How to Get IT, Security, and the Business on the Same Risk Page When it comes to compliance issues, IT organizations often find themselves in a difficult position. Usually, compliance mandates must be met, but the tools that IT organizations have at their disposal are often overly comprehensive and too complicated to deploy. Rather than […]

How to Get IT, Security, and the Business on the Same Risk Page

When it comes to compliance issues, IT organizations often find themselves in a difficult position. Usually, compliance mandates must be met, but the tools that IT organizations have at their disposal are often overly comprehensive and too complicated to deploy.
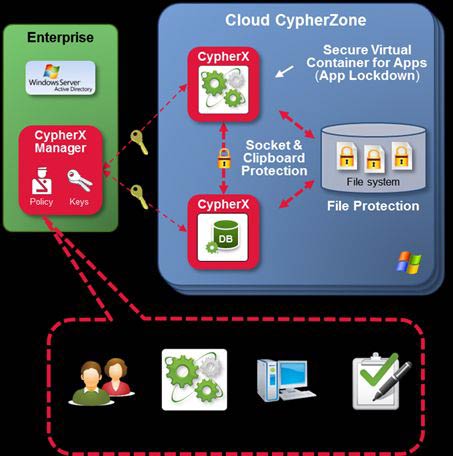
Rather than taking a shotgun approach to meeting compliance mandates, AFORE Solutions has come up with an approach that allows IT to focus on meeting compliance requirements for specific applications. CypherX wraps applications in a virtual container that encrypts all the data in that application while providing the mechanisms IT organizations need to granularly manage all the IT compliance policies associated with that application.
According to Jonathan Reeves, chairman and chief strategy officer for AFORE Solutions, CypherX takes advantage of the extensions that Intel included with its Westmere-class of Xeon processors, which added support for the Advanced Encryption Standard (AES). That approach, says Reeves, allowed AFORE to develop a virtual container that encrypts data in a way that has minimal impact on actual application performance.
When it comes to security and compliance, no one can really be sure what anyone is going to do with any piece of data. By applying encryption at the application level, Reeves says IT organizations can essentially digitally shred data at the first sign of trouble. The data itself can be accessed only by applications that have been certified by IT and are actually running on machines that the IT organization has validated.
In effect, Reeves says that instead of locking down a system, CypherX allows the IT organization to essentially lock down the application.
Encryption use is on the rise, since IT organizations have been tasked with finding a way to execute compliance policies. So it makes sense to manage encryption from the application layer down instead of trying to manage it from the storage system up.
After all, not all applications are created equal, so broadly applying encryption might not make the most sense. But since some applications clearly have more need to encrypt data than others, IT organizations need a way to apply encryption and compliance policies in a way that actually reflects the business value of the data stored within any particular application.
MV
Michael Vizard is a seasoned IT journalist, with nearly 30 years of experience writing and editing about enterprise IT issues. He is a contributor to publications including Programmableweb, IT Business Edge, CIOinsight and UBM Tech. He formerly was editorial director for Ziff-Davis Enterprise, where he launched the company’s custom content division, and has also served as editor in chief for CRN and InfoWorld. He also has held editorial positions at PC Week, Computerworld and Digital Review.