In February 2015, Financials was the lone industry sector with cyber crime incidents above six-month averages. This is largely attributed to the massive breach at health insurer Anthem. SurfWatch Labs collects and analyzes cyber-incident data and through that process, Anthem accounted for an astonishing 42 percent of all the negative CyberFacts collected in February. This caused the Financials sector share of overall cybercrime discussion to jump by more than 33 points – from its 12 percent six-month average to 46 percent. Additionally, Financials had 46 distinct cybercrime targets discussed in February, a significant rise from January’s 28.
What happened in Consumer Goods, Information Technology and Health Care in February? Each saw slight improvement over January activity, although all industries unfortunately experienced notable incidents that call for due diligence. In this slideshow, Adam Meyer, chief security strategist, SurfWatch Labs, highlights the findings from each sector.

Cybersecurity Highlights by Industry Sector
Click through for cybersecurity highlights by industry sector for February, as identified by SurfWatch Labs.
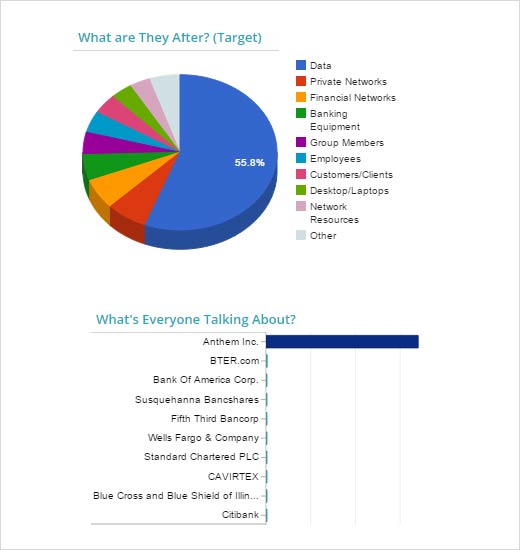
Financials
Anthem was the most discussed target as it reported the unauthorized access of 78.8 million records in its database, with between 8.8 million and 18.8 million of those records representing non-customers. Blue Cross Blue Shield customers were also affected. The top effects, or the results of cyber criminals’ activity in February, included credentials stolen/leaked, and infected/exploited assets, both of which saw significant jumps from the previous month. Other notable incidents also occurred, including a few Bitcoin exchanges that went offline, ATM hacking and a fax spam campaign using Dyer malware targeting Bank of America, Citibank and Wells Fargo customers. The Anthem breach effects will continue to ripple as cyber criminals use the data to start phishing scams and reports of fraudulent tax returns, child ID theft and more.
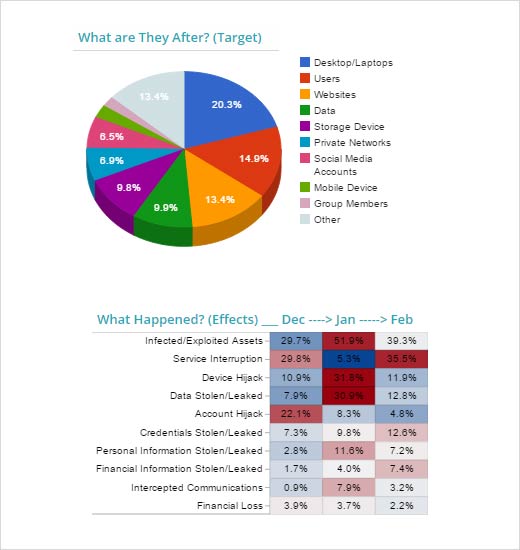
Information technology saw a slight decrease in cyber risk for February when compared to the sector’s six-month average. Desktop/laptops (20.3 percent), users (14.9 percent) and websites (13.4 percent) were the top trending targets and Lenovo received the bulk of attention for the month. The PC producer sold computers preinstalled with adware designed by Superfish to hijack Internet sessions and make users vulnerable to man-in-the-middle attacks. Also discussed was espionage against mobile phone SIM card maker Gemalto from reports leaked by Edward Snowden and increased hacktivist activity against ISIS Facebook and Twitter accounts. For the past three months, risk to the IT sector has continued to fall, yet social media accounts keep getting hijacked.
