Digital forensics has continued to grow in importance as enterprises deal with increasing amounts of digital data and the possibility of cyber-attackers infiltrating their systems. Digital forensics investigation tools will continue to evolve and improve, offering organizations the ability to identify malicious actors and defend against attacks before serious damage can be done.
Table of Contents
What is Digital Forensics?
Digital forensics is a branch of forensic science involving data recovery and analysis techniques in order to aid security investigations. It uses established forensic procedures and protocols to extract, preserve, analyze, and document computer-related data. Forensic results are used to determine if an illegal activity has occurred or confirm whether or not events took place as expected.
The goal of digital forensics is to discover, recover and document electronically stored information (ESI) from computers, cell phones, storage devices, and networks for legal purposes. It provides a vital link between today’s high-tech crimes and criminal investigations.
Whether your company’s enterprise network has been compromised by an outsider or you suspect employees may be stealing intellectual property for personal gain, digital forensics can help you get to the bottom of it. Depending on how you use your computer and which applications you have installed, there are likely many pieces of information related to every action taken on your system. Thus understanding how each piece fits together—and its relevance within a given investigation—is essential for successfully reconstructing each event.
Also read: Cybersecurity Awareness for Employees: Best Practices
What are Digital Forensics Tools?
Computer forensics tools are computer applications used to investigate digital devices and reconstruct events. While most people associate computer forensics with law enforcement, they are also used by network administrators, IT professionals, and other individuals who may come across a computer system or device in a state of compromise.
Computer forensic investigators gather evidence from systems logged into an investigation case. This data is then compared to other evidence and analyzed for discrepancies to find out what happened at a given time on a device. The process results in a step-by-step account of an event, such as unauthorized access to files or tampering with executable code.
With software involved in so many aspects of our daily lives—including computers at work and home, smartphones we carry around all day long, wearables, activity trackers, and smartwatches—it’s not surprising that digital forensics tools have become so popular over recent years. Statista estimates there will be 7.26 billion mobile devices in use globally by 2022, and 75.44 billion IoT devices will be connected to the internet by 2025.
As a result, cybercrime is also on an upward trajectory. The number of cases involving online crime is increasing year on year, according to Cybersecurity Ventures, which estimated that global cybercrime costs could reach $10.5 trillion annually by 2025 if nothing is done to combat it.
Benefits of Digital Forensics Tools
Help find vulnerabilities
Without good security measures there is no way to protect your sensitive information from falling into cybercriminals’ hands. The moment they do, you can expect unwanted emails, lost productivity due to poor service quality, and an overall bad online reputation. To prevent such problems, you need to keep constant tabs on everything happening in or around your system or network so that you can get rid of vulnerabilities before they cause real harm.
Checks employee-related crimes
Employees tend to be interested in accessing information that doesn’t concern them or sharing confidential data with third parties, especially if they want to make extra money. Of course, both actions are strictly prohibited in any business environment, so implementing digital forensics solutions will help you detect when employees breach your confidentiality rules and take immediate action against them.
Helps monitor online threats
Hackers are always coming up with new ways to attack users and steal their personal data without getting noticed. So to stay ahead of these scammers, you need powerful surveillance software capable of keeping constant tabs on what happens in or around your networks without disrupting normal operations even slightly.
Protects industrial espionage
Businesses attract competitors who might use various techniques, including industrial espionage, to learn about your latest strategies, plans, and developments. For example, to grab hold of your trade secrets, they might send someone posing as a contractor to improve one of your products or services.
Assists law enforcement agencies
Law enforcement agencies rely heavily on digital evidence to build criminal cases against perpetrators. However, collecting and storing large amounts of information takes a lot of time and resources, which could otherwise be spent chasing criminals down instead.
Also read: Best Antivirus Software for Business 2022
Top 7 Digital Forensics Tools and Software
There are many digital forensics tools and software to choose from, so where do you start? As outlined below, our top 7 picks stand out from their peers due to their support for file integrity monitoring, remote access abilities, and more.
