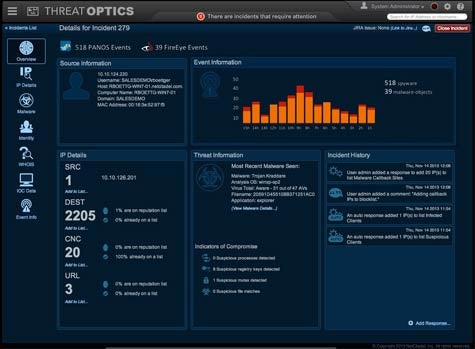
A world of difference exists between discovering a potential security threat and actually understanding the amount of potential harm it could cause.
Looking to give IT organizations access to a set of analytics applications that allows them to visually see how lethal any given security threat might be, NetCitadel this week made available NetCitadel ThreatOptics, an analytics application that gets applied against the threats discovered by the company’s security intelligence cloud platform.
NetCitadel CEO Mike Horn says NetCitadel ThreatOptics is designed to provide the context that is so often missing when trying to identify threats. The sheer volume of threats, says Horn, makes it exceedingly difficult to identify threats, such as advanced persistent threats, that are a lot more lethal than garden-variety malware.
NetCitadel ThreatOptics also integrates with multiple existing security devices, such as firewalls and web proxies, to help IT organizations respond to security threats in real time.
By providing an analytics capability, NetCitadel ThreatOptics reduces the security fatigue that so often results in IT organizations not actually discovering serious security threats because of the sheer volume of attacks they are trying to cope with every day.
The ultimate goal, says Horn, is to reduce the time it takes to automate the remediation of those threats. Once that capability is in place, Horn says the cost of launching a successful security attack starts to escalate for the purveyors of malware, who generally then focus their efforts on targets that are more easily compromised.
Existing security information event management (SIEM) tools provide ways to capture data about security threats. But Horn says the first generation of these tools doesn’t do much to help security teams verify and prioritize security threats. As a result, NetCitadel and a host of other security vendors are racing to deliver next-generation security intelligence services via the cloud.
Weeks, sometimes months, can go by before a security team discovers a security threat. While that security threat clearly represents an injury, the insult comes when it takes multiple days for the IT team to first understand the extent of that threat and then ultimately completely remediate the vulnerability.