6 Cyber Secrets Setting You Up for Betrayal One of the primary reasons so many relatively simple attacks wind up compromising IT security defenses is that the internal IT organization suffers from IT security fatigue. In any given day, any number of IT security technologies will generate a stream of alerts, most of which wind […]

6 Cyber Secrets Setting You Up for Betrayal

One of the primary reasons so many relatively simple attacks wind up compromising IT security defenses is that the internal IT organization suffers from IT security fatigue. In any given day, any number of IT security technologies will generate a stream of alerts, most of which wind up being false positives. After a while, the IT organization becomes inured to the alerts until, of course, one of them involves a previously undiscovered vulnerability. By then, the damage is done.
Arctic Wolf Networks this week unfurled AWN Cyber-SOC, a service through which security professionals provide a security information event management (SIEM) capability based on a combination of custom, open source and commercial software technologies that serves to reduce internal IT security fatigue.
Rather than take over IT security management completely, Arctic Wolf Networks CEO Brian NeSmith says, AWN Cyber-SOC is designed to supplement efforts of the internal IT security department. All the firewalls and endpoint security continues to be managed by the internal IT department. Arctic Wolf Networks takes over responsibility for keeping track of the number and types of attacks being launched and what vulnerabilities they are trying to exploit inside the organization, says NeSmith. In effect, NeSmith says, Arctic Wolf Networks becomes the security operations center for the organization that is responsible for all activities relating to IT security hygiene.
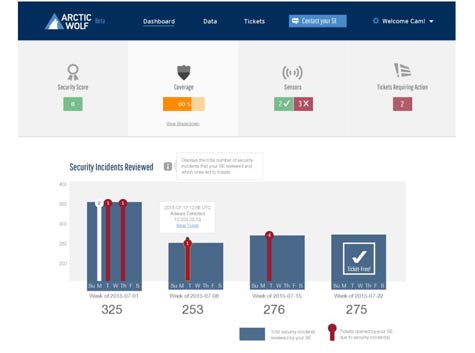
But what makes Arctic Wolf Networks most unique, says NeSmith, is that specific engineers are dedicated to a customer. That engineer not only knows the topology of the IT environment of the customer, but Arctic Wolf Networks eschews all the upfront installation and discovery fees normally imposed by a provider of managed security services.
Looking for anomalies that might signal an attack in massive amounts of log data requires both patience and expertise. When it comes to IT security, most internal IT organizations have neither. As such, it makes more sense to outsource that part of the IT security function to an organization built from the ground up to have both those attributes in abundance.
MV
Michael Vizard is a seasoned IT journalist, with nearly 30 years of experience writing and editing about enterprise IT issues. He is a contributor to publications including Programmableweb, IT Business Edge, CIOinsight and UBM Tech. He formerly was editorial director for Ziff-Davis Enterprise, where he launched the company’s custom content division, and has also served as editor in chief for CRN and InfoWorld. He also has held editorial positions at PC Week, Computerworld and Digital Review.