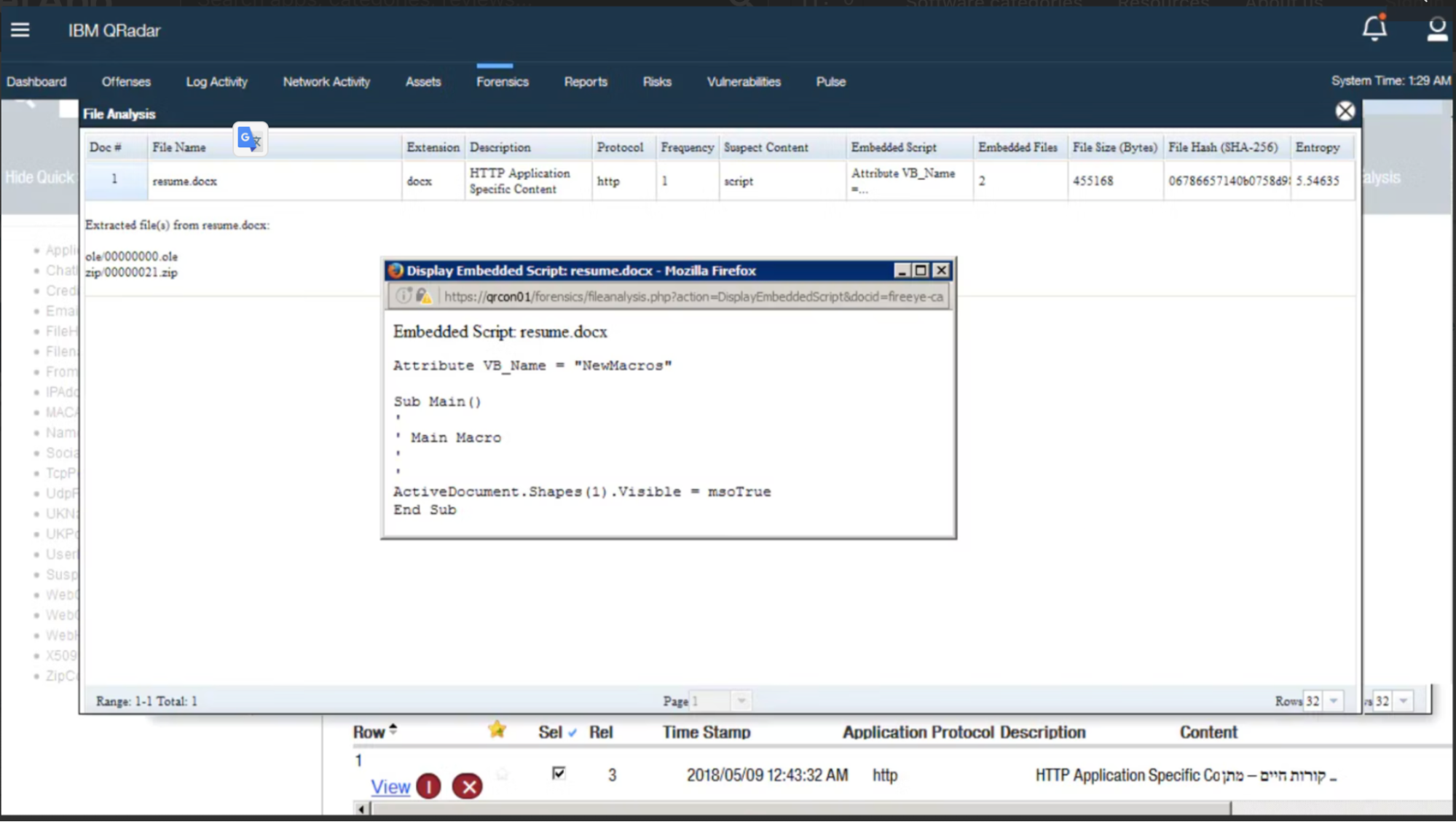
IBM Security QRadar
QRadar gives security professionals centralized access into enterprise-wide security data as well as actionable insights into the most critical threats. Security analysts may use a single pane of glass to immediately evaluate their security posture, identify the most serious risks, and dig down for further information, which helps to expedite processes and eliminates the need to switch between tools. Using QRadar’s anomaly detection capabilities, security teams can quickly identify changes in user behavior that could be indicators of an unknown threat.
