GFI Software™ recently released its VIPRE® Report for August 2012, a collection of the 10 most prevalent threat detections encountered last month. In August, GFI threat researchers also examined the privacy of users downloading mobile apps released by both the Barack Obama and Mitt Romney U.S. presidential campaigns. Researchers also uncovered a variety of new attacks targeted at Android™ device owners including phony antivirus programs and a fake Adobe® Flash® Player application.
“While issues with mobile security are a relatively new phenomenon, it does not mean that there are not already a large number of security pitfalls that users should avoid,” said Christopher Boyd, senior threat researcher at GFI Software. “Avoiding mobile malware often requires the same preventative tactics associated with traditional malware such as verifying the legitimacy of any unsolicited emails or hyperlinks before installing an unknown application or submitting personal information. However, as we saw this month, even legitimate mobile applications can pose a threat to privacy if users do not investigate before granting permissions to gather data.”
Click through for more on the personal data and permissions required for presidential campaign apps and the top 10 threats for August, 2012, as identified by GFI Software.
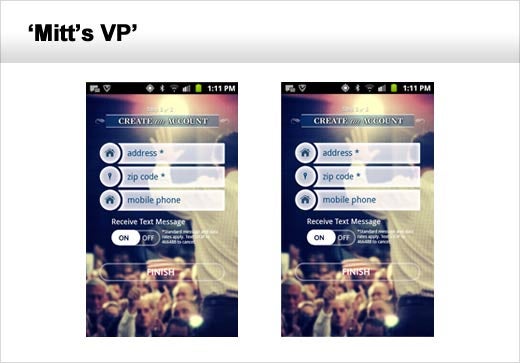
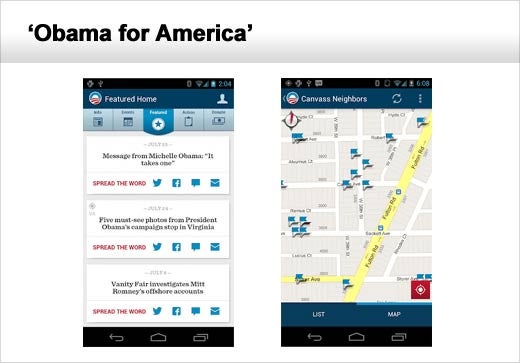
The “Obama for America” and “Mitt’s VP” smartphone applications were found to have a number of significant privacy issues that went unnoticed by users who did not read the terms of service agreements before using either application.
In order to use the Romney campaign’s app, users had to sign in through their Facebook® account or to provide personally identifiable information such as their name, email and home address. Users who opted to sign in through Facebook gave the app permission to post on their profile page on their behalf and to collect even more data from their Facebook friends. The application was also found to collect other information such as the device ID, carrier and phone number as well as GPS and cell locations.
There were two other permissions this app seeks that caught GFI’s attention, including access to the audio recording features of a mobile phone and its camera. The app doesn’t appear to take advantage of those features now, so why does it need those permissions?
The Obama campaign’s application required users to allow the app to gather information such as GPS location as well as the names and phone numbers found in the user’s contact list, call and message logs, data on other installed apps and the contents of the phone’s SD card if present. The user was then presented with information on registered voters in the area before being encouraged to canvass the neighborhood on behalf of the campaign. Furthermore, this app constantly collects user location information.
Mobile users also drew the attention of cyber criminals in August with the OpFake Trojan being distributed under the guise of the Adobe Flash Player, which is no longer being developed or supported on mobile browsers. Furthermore, some versions of the fake application were bundled with adware, which rooted the device and downloaded a fake version of the real Flash Player application. The adware program then performed a number of malicious tasks including the theft of the user’s phonebook contacts for advertising purposes and the deployment of pop-ups on the user’s screen.
Other Android users encountered a number of fake mobile anti-virus applications masquerading as mobile applications provided by legitimate anti-virus companies. The fake applications contained a Boxer malware program that sends SMS messages to a premium number before redirecting the user to another site.
GFI’s top 10 threat detection list is compiled from collected scan data of tens of thousands of GFI VIPRE Antivirus customers who are part of GFI’s ThreatNet™ automated threat tracking system. ThreatNet statistics revealed that Trojans and adware dominated the list with each taking four of the top 10 spots.
| Detection | Type | Percent |
| Trojan.Win32.Generic | Trojan | 34.00 |
| Trojan.Win32.Sirefef | Trojan | 10.04 |
| Yontoo (v) | Adware (General) | 2.13 |
| GamePlayLabs | Adware (General) | 4.16 |
| GameVance | Adware (General) | 1.20 |
| Wajam | Adware (General) | 1.55 |
| Trojan.Win32.Ramnit.c(v) | Trojan | 0.89 |
| Worm.Win32.Downad.Gen(v) | Worm.W32 | 0.89 |
| INF.Autorun(v) | Trojan | 0.79 |
| Virus.Win32.Sality.at(v) | Virus.W32 | 0.66 |