The Best Security Advice from Leading Experts One of the fundamental problems with IT security is that the IT environment is becoming more complex, while both the volume and types of attacks that IT organizations need to defend against continue to grow. All that complexity increases the overall attack surface to be defended, which by […]

The Best Security Advice from Leading Experts

One of the fundamental problems with IT security is that the IT environment is becoming more complex, while both the volume and types of attacks that IT organizations need to defend against continue to grow. All that complexity increases the overall attack surface to be defended, which by definition means more vulnerabilities than ever can be exploited.
To help IT organizations discover those vulnerabilities, SafeBreach this week launched a namesake platform that allows IT organizations to use an automated playbook to launch scripted attacks to discover where IT vulnerabilities lie. SafeBreach CEO Guy Bejerano says SafeBreach has taken years of security research and encapsulated it in the form of a playbook that allows its platforms to launch an artificial attack. The platform then discovers which vulnerabilities are being exploited in those attacks, which allows IT organizations to remediate those issues before they are exploited by real cybercriminals.
Bejerano says as new attacks are developed, SafeBreach will continue to update its platform. That in effect creates something of a spy versus spy cycle of updates between SafeBreach and the hacking community, says Bejerano.
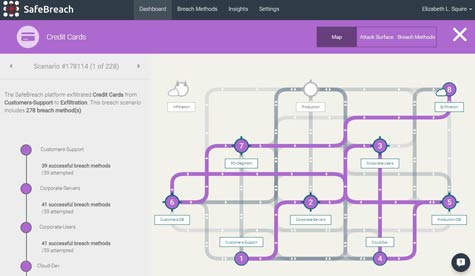
In general, Bejerano notes that the vast majority of attacks make use of relatively simple exploits. The trouble is that given the complexity of IT environments today, it’s hard for IT organizations to discover when a vulnerability that is commonly exploited is introduced into their IT environment.
SafeBreach doesn’t automate the remediation of those vulnerabilities. But it does provide access to information that IT organizations need to prioritize their IT security efforts. After all, not everything in an IT environment can be secured equally well. But when it comes to critical business assets, there’s no real acceptable excuse for not at least making a best effort to eliminate the vulnerabilities that cybercriminals routinely exploit. That may not prevent them from coming up with more innovative attacks, but it may make their task just difficult enough that they will go look for an easier target somewhere else.
MV
Michael Vizard is a seasoned IT journalist, with nearly 30 years of experience writing and editing about enterprise IT issues. He is a contributor to publications including Programmableweb, IT Business Edge, CIOinsight and UBM Tech. He formerly was editorial director for Ziff-Davis Enterprise, where he launched the company’s custom content division, and has also served as editor in chief for CRN and InfoWorld. He also has held editorial positions at PC Week, Computerworld and Digital Review.