Key Differentiators
- Retrace the step-by-step actions of cyber criminals.
- Rebuild data and evidence related to a security incident.
- Enable threat-prevention collaboration and management.
- Rebuild data and evidence related to a security incident.
Pricing
No pricing details are available on the vendor website. However, a 14-day trial is available and you can get in touch with IBM Qradar team for quotes tailored to your enterprise needs.
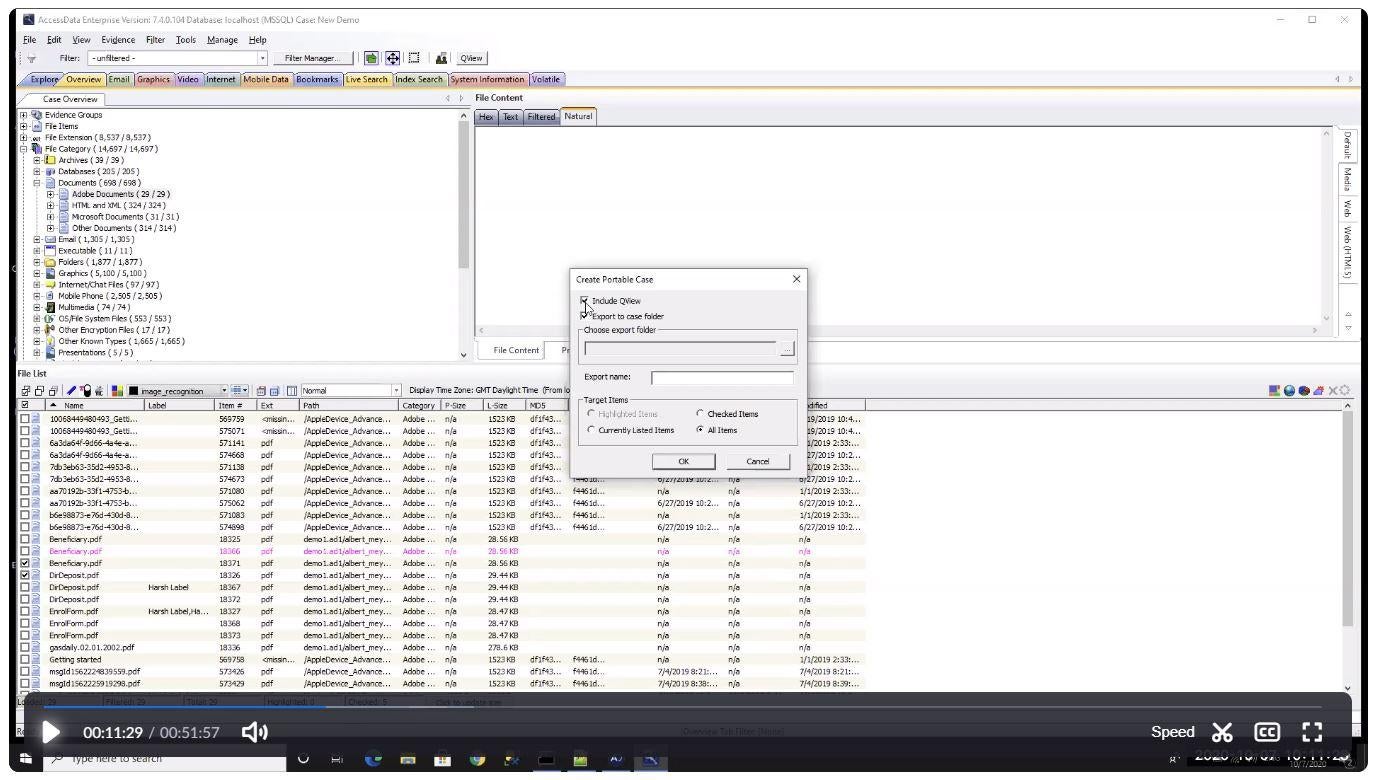
FTK Forensic Toolkit
Forensic Toolkit (FTK) is a court-approved digital forensics software designed to help businesses across various verticals collect and process data from different sources. The tool also offers file decryption and a password cracking system.
