Cisco is sharing the results of a survey about the overall state of network security in the enterprise worldwide.
The survey – the results of which were announced in conjunction with the announcement of its partnership with other vendors to create validated secure borderless network systems – looked at the security processes of companies in the United States, Germany, China, India and Japan. Specifically, the survey delved into the IT security issues related to tracking vulnerabilities and policy enforcement in the corporate environment.
More than 500 IT decision makers from the five target countries took part in the survey. Interestingly, security in the United States, China and India is achieved using a multipronged approach, with companies incorporating more than one technology to track vulnerabilities. But despite the greater attention to security, respondents from these countries regularly find employees are using unauthorized devices or unsupported applications on their network, resulting in information loss.
Social networking was the largest offender, with 68 percent of respondents reporting unauthorized Facebooking (or other online socializing).
What may be the most telling findings, however, are those that show how important security issues are relative to hiring and keeping good employees. The survey reveals a feeling among its respondents, especially those in China and India, that overly strict security policies can have a negative impact on the hiring and retention of employees who are under the age of 30 – a whopping 71 percent, in fact.
And yet, more than half of the survey respondents said they would allow personal devices on the corporate network within the next year, despite the potential security risks.
Both of these statistics show that many IT decision makers are apt to turn a blind eye to seemingly non-threatening but nonetheless real security breaches in the name of employee satisfaction, especially those employees under 30. Do they think employees over 30 are the only population posing a security risk? What is it about employees under 30 that makes them immune to security policies and impervious to scrutiny?
I can understand that younger employees may be perceived to be more in tune with cutting-edge technologies, but that’s not always the case. Sometimes, experience is the greatest teacher. And experience is the one thing many of these under-30 employees lack.
It seems counterintuitive to implement tight security policies and turn around and ignore them to keep employees happy. Ensuring the security of corporate information should be the IT decision maker’s highest priority.

Click through to see more findings from a recent survey by Cisco Systems.
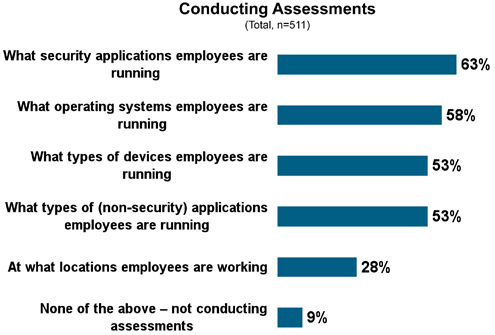
And the rest probably soon will be.
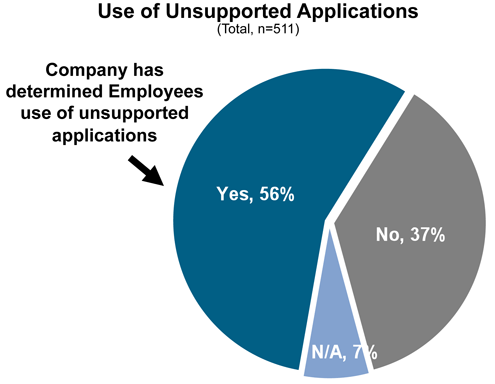
It’s nice to validate what you have always suspected.
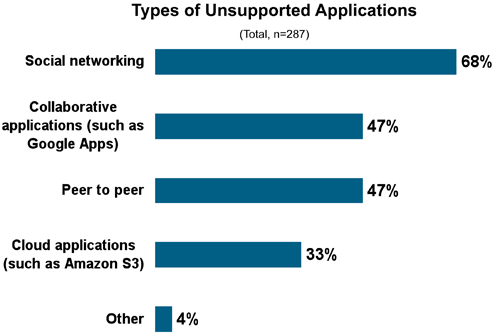
The next great security threat raises its head.
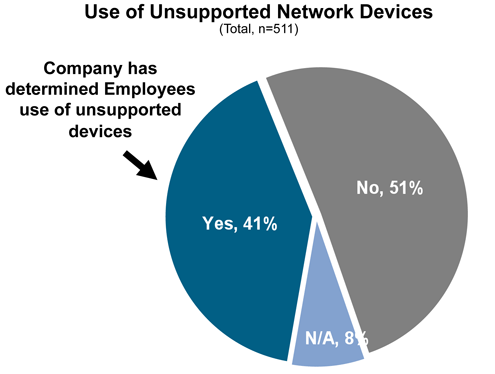
This trend will grow as employees continue to buy more personal technology gear.
