A new study from the United Kingdom that was conducted by the Ponemon Institute on behalf of IBM is illustrative of a worldwide challenge when it comes to enforcing IT security. The study of 115 C-level executives finds that while CEOs are increasingly placing more importance on data security, there is a significant gap between their perception of how good their organizations are at securing information and the perceptions of the rest of the executive management team.
The core issue, says Dr. Larry Ponemon, is that CEOs are still pretty divorced from the processes associated with managing security, which tends to give them a slightly distorted view of their company’s capabilities and what it takes to secure the organization.
The good news is that everybody seems to agree that spending money on security is a valuable and necessary endeavor, but not everybody seems to be on the same page concerning what the proper amount should be.

Click through for highlights of the Ponemon study on C-level executives’ concerns over security.
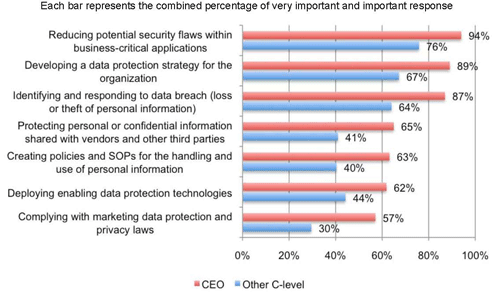
Security has become a much bigger issue for the CEO.
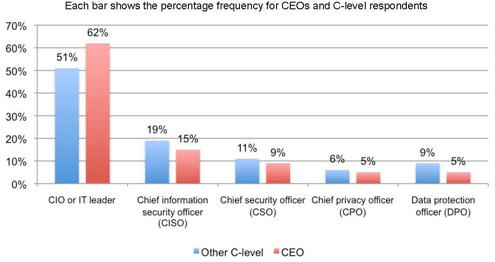
The responsibility for security lies mostly with internal IT.
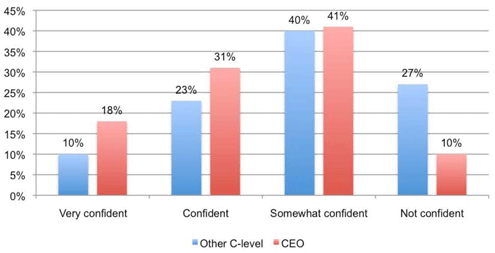
Confidence in security measures is not as high as it might be.
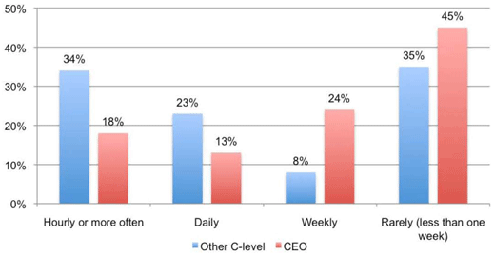
There are more attacks than most CEOs realize.
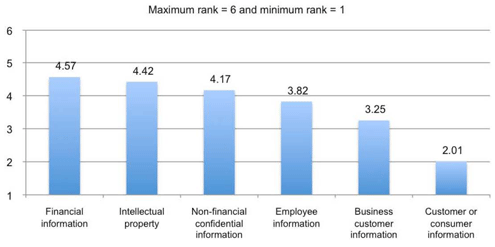
Financial data is seen as a lot more critical to protect than customer data.
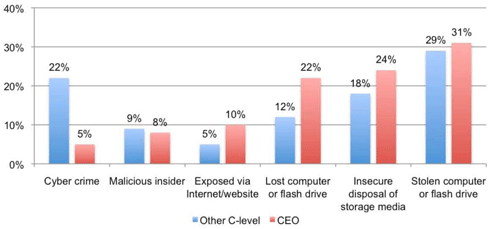
Stolen laptops or flash drives top the list of potential threats.
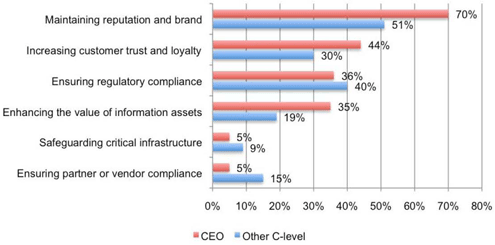
Damage to the brand is the top concern.
