Two new surveys of 2,660 information workers and 560 IT managers and executives, conducted by International Data Corp. on behalf of Unisys, find that while usage of personally owned devices is growing in the enterprise, these are still pretty much used to augment traditional usage of PCs. At the same time, the survey shows that social media is used primarily for marketing purposes.
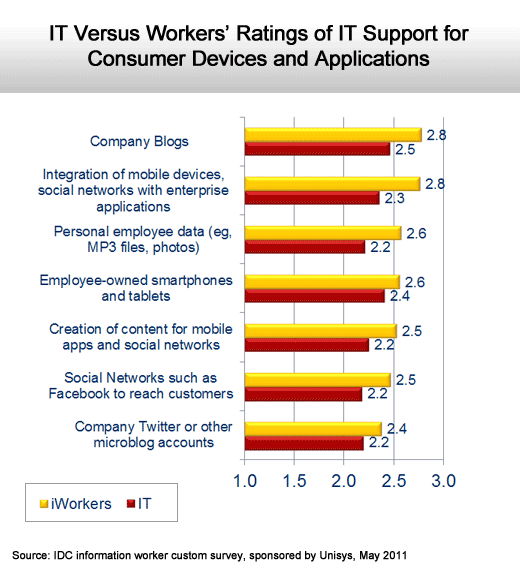
Interestingly, workers give internal IT more credit for supporting these devices than IT managers, which suggests there is a lot of extracurricular support provided by IT staff.
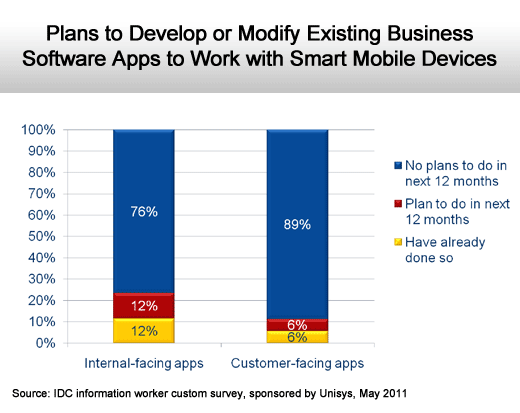
But despite the proliferation of these devices, any plans to optimize existing applications for mobile computing devices remain in relative infancy.
Click through for results from a survey on the consumerization of IT conducted by International Data Corp., on behalf of Unisys.
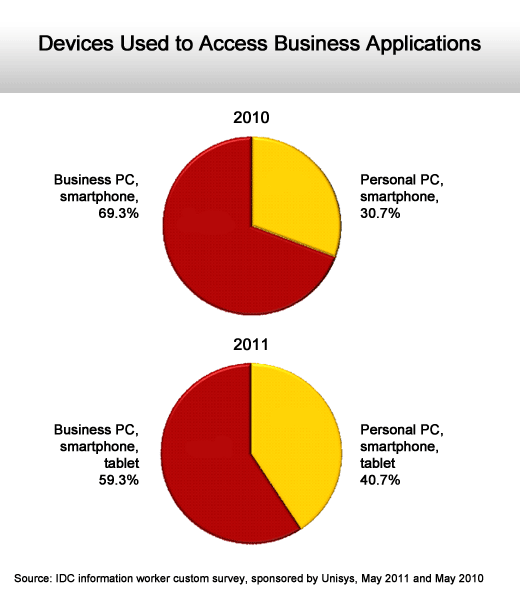
Personally owned devices gain at a steady rate.
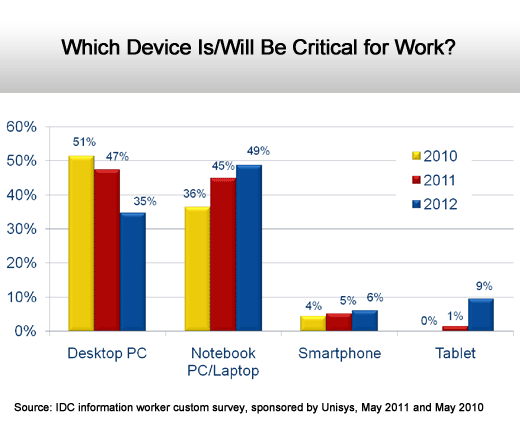
But the notebook still rules.
