Hot New Security Products Debuting at RSA Conference 2016 As is the case with almost any IT initiative these days, security is a major concern with the Internet of Things (IoT). The simple fact is that digital criminals have become quite adept at exploiting even the simplest of vulnerabilities in ways that can wreak havoc. […]

Hot New Security Products Debuting at RSA Conference 2016

As is the case with almost any IT initiative these days, security is a major concern with the Internet of Things (IoT). The simple fact is that digital criminals have become quite adept at exploiting even the simplest of vulnerabilities in ways that can wreak havoc.
At the RSA 2016 conference this week, Barracuda Networks unveiled a new series of firewalls specifically designed for IoT environments. Klaus Gheri, vice president of network security for Barracuda Networks, says that the Barracuda NextGen Firewall S-Series makes use of a small Barracuda NextGen Firewall Secure Connector 1 (SC1) appliance that utilizes a proprietary Barracuda IPsec protocol to communicate back over a virtual private network (VPN), with a Barracuda NextGen Secure Access Concentrator that is a virtual gateway residing in either a public or private cloud.
Administrators can also invoke an Automatic Network Setup feature to define a single, large network that is automatically partitioned into smaller subnets, which then are automatically assigned to a particular SC1 appliance.
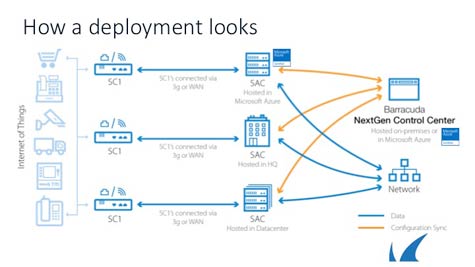
Gheri says the number of endpoints that can be hooked up to an SC1 appliance depends on the IoT use case. A medical device might generate so much data that it requires its own SC1 appliance. In other cases, a dozen or more endpoints might only generate data intermittently. The crucial thing is to employ a distributed approach to security that leverages the economics of the cloud on the back end, while keeping relatively low the cost of deploying an appliance as close to the endpoint as possible.
Many IT organizations think that applying IT security in an IoT environment should be the same as a traditional data center. But, says Gheri, IoT environments are significantly different in terms of both scale and how data flows across the network. The challenge, of course, is maintaining overall security when the nature of the data flowing across those IoT environments tends to vary widely from one implementation to another.
MV
Michael Vizard is a seasoned IT journalist, with nearly 30 years of experience writing and editing about enterprise IT issues. He is a contributor to publications including Programmableweb, IT Business Edge, CIOinsight and UBM Tech. He formerly was editorial director for Ziff-Davis Enterprise, where he launched the company’s custom content division, and has also served as editor in chief for CRN and InfoWorld. He also has held editorial positions at PC Week, Computerworld and Digital Review.










