While most IT organizations are resigned to the fact that they will experience a significant security incident in the next three years, the vast majority are unprepared to deal with its consequences.
Those are the findings of a recent survey of 200 IT security professionals conducted by Trusted Strategies on behalf of Solera Networks, a provider of a network forensics appliance.
The survey finds that 82 percent of those surveyed expect to have a significant security issue in the next three years, but 52 percent admitted that their organization is not ready to handle such an issue. And 35 percent said they currently lack an up-to-date security response plan. Worse yet, 64 percent said they lack the tools to determine the full scope of a security incident, and 20 percent said it would be impossible to determine the full scope of such an incident.
Pete Schlampp, vice president of marketing and product management for Solera Networks, says that as the security landscape gets more threatening and complex to manage, most IT organizations are poorly equipped to deal with such threats.
In fact, the major concern for IT organizations seems to be actual systems outages and the length of time it takes to recover a system if it crashes. This suggests, says Schlampp, that some IT organizations might be too focused on parochial concerns rather than on how the malware on their system might actually be affecting the business, especially when it comes to theft of data.
Obviously, the convergence of security and IT operations is critically important. But the real challenge, says Schlampp, is first accepting the fact that some sort of security incident is going to happen and then putting in place a holistic approach to managing the problem that not only discovers all the IT issues at hand, but also all the potential ramifications that breach could have on the business. Only then will IT organizations really be pursuing a true risk-based approach to security management.

Click through for results from a survey conducted by Solera Networks on network security.
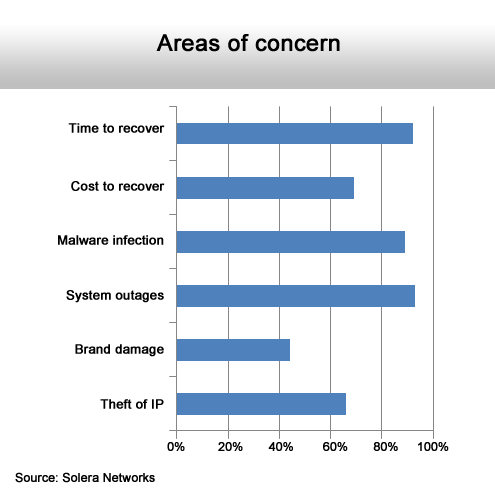
IT, rather than business, issues dominate.
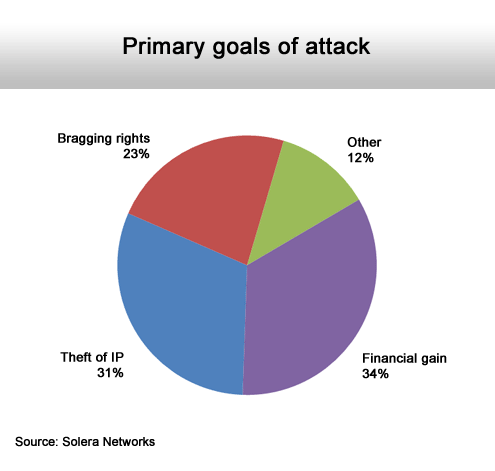
Attacks are motivated by money.
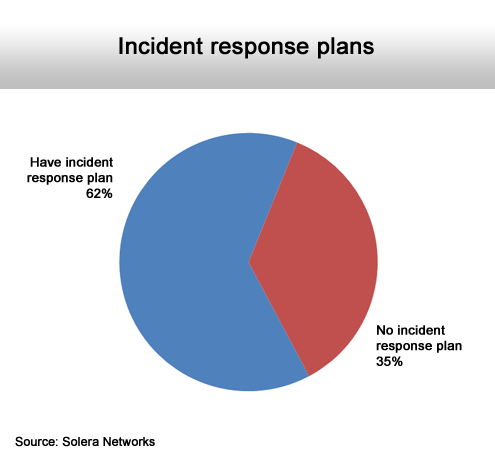
Most have one, but confidence in them is another matter.
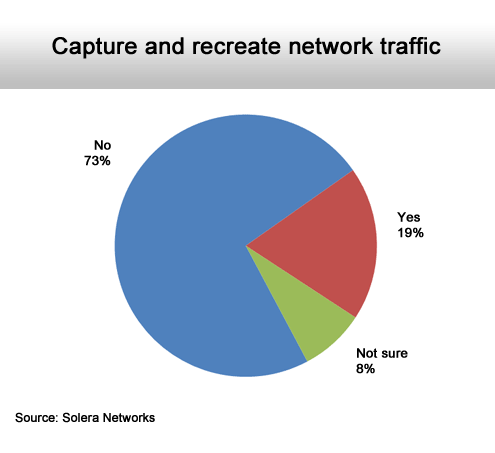
There is no crime trail to follow.













