McAfee recently released its eighth annual study revealing the most dangerous celebrities to search for online. The study found a mix of comedians and musicians among the most dangerous, with Jimmy Kimmel, comedian and late night host of Jimmy Kimmel Live, replacing Lily Collins (Mirror, Mirror) as McAfee’s most dangerous celebrity in search. When searching for videos and downloads of Kimmel, McAfee reports that you have a 1 in 5 chance of clicking on a page that tests positive for viruses and other malware.
Jimmy Kimmel is the second male to find his way to the No. 1 spot (moving up from No. 39), following Brad Pitt in 2008. DJ Armin van Buuren takes the number-two spot behind Kimmel, and Ciara, the third. Additional celebrities in the top 10 include Blake Shelton, Britney Spears (holding her place at No.7), and three New Jersey natives: Bruce Springsteen, Jon Bon Jovi and Chelsea Handler.
Cybercriminals are constantly trying to find ways to take advantage of consumer interests, be it celebrities or other high-profile events. It’s important to educate users on the security risks that exist when searching for such news and media events, in order to keep their devices and personal data safe.
Here are McAfee’s most dangerous celebrities by category, as well as tips to keep users safe.
Most Dangerous Celebrities Online
Click through for the most dangerous cyber celebrities for 2014, as identified by McAfee. Also be sure to check out and share the tips for keeping end users safe online.
Dangerously Funny Men and Women
In addition to Jimmy Kimmel (No. 1), Chelsea Handler (No. 9), Jimmy Fallon (No. 12), Adam Sandler (No. 14), Jason Segel (No. 19), Wee Man (No. 35), and Cameron Diaz (No. 41) all rank in the top 50.
Country and EDM Artists Dance to the Top
Representing popular music genres on the rise, country music stars and electric dance music (EDM) artists pump up the top 50 list. Four musicians make the top 50, with two of them landing within the top 10: Armin van Buuren (No.2) and Blake Shelton (No.6). Other musicians at play include: Calvin Harris (No. 17) and Carrie Underwood (No.47).
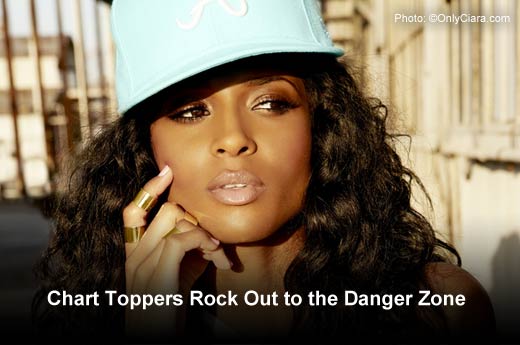
Chart Toppers Rock Out to the Danger Zone
This year, several rap, hip hop and R&B hit makers are in the top 20: Ciara (No. 3), Flo Rida (No. 4), 50 Cent (No. 13), Cheryl Cole (No. 16) and Iggy Azalea (No. 20). Additional superstars heating up the top 50 are Jason Derulo (No. 24), Jay Z (No. 26), Chris Brown (No. 28), Paul McCartney (No.29), Jennifer Lopez (No. 31), Pitbull (No. 34), Jessie J (No.44), Rihanna (No.45), Justin Timberlake (No.46), and Pharrell Williams (No. 49).
The Garden State
This year, four native New Jerseyians are in the top 25: Bruce Springsteen (No. 5), Bon Jovi (No. 8), Chelsea Handler (No. 9), and JWoww (No.23).
Romantic Comedy’s Leading Ladies
Several of America’s sweethearts are in the top 50 this year, including: Jessica Alba (No. 14), Kate Winslet (No. 18), Jennifer Lopez (No. 31), Jessica Biel (No. 33), Jennifer Aniston (No.37), Jennifer Garner (No.38), and Cameron Diaz (No.41).
Where Have the Kardashians Gone?
Last year, searching for downloads of Kanye West, Kourtney Kardashian, Kim Kardashian, Khloe Kardashian and Kris Jenner was popular among Americans. This year, the Kardashian clan is nowhere to be found. Instead, Jersey Shore star JWoww (No. 23) and celebrity mogul Jay Z (No. 26) claim spots on the list.
How You Can Stay Protected
- Beware of clicking on third-party links. You should access content directly from official websites of content providers. For example, visit ABC.com to find Jimmy Kimmel’s latest episodes.
- Ensure you use Web protection that will notify you of risky sites or links before you visit them. Stick to official news sites for breaking news.
- Don’t download videos from suspect sites. This should be common sense, but it bears repeating: Don’t download anything from a website you don’t trust — especially video. Most news clips you’d want to see can easily be found on official video sites and don’t require you to download anything.
- “Free downloads” is by far the highest virus-prone search term. Anyone searching for videos or files to download should be careful not to unleash unsafe content such as malware onto their computers.
- Always use password protection on your phone and other mobile devices. If you don’t and your phone is lost or stolen, anyone who picks up the device could have access to your personal information online.
- Don’t “log in” or provide other information: If you receive a message, text or email or visit a third-party website that asks for your information — credit card, email, home address, Facebook login or other information — to grant access to an exclusive story, don’t give it out. Such requests are a common tactic for phishing that could lead to identity theft.
- Search online using a tool, such as SiteAdvisor software, which protects users from malicious websites and browser exploits. A complimentary version of SiteAdvisor software can be downloaded at www.siteadvisor.com