Thanks to widespread usage of Apple Siri and Cortana on Windows, end users are starting to regularly employ conversation interfaces to query applications. Now ThinAir is bringing support for a similar conversation interface capability to IT security software.
Announced today at the Gartner Symposium/ITxpo 2017 conference, the latest 2.0 version of the company’s namesake platform for investigating insider threats can now be invoked using a conversational interface that allows IT security personnel to employ spoken words to determine, for example, who accessed which file, and when.
ThinAir CEO Tony Gauda says it gathers metadata from all the content strewn across the enterprise that enables IT organizations to determine not only what types of content have been generated, but also who in the organization accessed it using a built-in search interface. The goal, says Gauda, is to reduce the amount of time it takes to investigate a breach. Today, Gauda says, it takes on average 191 days for an organization to discover the source of a breach, which is way too long to have any effect on implementing a meaningful response.
“Most of what they have is access to tangential indicators of compromise,” says Gauda.
The addition of a conversation interface, says Gauda, should reduce the amount of time required to investigate who accessed applications down to a few minutes.
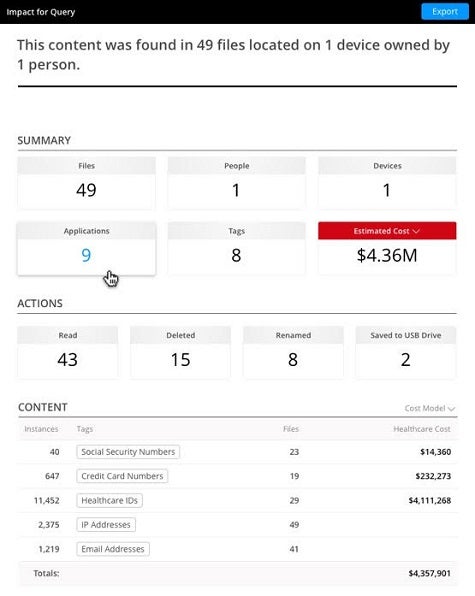
Other new capabilities in ThinAir 2.0 include an impact analysis tab for determining the potential scope of a breach and the ability to onboard new users in under a minute.
Most of what passes for IT security today is focused on preventing breaches. But in an age when breaches are a regular occurrence, the ability to determine when and where a breach might have occurred is often the difference between losing days if not weeks of IT productivity versus getting on with real business.