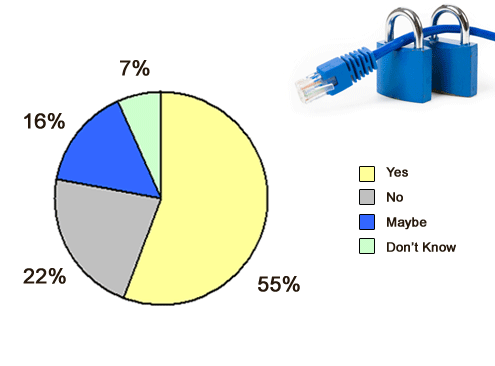After spending billions of dollars trying to secure network perimeters, IT organizations are discovering, sometimes through painful experience, that hackers and developers of various forms of malware are increasingly focused on compromising applications.
That only makes sense because, after all, that’s where the valuable data is. At the same time, these attacks are getting more targeted in order to fly under the radar of security solutions that are designed to look for specific types of signatures. The end result is not only more dangerous attacks, but also ones that are increasingly invisible to IT organizations.
The end result is that no one is really sure how many applications are compromised. But according to a recent survey of 300 IT professionals that was conducted by Fortify Software at the recent Infosecurity Europe 2010 conference, 56 percent said software in use within their organization was compromised. Worse yet, 16 percent said maybe and 7 percent said they didn’t know.
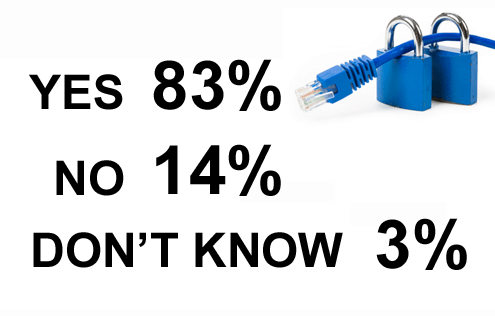
Perhaps even more disturbing, 83 percent said that the commercial software they buy off-the-shelf comes with all kinds of unknown vulnerabilities, which accounts for why IT organizations spend so much time patching software these days.
Barmak Meftah, chief products officer for Fortify, says a big part of the problem is that application developers really don’t focus on security. It’s only when the security team sits down with developers to show them what they are doing to make it easy for outsiders to compromise their software that any real fundamental change takes place.
Meftah says application developers will be focusing a lot more on security with the advent of cloud computing, which in many cases comes with fairly detailed security requirements as part of the service level agreement mandated by the cloud computing provider.
What all this means is the security landscape as a whole is going through a profound transformation that will ultimately change the way application software is developed. In the meantime, it’s now incumbent on most IT organizations to access their application security because what worked well last year is increasingly becoming irrelevant today.
Click through for findings from a recent survey by Fortify Software.
At least more than half are certain there are.
And the number of attacks aimed at applications is growing.
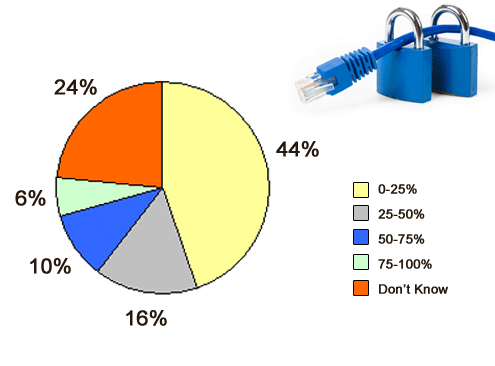
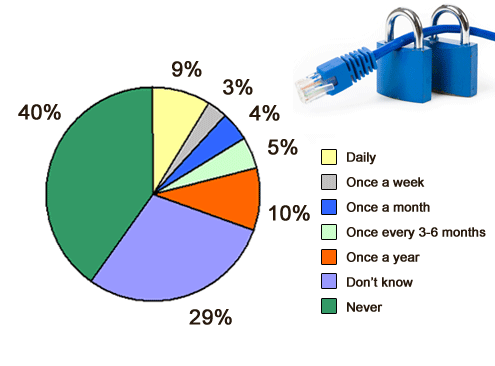
Many don’t know, and those that say never may not know either.
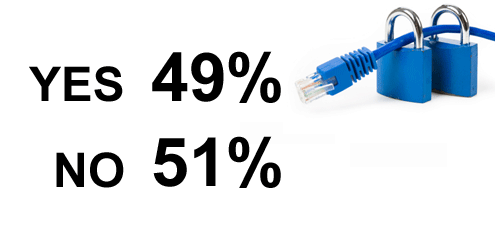
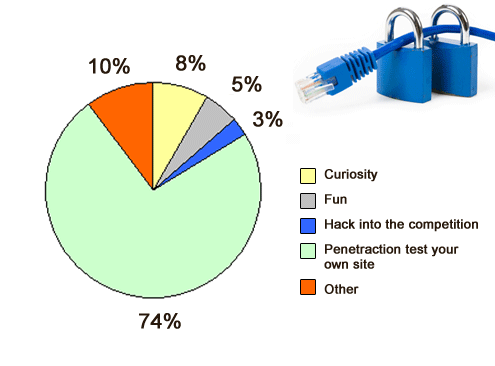
About half have some personal experience with hacking.
Most are doing penetration testing on their own sites.
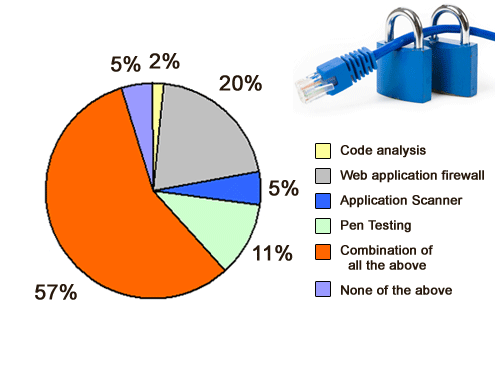
Most are applying a mix of solutions.
Commercial software frequently has more vulnerabilities than custom software.