Much like in the streets of New York City in “Ghostbusters,” suspicious activity is happening in varying degrees all over the web. The relative risk of visiting a website in a “shady” neighborhood can vary dramatically depending on who is managing the “residents” there.
What many users may not realize is that the letters following the “.” in a website address represent a top-level domain (TLD) – essentially a “neighborhood” of addresses – maintained by a specific company or group. Ideally, TLDs would all be run by security-conscious operators who diligently review new domain name applications, and reject those that don’t meet a stringent set of criteria.
Unfortunately, the reality for many of these new neighborhoods is that they go unpoliced, like Slimer wreaking havoc on the 12th floor of the Sedgewick Hotel. To avoid getting slimed, businesses and consumers need guidance to understand how safe, or how shady, these new TLDs may be considered for web security purposes.
Courtesy of Blue Coat research, let’s take a closer look at the web’s shadiest neighborhoods.

There’s Something Strange in Your (Web) Neighborhood
Click through for a closer look at the web’s shadiest neighborhoods, as identified by Blue Coat.

Lax Policies
Lax policies in some managing organizations breed shady neighborhoods.
The dramatic rise in new TLDs can be attributed to a new generic top-level domains (gTLDs) initiative launched by the Internet Corporation for Assigned Names and Numbers (ICANN) in 2012. ICANN’s frequently asked questions document for gTLDs outlines the original goal for the initiative:
One of ICANN’s key commitments is to promote competition in the domain name market while ensuring Internet security and stability. New generic Top-Level Domains (gTLDs) help achieve that commitment by paving the way for increased consumer choice by facilitating competition among registry service providers. Soon entrepreneurs, businesses, governments and communities around the world will be able to apply to operate a Top-Level Domain registry of their own choosing.
Each new TLD is under the control of an organization that has to pay a $185,000 evaluation fee to ICANN and also has to prove that it has the infrastructure and expertise to run a new TLD registry.
Ideally, all of these new registries (and all of the country code registries) would exercise the same level of caution in who they allow to purchase domains in their new space – but many do not, and the bad guys know where to shop.

Explosion in New TLDs
There has been an explosion of new top-level domains in the past year.
In 2013-2014, over 600 new TLDs were approved, and the pace has continued in 2015. In early 2015, the count of valid TLDs was 795 (including the country codes), and by mid-August, the count was over 1000. As the sheer number of new neighborhoods on the web has skyrocketed, so have the opportunities for attackers.
For the sake of comparison, back in its early days, the web was limited to six normal TLDs and roughly 100 “country code” TLDs. This continued for over a decade, with a few additional TLDs being added in 1998, 2001, 2005 – some of which are likely familiar to many users (.info, .biz, .mobi, .name, .pro), and some less familiar (.aero, .asia, .cat, .coop, .int, .jobs, .museum, .tel, .travel, .post). The infamous “.xxx” was added in 2011.

Malicious Activity
Malicious activity continues to increase.
Dr. Egon Spengler might as well have been describing malicious web activity when he said, “Well, let’s say this Twinkie represents the normal amount of psychokinetic energy in the New York area. Based on this morning’s sample, it would be a Twinkie… thirty-five feet long, weighing approximately six hundred pounds.”
That’s a big Twinkie. And a big dose of malicious activity dominating shady TLDs, namely, scams, spam, suspicious activity and potentially unwanted software (PUS). Most of these websites are being leveraged by attackers in spam and scams and to distribute potentially unwanted software. Others are related to search engine optimization/ positioning or other “junk sites” that would be classified as suspicious.