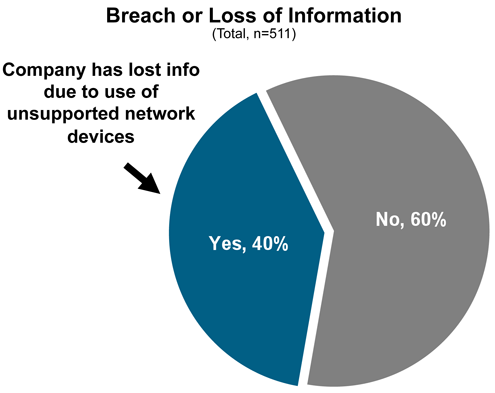
Almost half have already experienced some sort of data loss.
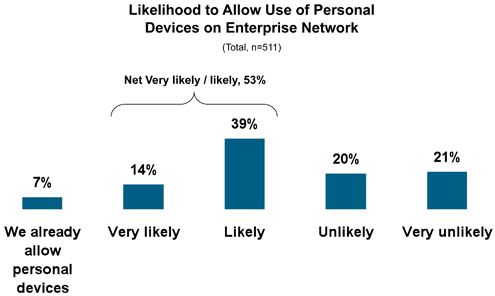
The days when IT could just say no are coming to a close.
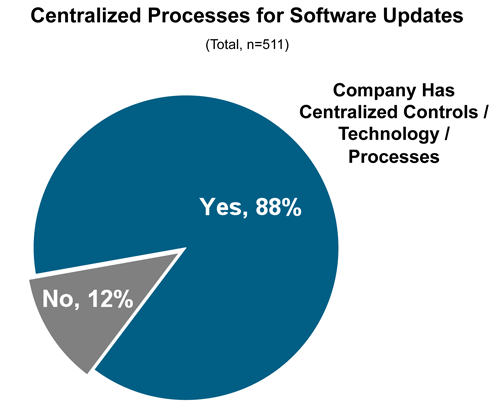
The days of visiting each PC to update software are long gone.
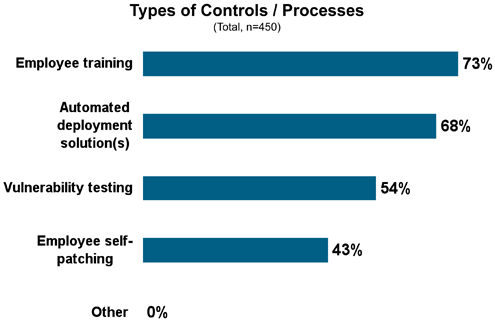
No need to waste expensive IT talent on software updates.
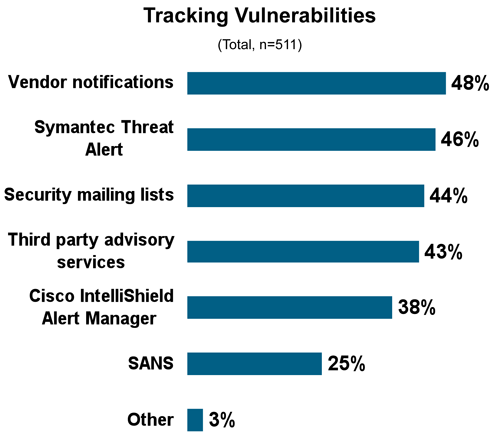
Vendor notifications are closely followed by Symantec threat alert and mailing lists.
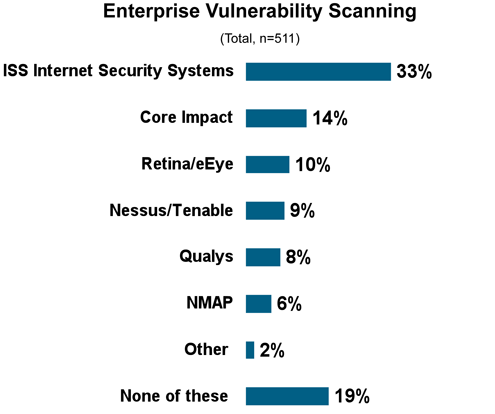
ISS is clearly the market leader when it comes to scanning.
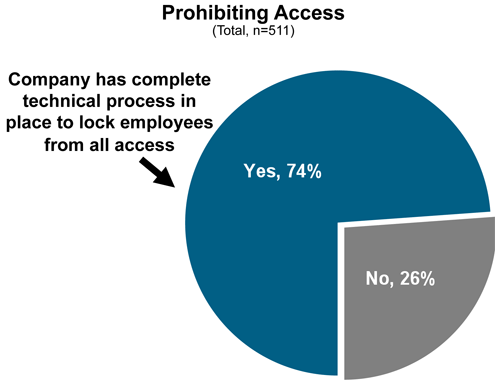
The good news is that security organizations are not wholly unprepared.