Key Differentiators
- Provides full-disk forensic images.
- It visualizes data in timelines, cluster graphs, pie charts, geolocations, and other ways to help you understand occurrences.
- FTK can decrypt files, crack passwords from over 100+ applications,and build reports.
- FTK supports decryption of File Vault 2 from the APFS file system, as well as importing and parsing of AFF4 images created from Mac computers.
- FTK enable you locate, manage and filter mobile data more easily with a dedicated mobile tab.
Pricing
Pricing details are not available. You can schedule a demo with the FTK team to find out if the solution is a good fit for your enterprise unique needs.
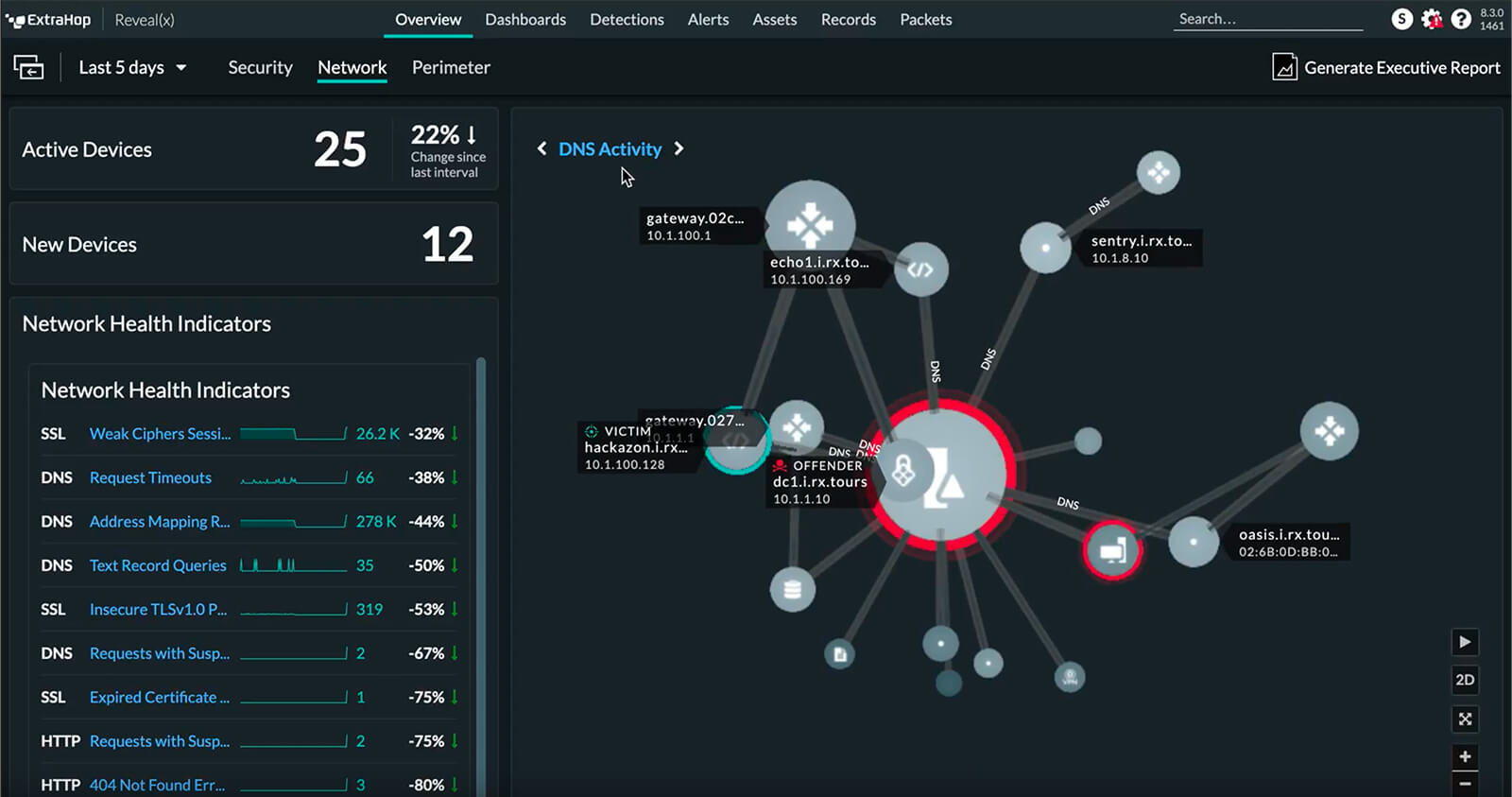
ExtraHop
The ExtraHop Reveal(x) 360 cyber defense technology detects and responds to advanced threats before they undermine business security. They process petabytes of data every day using cloud-scale AI, decrypting and analyzing all infrastructure, workloads, and data-in-flight. With ExtraHop’s comprehensive visibility, enterprises can spot malicious activity, hunt advanced threats, and investigate any incident.
Key Differentiator
