Venafi, a leading cyber security company in next-generation trust protection, recently announced the results of in-depth research by its Threat Center team into how Edward Snowden successfully breached the National Security Agency (NSA). After months of review, analysis and peer feedback, this research reveals that the contract worker leveraged valid credentials as a low-level system administrator to fabricate cryptographic keys and digital certificates, which he then used to access and steal classified information and U.S. intellectual property. The NSA’s inability to detect or respond to anomalous key and certificate activity on its network allowed him to infiltrate systems and exfiltrate data without being detected.
Click through for a closer look at how NSA security was breached and how it could happen to your organization, as identified by Venafi.
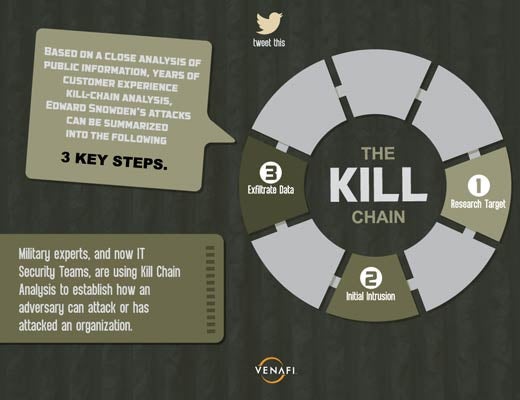
Military experts, and now IT security teams, are using Kill Chain analysis to establish how an adversary can attack or has attacked an organization.
Just like any government contractor, Edward Snowden was issued a CAC smart card with digital certificates and keys. As an administrator, he was also issued SSH keys for systems he was required to administer. This allowed Snowden to have valid access to some data and understand what else was out there.
As described in testimony by General Keith Alexander, Edward Snowden fabricated digital keys because of the NSA’s failure to detect anomalies. He used his authorized access to create new keys, obtain unauthorized keys, and create trust for new keys.
To get data out unnoticed, Edward Snowden needed to transfer data between systems. The transfer needed to go undetected, so he encrypted his data transfer sessions using self-signed certificates.
What attackers are looking for.
17K keys and certificated per enterprise.
Over half of all enterprises don’t know where keys and certificated are or how to use them.
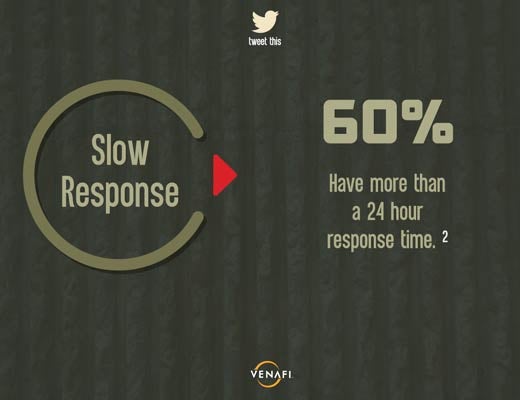
Sixty percent have more than a 24 hour response time.
There has been a 10x increase in malware digitally signed with a compromised or stolen digital certificate.
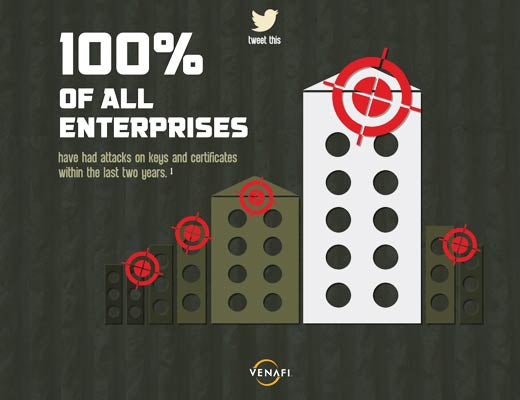
Your organization is a target and cannot hide. All enterprises have had attacks on keys and certificates within the last two years.
If the most secure organization in the world can be attacked, guess who’s next.