It used to be that programmers created and launched annoying but mild virus and spam malware to show the world just how brilliant they were and to gain notoriety. Today, we live in a very different world where cyber threats and attacks are recognized as significant global, political and commercial challenges with serious financial and reputational consequences.
The cyber criminal community has evolved from pranksters, lone wolves, and organized gangs to nation-states and hacktivist groups whose primary results have been increased costs and lost productivity. As enterprises and governments connect literally everything to the Internet, the size of their attack surface has grown, opening more opportunities for cyber criminals. Many of their current exploits are going unnoticed.
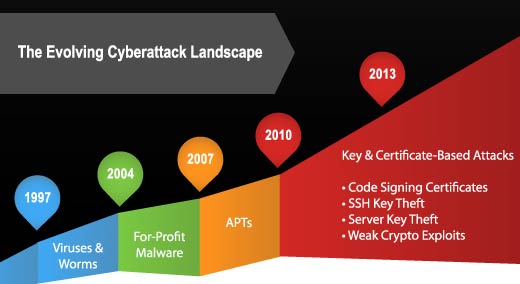
Here’s a closer look at the evolution of cyber attacks, identified by Venafi.
Click through for a look back at the last 16 years and the rise of cyber attacks, as identified by Venafi.
Sixteen years: from viruses, worms, DDoS, advanced persistent threats, to key and certificate-based attacks.
Viruses, Worms & DDoS – Damage Level: Disruption
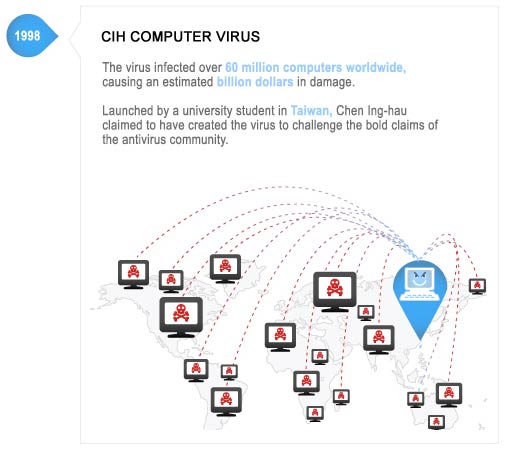
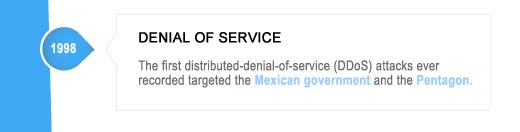
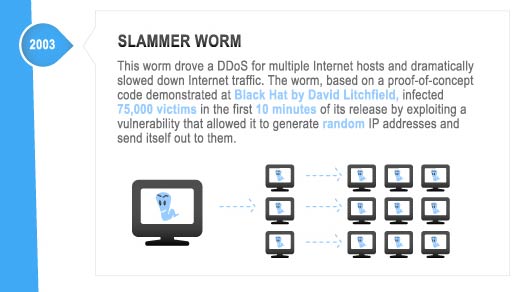
Viruses, Worms & DDoS – Damage Level: Disruption
Viruses, Worms & DDoS – Damage Level: Disruption
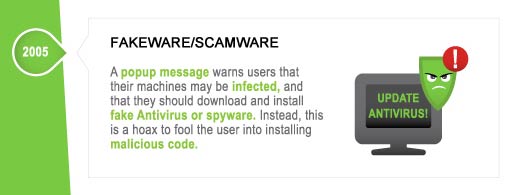
For-Profit Malware – Damage Level: Cybercrime
For-Profit Malware – Damage Level: Cybercrime
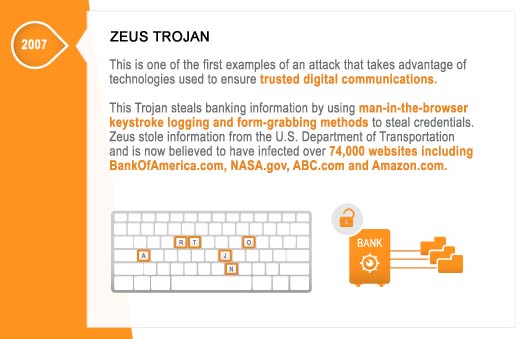
APTs – Damage Level: Cyber Espionage