- ExtraHop identifies threats using behavior-based analytics backed by machine learning.
- Address rogue instances, exposed resources, and ongoing cloud-based threats as soon as possible.
- Support distributed workforce, cloud migration, and resolve performance challenges.
- ExtraHop Reveal(x) automatically classifies all devices interacting on the network, to enable security teams to detect and decrypt malicious actors.
Pricing
ExtraHop offers three distinct solution for various enterprise use cases: ExtraHopReveal(x) for network detection and response platform for hybrid enterprise; Reveal(x) 360 is SaaS-based security for edge, core, and cloud deployments and ExtraHop Reveal(x) IT analytics performance for IT operations. You can book a free demo with the ExtraHop team.
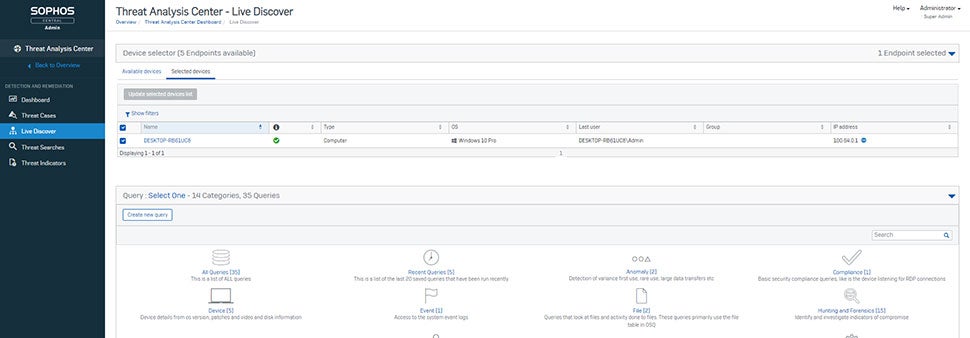
Intercept X Endpoint
Intercept X Endpoint helps security analysts and IT managers in detecting and blocking malware assaults across networks by using deep learning technologies. Administrators may use the program to detect and interrupt malicious encryption processes, protecting the system against file-based attacks and master boot record (MBR) ransomware.
