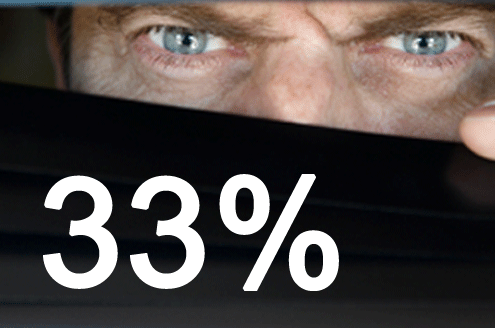
Normally I hate to start off with a reference to surveys, if only because the result can be an instant snooze for readers. This time, however, I’m making an exception. The reality is that the U.S. Government is under attack continuously by foreign interests, but less than two-thirds of respondents in a recent survey believe it.
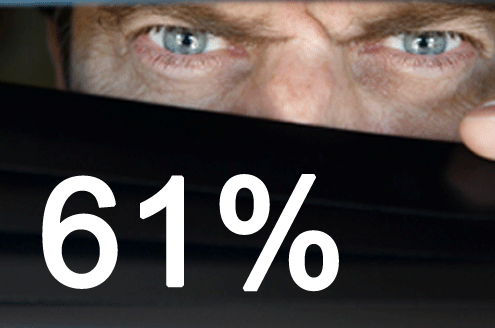
The survey, performed earlier this year and reported last week by the Clarus Research Group here in Washington, reported among other things that 61 percent of Federal IT managers view the threat of an attack from foreign nations against the U.S. in the next year as “High.” One wonders what these people, all Federal IT decision makers, consider to be a “threat.”
In the interests of full disclosure, this survey was commissioned by the IT security folks at Lumension. But there’s no reason to think the results were skewed by that. The fact is that foreign countries, either directly or through surrogates, are attacking the U.S. and have been for years. This is a reality that Federal IT managers have to deal with on a daily basis.
What’s equally important to realize is that many of the attacks on the U.S. are against private IT interests. Defense contractors, companies that provide critical infrastructure such as power companies and phone companies, and other federal contractors are under attack. Those attacks are aimed at gathering information, disrupting activities, looking for attack vectors against the US government, and even bringing critical infrastructure down in a coordinated attack.
Adding to the complexity is the fact that some foreign countries, notably China, are also attacking private companies for their intellectual property. We’re at war, and anything is fair game. What’s worse is that we’re at war without the weapons and defenses we need.
A telling response to the Clarus survey was one in which only about half of respondents felt that the newly appointed cyber security director would be able to make a difference. This is worrying, but not because of the reasons you may think. Remember, the U.S. government’s IT infrastructure is a maze of independent, unconnected systems purchased at different times for different requirements, and managed by people who are underpaid, overworked and given too little authority to accomplish their missions.
What this means is that changing direction with the current situation in Federal IT is like trying to steer an oil tanker with an oar. You might be able to do it eventually, but it would work better to have something bigger. Lumension Chairman and CEO Pat Clawson suggests in a press release issued by his company that the new cyber security czar needs to have budget and policy authority, and he needs to report to the President. In other words, this needs to be a cabinet-level position.
I don’t think Clawson goes far enough. One of the biggest ongoing problems that afflicts federal IT is the lack of a realistic level of funding. Congress and the Executive Branch love to issue edicts of what Federal IT managers have to do in terms of security, management or standards. They issue compliance and auditing requirements. They bemoan the attacks on the IT infrastructure. But do they provide the money to pay for this? You guess.
The fact is that Federal IT managers, the ones that actually run the systems on a daily basis, are chronically underfunded, they are beset with conflicting requirements, and they are understaffed. They can’t spend money to solve the problem even if they have funding because the web of conflicting procurement regulations makes it nearly impossible to buy anything on a timely basis. It’s kind of like you finding a virus on your computer this year, but having to wait until 2014 to buy an anti-virus package.
The result is that federal IT managers are trying to hold back the rising tide with a couple of sandbags and their pinkie finger. The fact that they’re doing as well as they are is remarkable. The fact that they’re being asked to do it with less because of budgetary fantasies on the part of Congress is disturbing. The best leadership in the world can’t accomplish anything without the right tools, the right information and enough people. In other words, now that we have a cyber security czar trying to steer this oil tanker, maybe we should also buy him a bigger oar.
Click through to see key results from the Federal Cyber Security Outlook 2010 study of 201 Federal IT Decsion Makers, sponsored by Lumension Security and conducted by Clarus Research.
And the numbers are expected to climb as more countries develop cyber-espionage.
In fact, many think that escalation of cyber-warfare is imminent.
There more confidence overall, but only six percent said ability to respond was excellent.
The bad guys are getting smarter everyday.
Sometimes the biggest threats come from the people trusted most.