APTs – Damage Level: Cyber Espionage
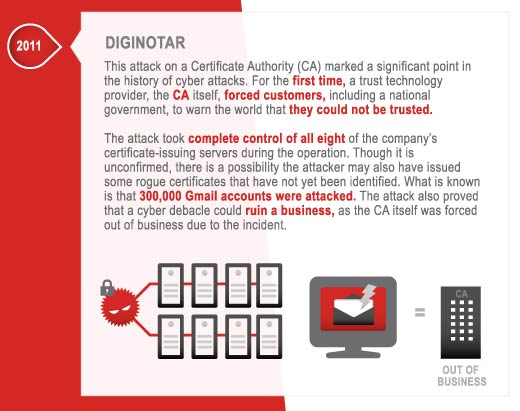
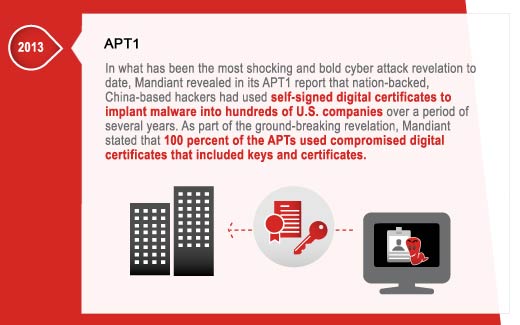
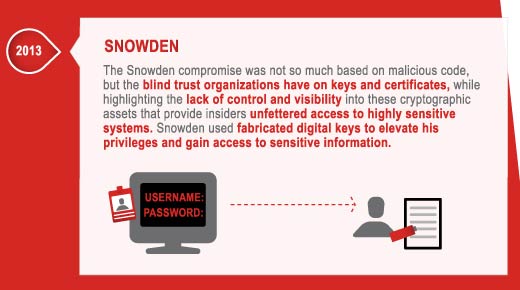
Code Signing Certificates, SSH Key Theft, Server Key Theft & Weak Crypto Exploits – Damage Level: World Without Trust
Code Signing Certificates, SSH Key Theft, Server Key Theft & Weak Crypto Exploits – Damage Level: World Without Trust
Code Signing Certificates, SSH Key Theft, Server Key Theft & Weak Crypto Exploits – Damage Level: World Without Trust
Code Signing Certificates, SSH Key Theft, Server Key Theft & Weak Crypto Exploits – Damage Level: World Without Trust
Code Signing Certificates, SSH Key Theft, Server Key Theft & Weak Crypto Exploits – Damage Level: World Without Trust
Code Signing Certificates, SSH Key Theft, Server Key Theft & Weak Crypto Exploits – Damage Level: World Without Trust
Code Signing Certificates, SSH Key Theft, Server Key Theft & Weak Crypto Exploits – Damage Level: World Without Trust
Code Signing Certificates, SSH Key Theft, Server Key Theft & Weak Crypto Exploits – Damage Level: World Without Trust
Code Signing Certificates, SSH Key Theft, Server Key Theft & Weak Crypto Exploits – Damage Level: World Without Trust
Code Signing Certificates, SSH Key Theft, Server Key Theft & Weak Crypto Exploits – Damage Level: World Without Trust
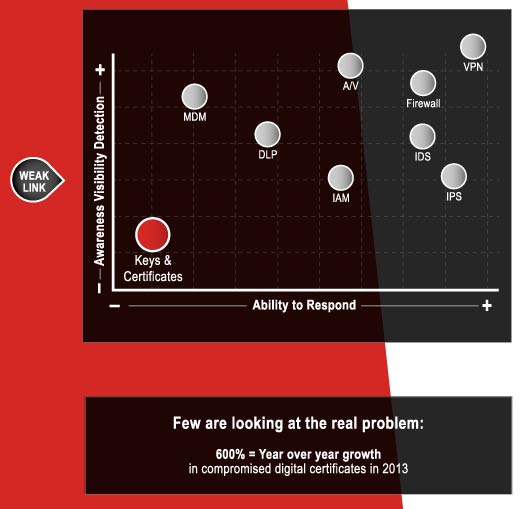
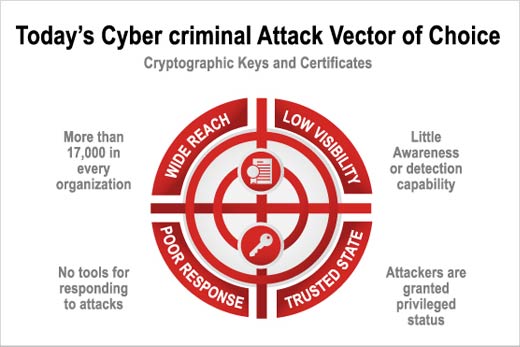
100 percent of over 2,300 global 2000 organizations surveyed acknowledged having attacks on keys and certificates in the last two years.
Today’s cyber criminal attack vector of choice.