Looking to give both end users and IT organizations control over files no matter where they are sent, FinalCode today announced the general availability of software that allows organizations to not only attach permissions to a file, but also delete them whenever necessary regardless of where they are or who has possession of them.
FinalCode CEO Gord Boyce says the company’s namesake software can be deployed using a virtual appliance that runs on top of an existing file system running on-premises, or it can be invoked as a cloud service. In either case, FinalCode allows end users to encrypt a document, and it enables them to delete all copies of the file no matter how many have been made or distributed, says Boyce.
Making use of agent software that is deployed on each endpoint, Boyd says end users then drag and drop a file onto a graphical representation of the agent software to attach the level of security they deem appropriate for that document. Once embedded in the file, the agent software continuously communicates back to the central FinalCode management platform.
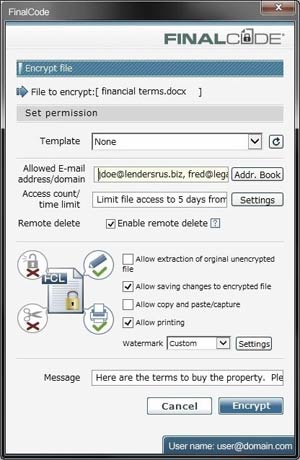
Though IT pros push the importance of encryption, one fundamental problem is that typically, encrypted files are never actually removed. This means that any entity with the wherewithal to crack an encryption scheme may still have the opportunity to breach the file.
If organizations want to hold end users more accountable for security, they need to provide a way to enable them to apply and enforce security policies that doesn’t require constant supervision of every file by the already overtaxed IT organization.



