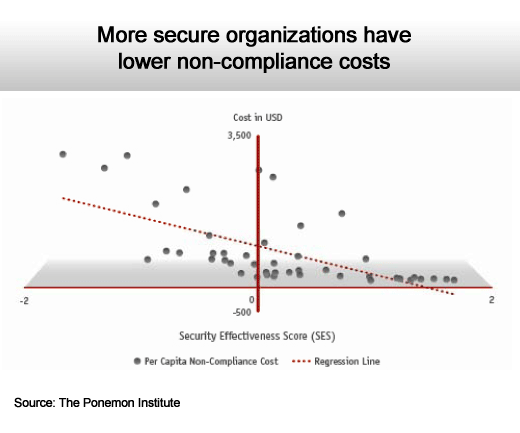
But a new survey of 160 information security experts working at 46 multinational companies, conducted by The Ponemon Institute on behalf for Tripwire, a provider of compliance management tools, finds that the companies that proactively manage compliance wind up paying a lot less over the long term than those that treat compliance as a cost to be avoided.
While no one can guarantee that their company will not be subjected to compliance-related penalties, the survey data shows that doing the bare minimum is roughly the equivalent of an invitation to financial disaster.
Click through for results from a survey on the true cost of compliance, conducted by The Ponemon Institute on behalf of Tripwire.
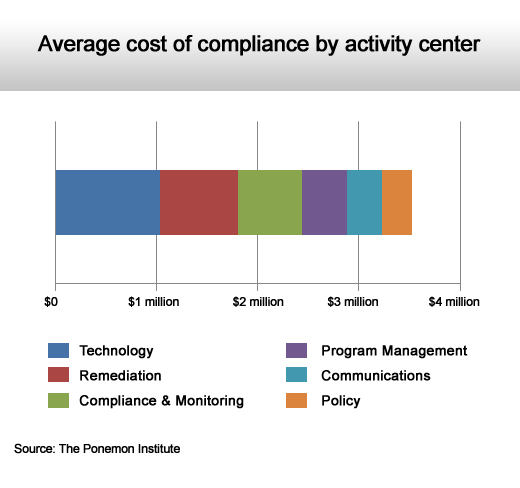
Costs can easily exceed $3 million when you add everything up.
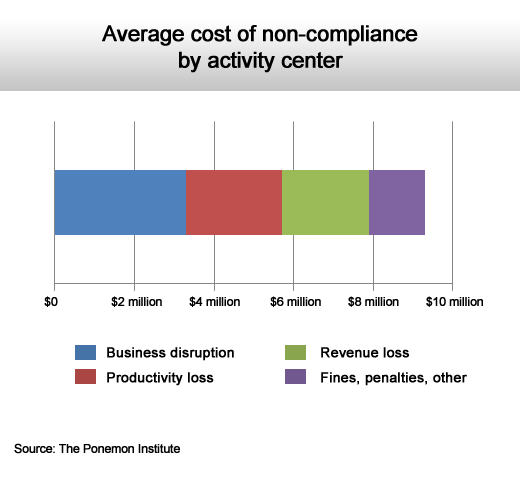
But it can cost over $9 million if you have don’t have the right controls in place.
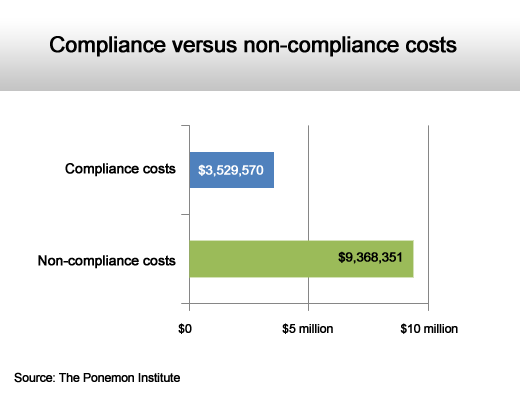
There’s $5.8 million in the difference.
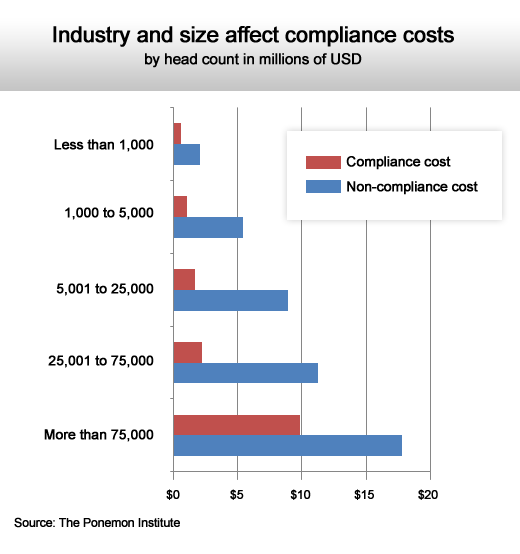
The bigger you are, the more it costs.
You can’t eliminate every cost, but you can mitigate them.
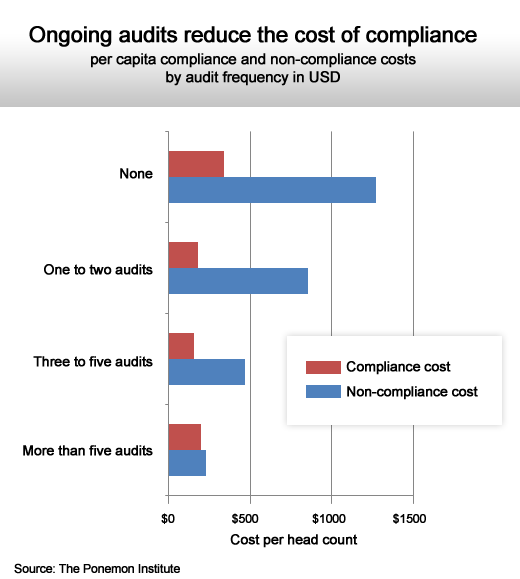
The more compliance work you do now, the less you pay later.