
Seven Ways to Improve Cybersecurity Through Behavioral Analysis

As part of an effort to create a massive IT security community, IBM today announced it will share ongoing security intelligence in real time along with security data that it has collected over the last 20 years via an IBM X-Force Exchange portal.
Diana Kelley, executive security advisor for IBM, says that the company is trying to create a community through which IT security professionals can collaborate to better identify threats and share alerts.
To that end, IBM is contributing anonymized security data gathered from more than 15 billion security events it monitors per day, security intelligence gathered via 270 million endpoints and 25 billion web pages and images, reputation data on 1 million known IP addresses, and data it has collected from over 8 million spam and phishing attacks.
Kelley notes that it is apparent that digital criminals regularly collaborate with one another. Using the IBM X-Force Exchange portal, Kelley says that IBM is trying to foster a similar level of collaboration among IT professionals. In the future, Kelley says that IBM plans to reveal which IT security vendors and organizations it has invited to participate in the community.
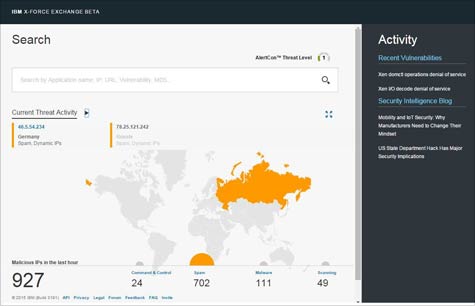
In the meantime, IBM is exposing a library of application programming interfaces (APIs) that organizations can use to launch queries across the portal, machines and applications, allowing businesses to operationalize threat intelligence and take action. In addition, Kelley says IBM will provide future support for STIX and TAXII, which are emerging standards for automated threat intelligence sharing.
In general, Kelley notes that IT security has become a boardroom-level issue, because hackers are no longer just stealing credit cards. With digital criminals now targeting specific organizations and individuals, a global market for stolen intellectual property worth billions of dollars has emerged.
The end goal, says Kelley, is to identify potential threats, and also determine which threats are active and most lethal to any organization at any given time. Armed with that information, organizations could then more rapidly automate the remediation of vulnerabilities being exploited by digital criminals.
While there will never be perfect security, Kelley notes that by making it more difficult for digital criminals to succeed, the cost of launching attacks becomes increasingly prohibitive. Over time, that means that the number of individuals and organizations that can afford to launch such attacks should decline, says Kelley.
To achieve that goal, IBM is essentially trying to create an online workbench for IT security professionals. Ultimately, the goal would be to apply advanced analytics and even the IBM Watson platform to identify threats and remediate vulnerabilities long before the actual attack can be launched.
Obviously, it will take some time for this approach to IT security to fully mature. But as it does, IT organizations should take note of the fact that even in the days when pirates raided shipping vessels on the high seas, the best defense usually involved merchants looking to their own mutual defense.










