IT organizations can employ a lot of tools to manage policies that can be applied to almost anything in the IT environment. But given the complexity of the IT environment, it turns out figuring out exactly what policy to create and when and where to apply it is a major challenge.
To address that challenge, Illumio today added a set of visualization and discovery tools to an Illumio Adaptive Security Platform for microsegmenting traffic in a data center that makes it possible to both identify dependencies in an IT environment and then generate the appropriate management or IT security policy.
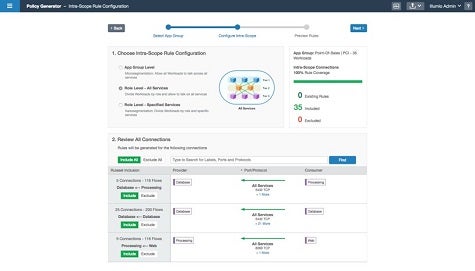
Designed to provide microsegmentation capabilities within a data center to better isolate application workloads, Chris Westphal, head of product marketing for Illumio, says version 2.0 of the Illumio Adaptive Security Platform is being enhanced with a Policy Generator module that can be employed to determine the relationship between applications and their underlying infrastructure dependencies. In addition, Illumio is making available an Explorer tool through which administrators can identify network traffic patterns by querying Illumio Adaptive Security Platform. Based on those queries, the Explorer module will also make recommendations concerning where to apply policies, says Westphal.
Westphal says the ultimate goal is to allow IT organizations to apply those policies at scale.
“Policies have been around for a while,” says Westphal. “But IT organizations have not been able to apply them across thousands of workloads.”
As a pioneer in the development of visual-based policy management tools, Westphal says this upgrade advances the capabilities surrounding the Illumio microsegmentation platform by making it much simpler to determine where and when to apply policies.
In terms of applying microsegmentation in the data center, most IT organizations are still coming up to speed on the concept. The basic idea is that by controlling the flow of east-west traffic inside the data center, IT organizations can provide higher levels of security by potentially limiting the damage any malware infestation can cause, while also improving application performance. The paradox is that the more granular those segments become inside the data center, the more difficult the overall IT environment can become to manage.