No application developer wants to deliberately inject a vulnerability into their application. The crux of the security issue is that they are generally too busy trying to make an application development deadline to manually hunt through all their code looking for vulnerabilities. More often, they are hoping someone more focused on testing or quality assurance […]
No application developer wants to deliberately inject a vulnerability into their application. The crux of the security issue is that they are generally too busy trying to make an application development deadline to manually hunt through all their code looking for vulnerabilities. More often, they are hoping someone more focused on testing or quality assurance will discover that vulnerability before the application goes into production.
Aiming to plug that security gap in the application development process, ShiftLeft came out of stealth mode today to unfurl a namesake cloud service that can be invoked to automatically identify potential security threats to any version of an application as it is being developed.
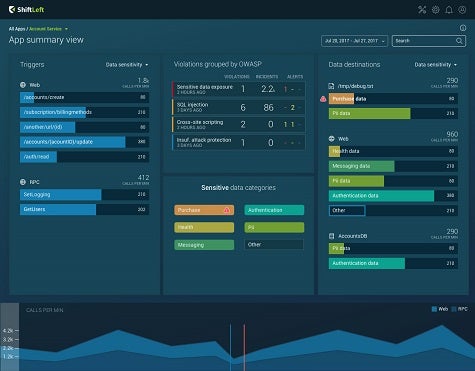
ShiftLeft CEO Manish Gupta says the company is providing a security-as-a-service (SECaaS) capability via security software running on Amazon Web Services (AWS) that automates the threat detection process by gathering all the security-related aspects of a Java application or microservice to create what Gupta describes as the Security DNA for each version of the application. That data is then used to create a “microagent” that gets inserted in the application runtime to generate security alerts and warnings any time that application gets updated.
“We’re allowing the developer to get to the root cause of any security issue,” says Gupta.
The result, adds Gupta, is a shifting to the left that makes the developer a lot more responsible for security, also known as DevSecOps, within the context of any continuous integration/continuous development (CI/CD) process. The more efficient that process becomes, the less time the rest of the IT team will need to spend remediating those vulnerabilities later.
As organizations look to speed up the rate at which they are building and deploying applications, very few of them have been able to address security issues in a meaningful way. There are now arguably more insecure applications being deployed than ever. The challenge and the opportunity facing IT organizations is to find some way to address as many of those security issues as possible before those applications ever get deployed.
MV
Michael Vizard is a seasoned IT journalist, with nearly 30 years of experience writing and editing about enterprise IT issues. He is a contributor to publications including Programmableweb, IT Business Edge, CIOinsight and UBM Tech. He formerly was editorial director for Ziff-Davis Enterprise, where he launched the company’s custom content division, and has also served as editor in chief for CRN and InfoWorld. He also has held editorial positions at PC Week, Computerworld and Digital Review.