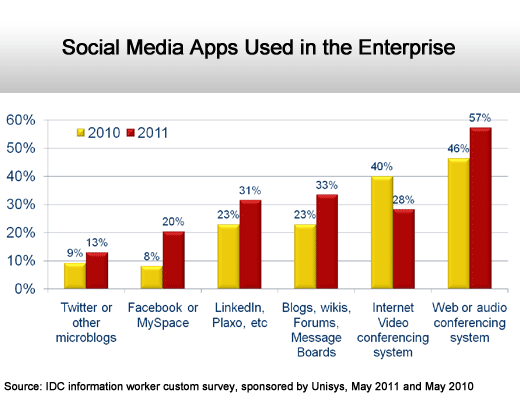
Videoconferencing declines.
Tablets will be critical and IT will work harder.
Workers think IT does a better job than IT does.
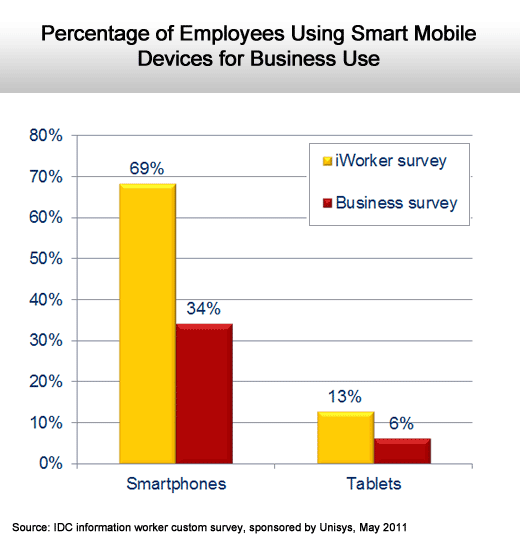
More usage than IT thinks.
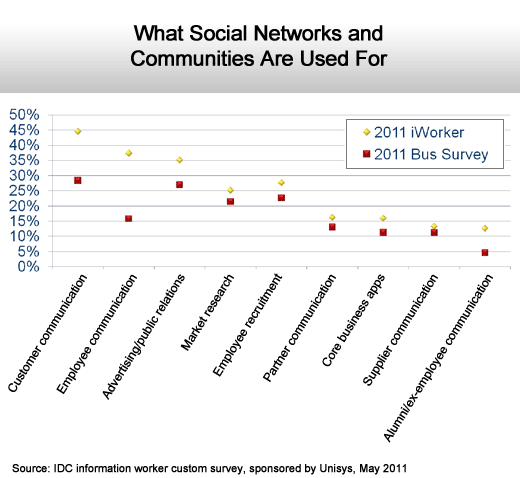
Marketing activities lead the way.