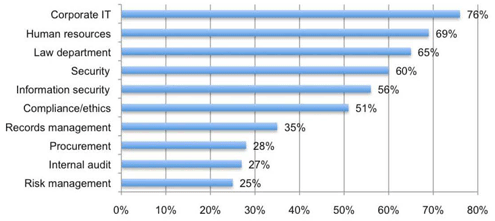
Corporate IT and human resources are the two departments charged most with securing data.
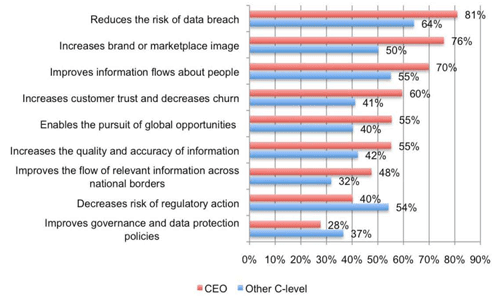
Reduction in breaches and better brand image top the perceived ROI of data security.
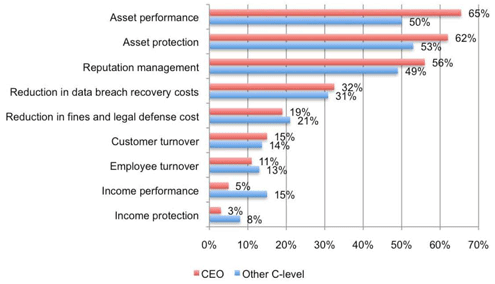
Asset performance and protection are metrics used to measure security ROI most.
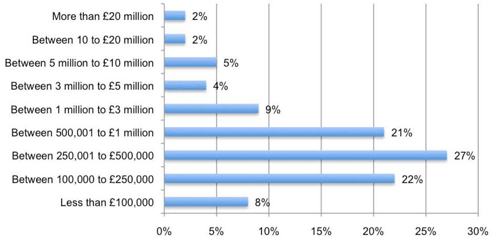
Relative to other security sectors, investments in data protection are small.
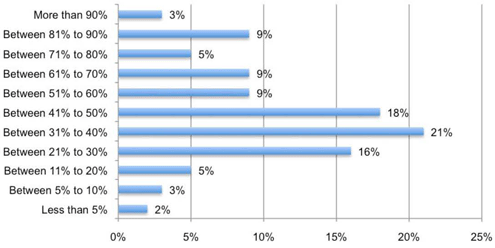
Most of the security budget goes to paying for existing solutions that deal with known threats.
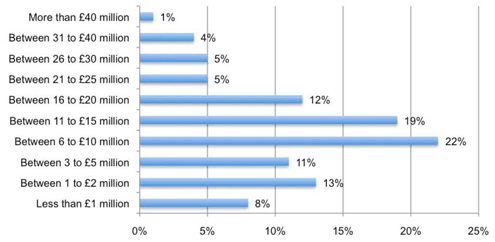
A pretty strong case for security ROI starts to emerge.
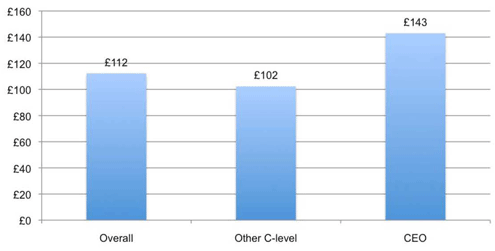
The cost of remediation is getting higher as more regulations come into effect.
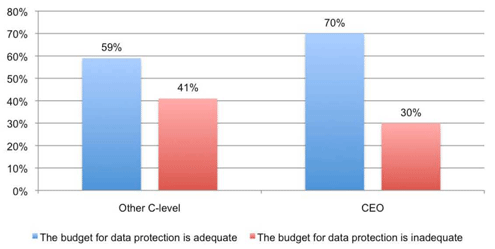
CEOs are out of step with the rest of the executive team.
