Key Differentiator
- Intercept X detects and investigates suspicious activity with AI-driven analysis.
- Sophos Intercept X Advanced with XDR synchronizes native endpoint, server, firewall, email, cloud and O365 security.
- Sophos Intercept X offers advanced protection technologies that disrupt the whole attack chain, including deep learning that predictively prevents attacks and CryptoGuard that rolls back the unauthorized encryption of files.
- You can investigate potential threats, create and deploy policies, manage your estate, see what is installed where and more, all from the same unified console.
Pricing
Intercept X Endpoint offers three pricing models:
- Intercept X Advanced costs $28 per user/per year
- Intercept X Advanced with XDR $48 per user/per year
- Sophos Managed Threat Response $79 per user/per year
Request quotes if you want features tailored to your enterprise needs. A free demo is also available.
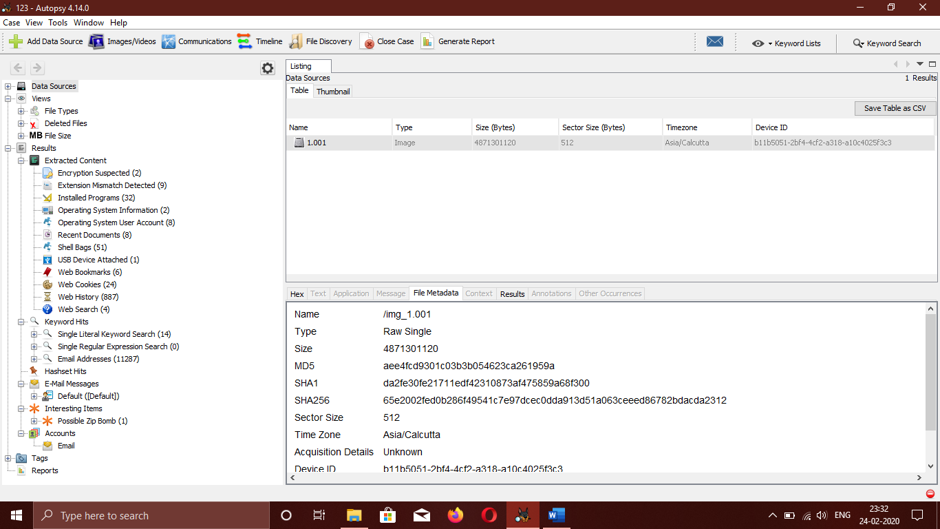
Autopsy
Autopsy is a digital forensics platform that also serves as a graphical interface for The Sleuth Kit and other digital forensics tools. It is used to investigate cybersecurity incidence on a computer by law enforcement, military, and company examiners.
Key Differentiator
- Autopsy supports major file systems such as NTFS, FAT, ExFAT, HFS+, Ext2/Ext3/Ext4, YAFFS2 by hashing all files and unpacking standard archives.
- Supports hard drives and smartphones.
- EXIF data extraction from JPEG images.
- Provides timeline analysis for all events.
- The Sleuth Kit enables you to extract data from call logs, SMS, contacts, and more.
Pricing
Autopsy is a free open source tool.
CAINE
CAINE (Computer Aided Investigative Environment) is an open source forensic platform that combines software tools as modules with strong scripts in a graphical user interface environment. Its operating environment was created with the goal of providing forensic professionals with all of the tools needed to conduct digital forensic investigations (preservation, collection, examination, and analysis).
Key Differentiator
- Offers a comprehensive forensics environment that is interoperable and can integrate with other software.
- CAINE may operate in live mode on data storage devices without the need to boot up an operating system (OS).
- CAINE software enables cloning.
- Offers a user-friendly graphical interface.
- Support semi-automated compilation of the final report.
Pricing
CAINE is a free open source tool.