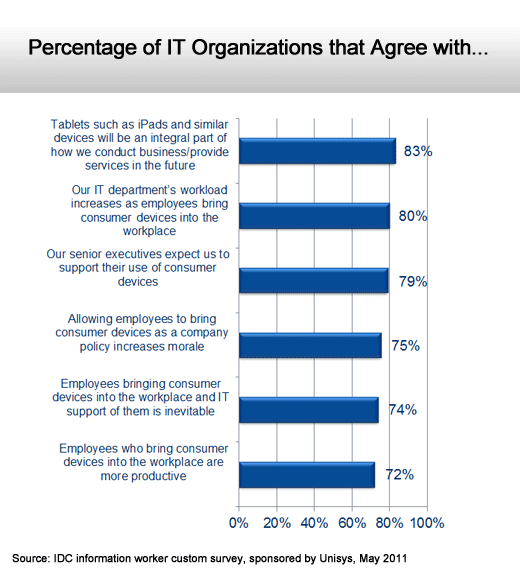
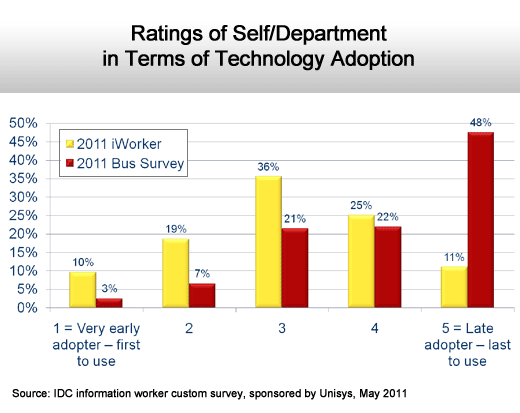
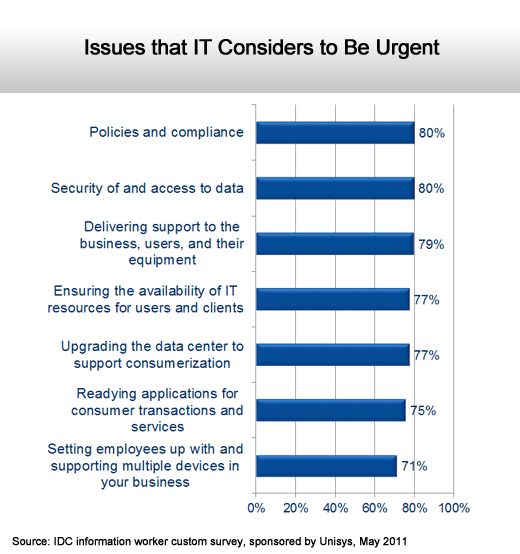
IT organizations remain conservative.
Work on internal-facing apps begins slowly.
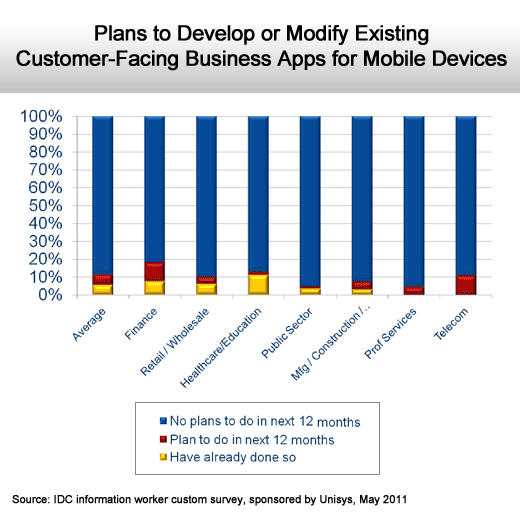
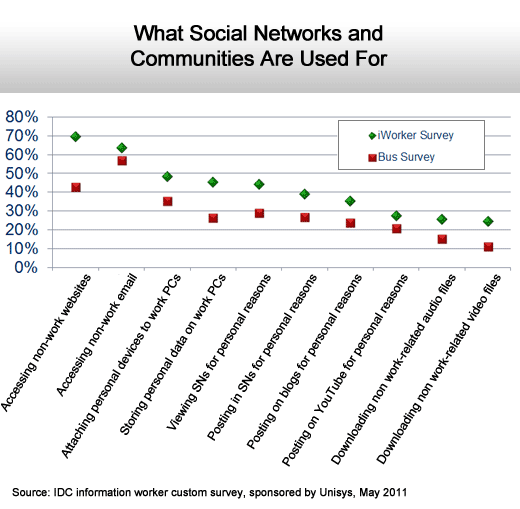
Not as much activity as one might think.