A Limitless Supply of TLDs
Bad guys always need a new supply of domains to do bad things.
Previous Blue Coat research, “One-Day Wonders: How Malware Hides Among the Internet’s Short-Lived Websites,” explored in depth how many sites on the web only exist for less than 24 hours. The explosion of new TLDs has provided a nearly limitless supply of “one-day wonders” for the taking. Links to these locations are included in spam campaigns, and they are changed rapidly to increase the chances that they will evade security defenses before they are updated.
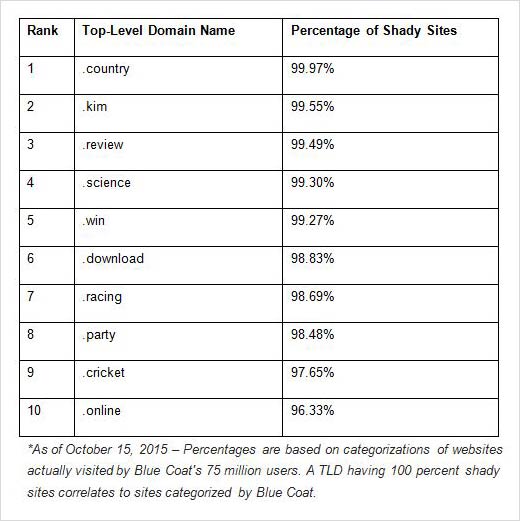
Top 10 Shady TLDs
The web’s top 10 TLDs with shady sites.
Based on analysis of web requests from more than 15,000 worldwide businesses and 75 million users, Blue Coat researchers have created a list rating the web’s shadiest TLDs. You’re bound to find your fair share of ectoplasmic residue (Ghost slime) polluting these neighborhoods.

Risky Activity
Fake video attacks are increasingly common as a successful threat targeting social media users.
In a different twist on a fake video attack, the highest-trafficked “.country” site observed by Blue Coat on a day in mid-June was part of a “shocking video” scam network.
This increasingly common scam leads visitors to a “teaser page,” usually designed to make them believe they are visiting YouTube, when in reality they are on a fake site that has no legitimate tie to YouTube. The non-working
video includes fake comments immediately below it from someone wanting
to know how to get the video to play, and someone else explaining that you have to “share” or “like” the video first, or take an online survey. When visitors follow these instructions, they either divulge personal data in the survey, or the scammers spam their Facebook friends.
Blue Coat sees this campaign frequently, often with sites that get hundreds of attempted visits per day, so people are clicking on it. Nearly all of that traffic is coming from Facebook, so the scammers’ scheme works.
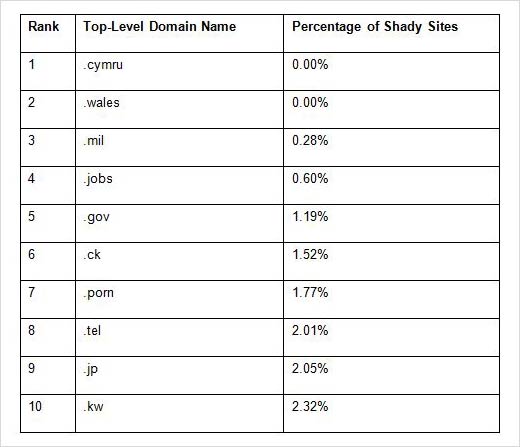
The ‘Safest’ Web Neighborhoods
This list includes the bottom 10 shady TLDs – or the “safest” TLDs, historically. All of these TLDs have less than 2 percent of their sites classified with shady ratings to date.
However, users should beware of reading too much into this section. Only a few of these have large numbers of sites in Blue Coat’s database. There are also no guarantees that TLDs that currently have lower risk levels will maintain them.
As good general-purpose TLDs, .tel and .jobs appear to be obvious targets for attackers in the future. In addition, .ck is a concern now that Blue Coat has publicly identified it as a fairly safe place, since whoever is running their registry may not have the resources to keep out the bad guys.

Minimize Business Risk
How to minimize risk for businesses.
Grab your jumpsuits and proton packs and, most importantly, be aware and vigilant about the online neighborhoods you visit. Even the “safest” TLDs are not without risk of threats from nefarious players. It remains as critical as ever to have strong digital security protection and policies in place.
Businesses should consider blocking traffic that leads to the riskiest TLDs, including .work, .gq, .science, .kim and .country. The remaining five TLDs in the top 10 shadiest TLDs list deserve similar consideration.

Minimize Consumer Risk
How to minimize risk for consumers.
Users should use caution when clicking on any links that have shady TLDs in them, if they encounter them in search results, email or social network environments. If unsure about the source, hover the mouse over a link to verify that it leads to the address displayed in the text of the link. Remember that you can “press and hold” a link on a mobile device (not just click) to verify that it leads to where it says it does.


