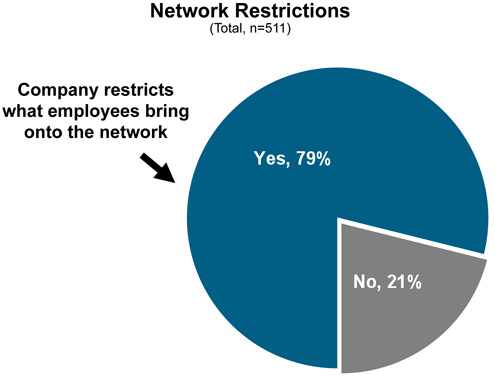
But employees are getting smarter about circumventing those rules.
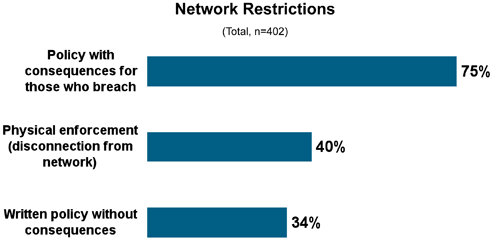
The consequences might not be enough to deter the behavior.
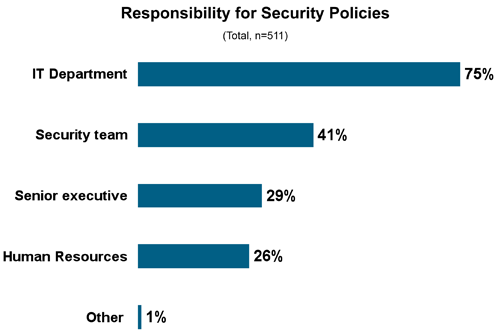
And enforcement may vary by employee.
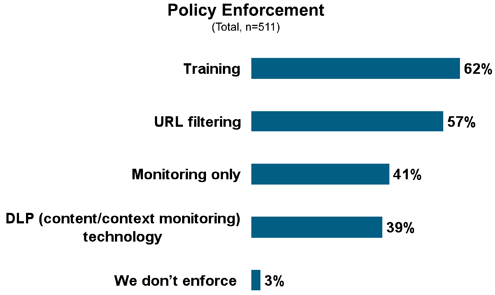
Most IT organizations prefer a nonconfrontational approach.
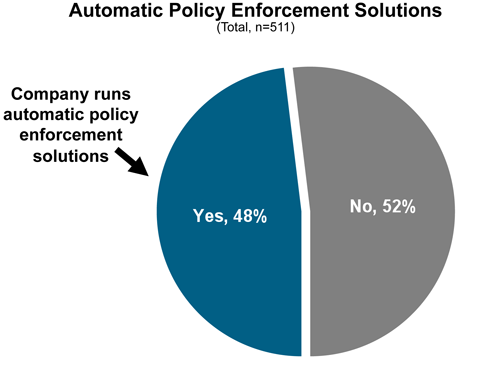
Network access control (NAC) systems will soon be required everywhere.
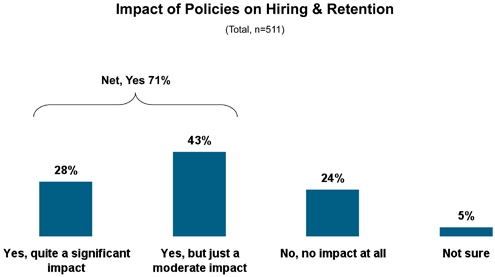
This is probably the number-one reason IT departments take a passive approach.
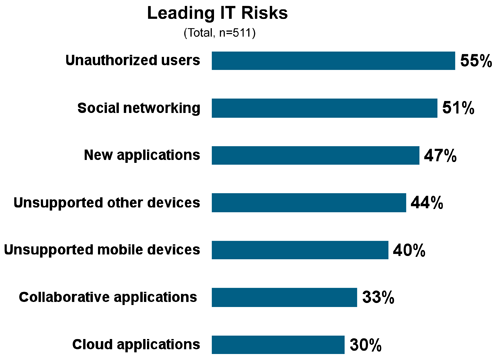
And yet, usage of these application and devices continues to grow.
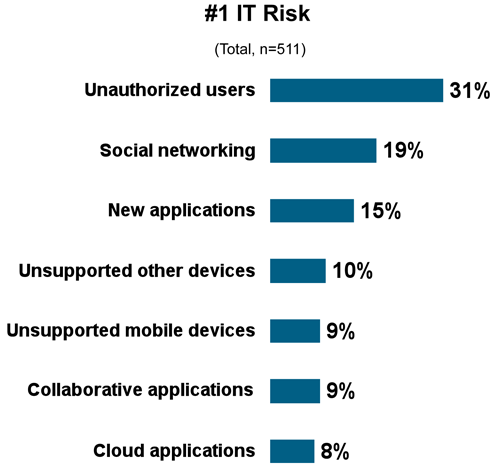
If any device can connect, you don’t know who’s actually on the other end.




























