Tensions Between IT and Business Leadership Force New Approach to Delivering Technology When it comes to governance and compliance, the biggest issue facing IT organizations is often simply trying to figure out who owns the data that is being accessed. To solve that problem, Whitebox Security, within its WhiteOPS governance software, makes available crowdsourcing techniques […]

Tensions Between IT and Business Leadership Force New Approach to Delivering Technology

When it comes to governance and compliance, the biggest issue facing IT organizations is often simply trying to figure out who owns the data that is being accessed. To solve that problem, Whitebox Security, within its WhiteOPS governance software, makes available crowdsourcing techniques to allow IT organizations to query end users to determine who owns the data they are accessing.
Whitebox Security CEO Maor Goldberg says that before any kind of effective governance and compliance policy can be put in place, the internal IT organization needs to know who should actually have permissions to access that data. Unfortunately, that’s not as easy as it might seem. Employees change jobs inside organizations, and even when they leave the company, many of them still retain passwords to sensitive documents and applications.
In addition to providing the tools IT organizations need to manage compliance, Goldberg says Whitebox Security gives IT organizations the tools they need to establish a baseline from which to assess who in the organization should have access to which data. To that end, Whitebox Security has updated its WhiteOPS to add a portal and simplified entitlements and identities forensics. In addition, the new release includes best practices for governance that IT organizations can immediately leverage.
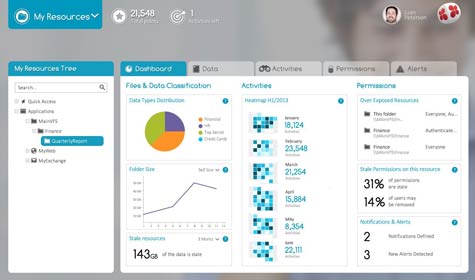
When it comes to governance, Goldberg says it’s pretty clear that far too many users are running around with privileged access to data that they either shouldn’t have or no longer need. Each one of those users represents a potential insider threat that is likely to throw up a red flag any time a compliance audit is conducted.
Naturally, the IT organization will bear most of the blame for that compliance violation, unless, of course, they can proactively find a way to avoid ever allowing that violation to occur in the first place.
MV
Michael Vizard is a seasoned IT journalist, with nearly 30 years of experience writing and editing about enterprise IT issues. He is a contributor to publications including Programmableweb, IT Business Edge, CIOinsight and UBM Tech. He formerly was editorial director for Ziff-Davis Enterprise, where he launched the company’s custom content division, and has also served as editor in chief for CRN and InfoWorld. He also has held editorial positions at PC Week, Computerworld and Digital Review.