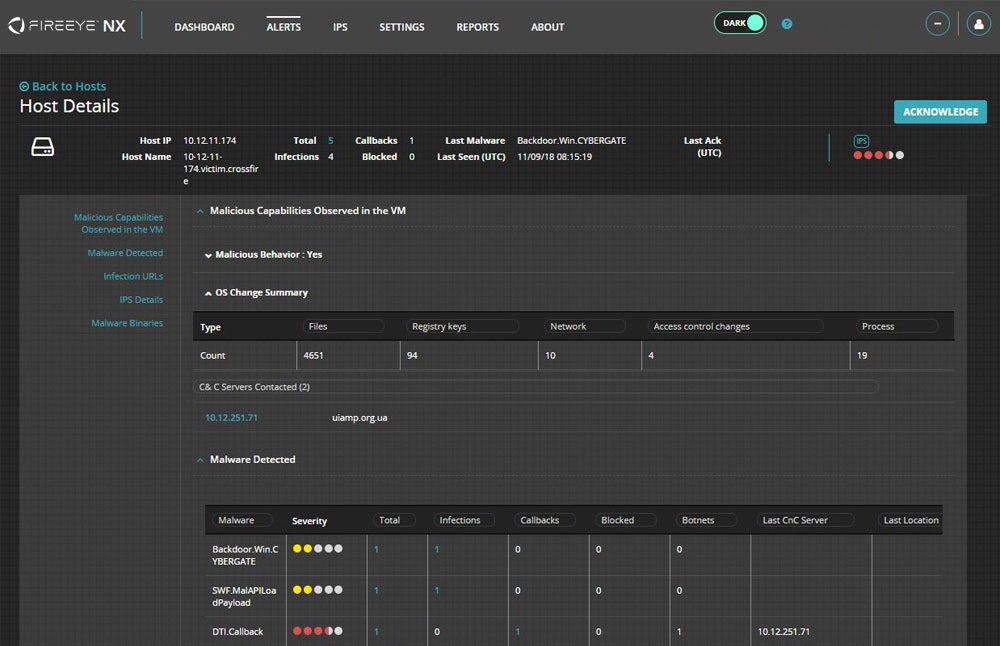
FireEye Network Security and Forensics
FireEye Network Security is a cyberthreat prevention system that helps enterprises reduce the risk of severe breaches by effectively identifying and blocking advanced, targeted, and other invasive attacks hidden in internet traffic. The Multi-Vector Virtual Execution (MVX) and dynamic machine learning and artificial intelligence (AI) technologies are at the core of FireEye Network Security.
Key Differentiator
- Detection of advanced, targeted and other evasive cyber attacks.
- Multi-vector correlation with email and content security.
- Immediate blocking of attacks at line rates from 250 Mbps to 10 Gbps.
- Low rate of false alerts, riskware categorization and mapping to MITRE ATT&CK framework.
- Pivot to investigation and alert validation, endpoint containment and incident response.
Pricing
Contact FireEye sales team for a detailed quote.
Choosing a Digital Forensics Tool
When choosing a digital forensics tool, you want to begin by getting as many answers to these questions as possible:
- What kind of investigations do I need to conduct?
- What evidence will I be working with?
- How large is my budget for buying software tools?
- How much time am I willing to invest in learning how to use new software applications?
The answers to these questions can help you narrow down your options. Many companies offer starter kits (often called suites), which bundle various pieces of software that are related to a particular type of investigation (i.e., computer fraud). Once you’ve chosen an investigative domain and narrowed your list down to two or three products, it’s important to test them out and see what works best for you.
In most cases, demo versions of programs are available online and free of charge; try it out on a familiar machine before making any commitments. If no demo version is available, read reviews to get a sense of whether other investigators have had good experiences using it. This can give you a better idea of whether or not it’s worth trying without a test drive.
Read next: Top Threat Intelligence Platforms & Tools