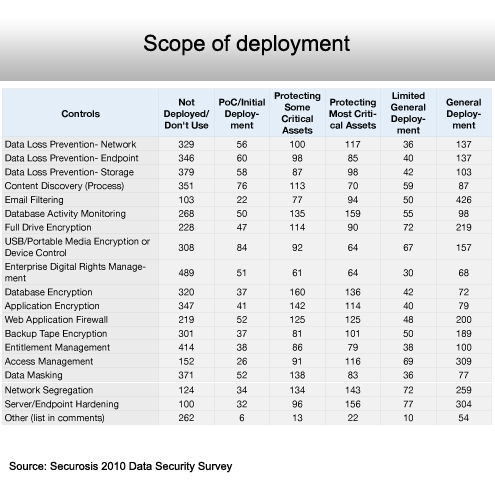
Email filtering and access management are the most generally deployed.
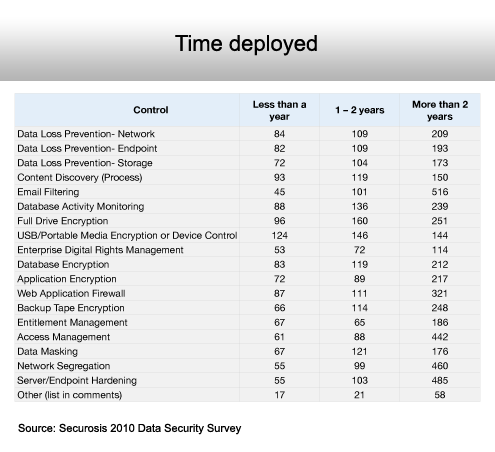
Security technology experience runs deep.
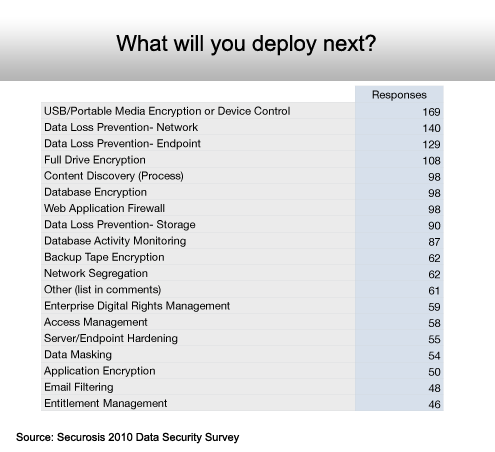
Portable media encryption and data loss prevention lead the charge.






