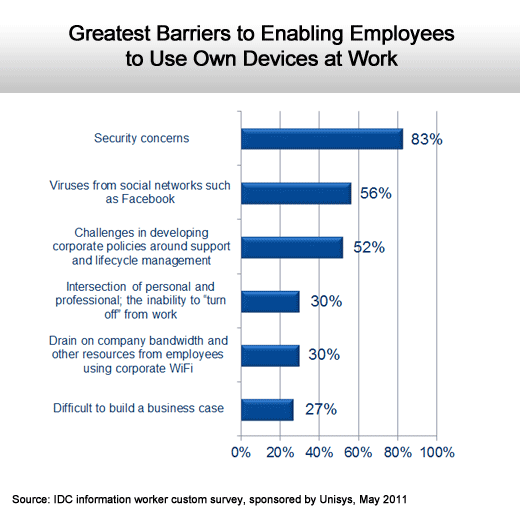
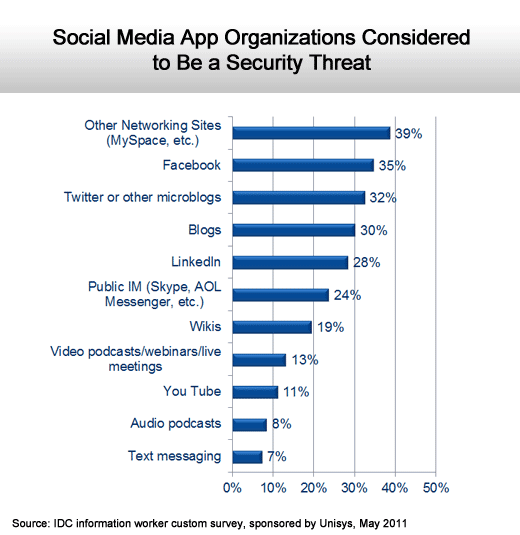
Security issues top the list.
Anything mobile.
Everything and anything social.
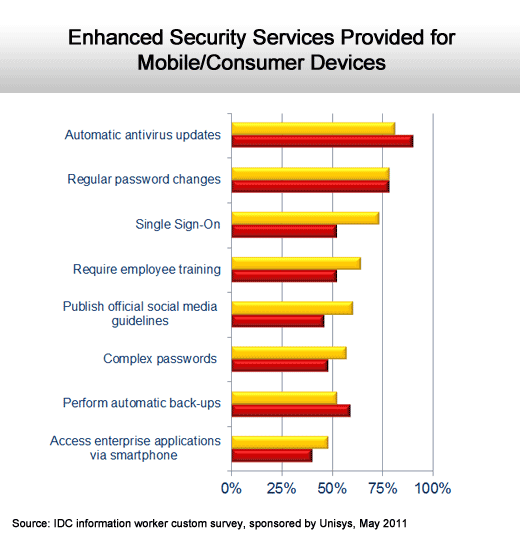
Anti-virus and password management top the list.
What isn’t urgent?
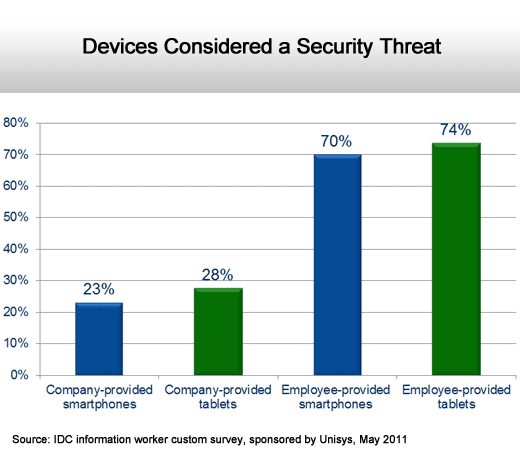
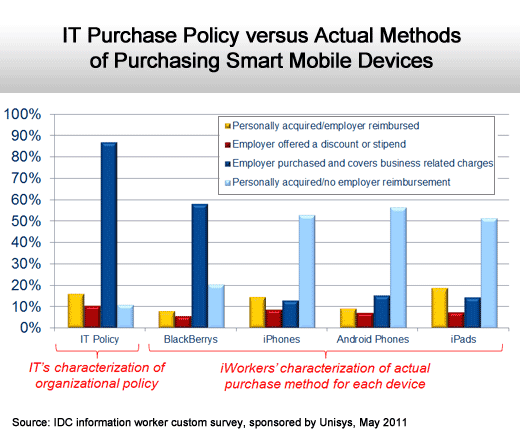
Apple and Android devices are employee owned.
Downloading and uploading are the real issues.