Interest is rising in microsegmentation as a means for better securing network traffic moving east to west in a data center. The basic idea is that if any node in the data center gets compromised, the only other nodes that could be exposed to malware are the nodes that share the same microsegmented network connection. […]
Interest is rising in microsegmentation as a means for better securing network traffic moving east to west in a data center. The basic idea is that if any node in the data center gets compromised, the only other nodes that could be exposed to malware are the nodes that share the same microsegmented network connection.
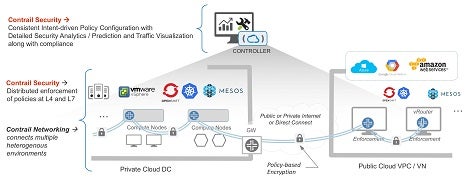
To make it less costly for IT organizations to achieve that level of security, Juniper Networks today announced a Contrail Security offering that is available as open source software.
Pratik Roychowdhury, senior director of product management for Contrail at Juniper Networks, says Contrail Security is a complement to the Open Contrail network virtualization software that Juniper Networks has previously made available as an open source project.
Via Contrail Security software, Roychowdhury says, IT organizations will be able to more simply implement policies across a microsegmented network spanning multiple environments, including public clouds, virtual machines, clusters based on Kubernetes container orchestration software and the OpenStack cloud management framework.
Because Contrail Security includes visualization, analytics and orchestration tools, Roychowdhury says, Contrail Security makes it simpler to manage microsegmented networks than rival network virtualization platforms. Contrail Security can also be integrated with third-party virtual firewalls, says Roychowdhury.
“We’re reducing operational complexity,” says Roychowdhury.
It’s still early days in terms of adoption of microsegmentation across virtual networks. But given the level of sophisticated security threats IT organizations now face, the need to contain the amount of damage that any malware can inflict is becoming a much higher priority.
MV
Michael Vizard is a seasoned IT journalist, with nearly 30 years of experience writing and editing about enterprise IT issues. He is a contributor to publications including Programmableweb, IT Business Edge, CIOinsight and UBM Tech. He formerly was editorial director for Ziff-Davis Enterprise, where he launched the company’s custom content division, and has also served as editor in chief for CRN and InfoWorld. He also has held editorial positions at PC Week, Computerworld and Digital Review.