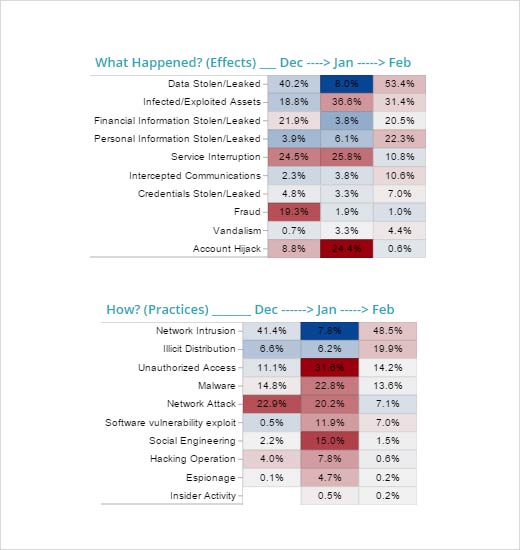
Consumer Goods
Consumer goods also saw a slight decrease in cyber risk for the month when compared to the sector’s six-month average. Websites increased as a top trending target from 18 percent to 34 percent while social media accounts, not even a trending target the previous month, moved to second place at 20.3 percent in February. Chipotle’s Twitter account was hijacked and used to send racist messages; Forbes Thought of the Day landing page was reportedly compromised by a Chinese espionage group to attempt to install malware on the attacked computer – a clear watering hole attack. Previously prominent attacks like Sony have finally subsided. The targeted asset score for the sector continued its decline from December and January, showing remarkable cooling of the payment system breaches that previously plagued the Consumer Goods sector.
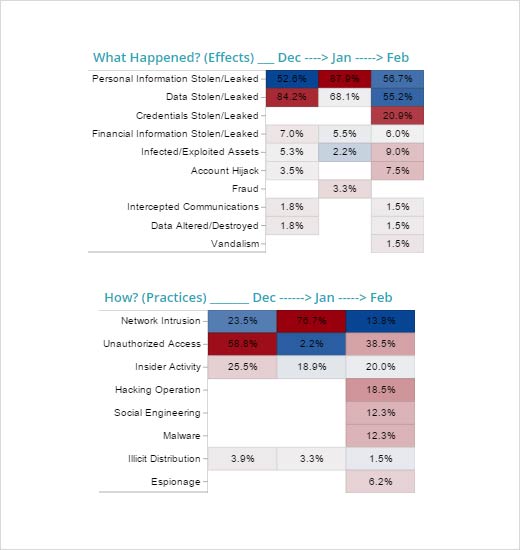
Health Care
A slight decrease in risk for health care was also seen in February. Data (83.6 percent) was by far the top trending result of cyber criminal activity, resulting in personal information stolen/leaked and credentials stolen/leaked appearing in 57 percent and 21 percent, respectively. How did the bad guys do it? The top practice in February was unauthorized access at 38.5 percent. The previous 90 days showed network intrusion as the top category, however that appeared in just 13.8 percent of the incidents in February. Several notable events occurred, including a stolen laptop affecting 7,900 patients at Riverside County Regional Medical Center, unauthorized patient access of 14,000 by an employee at UMass Memorial Medical Group, and the loss of medical paperwork that fell out of a courier vehicle on behalf of Kaiser Permanente Hawaii, affecting 6,600 patients. In Tennessee, 500 employees were notified that their information was stolen and used by thieves to try to file bogus tax returns in their names. These and other examples show the many potential attack vectors common across health care.

Technology Countermeasures
Based on attacks that occurred in February, a key takeaway from a risk mitigation perspective is to leverage encryption – especially for data at rest. Each sector was affected by a cyber threat that could have been mitigated through the proper use of robust encryption. Here are the different ways you can deploy encryption to mitigate the risk of data at rest being lost or stolen, prioritized by user exposure:
- Try to ensure full-disk encryption for all mobile devices such as laptops, tablets and phones. It’s important to note that technology makes it easy to share information as devices automatically sync information from device to device and in many instances you’ll have personal and corporate information on the same device. A compromised device can theoretically affect your entire ecosystem.
- File and folder encryption, preferably certificate-based, is the next level of encryption to deploy to mitigate the risk from users migrating data from the corporate-secured application and device to their own. An example of this would be a user pulling data out of an application and building pivot tables in a spreadsheet. More data migrates from the theoretically better secured application and database system of record to the user’s desktop, where it is no longer encrypted at rest as the workstation is in use. For this encryption capability, human factors such as ease of use and substantial employee training need to be a focal point of the solution.
- Application and database encryption is the area that holds the most legal and regulatory risk but has the least amount of human factors involved from a user standpoint and therefore can be engineered into a standard solution. The interaction between applications and databases also is generally your transactional systems of record that typically process customer payments, order fulfillment, enterprise resource planning and customer relationship management activities. While they might not be as exposed as your user base, they hold large quantities of data that is of value. In this area, you will want to ensure that encryption best practices are fully in place at the application and/or database environment and that key management process and key custodian are strictly enforced, as the strength in any encryption system resides with the level of key size and key management.
While using encryption does not mitigate all risks, it does mitigate a significant portion of risks to your technology-based legal and regulatory landscape such as HIPAA, HITECH, PCI-DSS, etc. Unfortunately, encryption can be challenging in many technology environments, placing a burden on ease of use for your users as well as affecting performance of some enterprise applications. Of course, every month brings different attacks and different appropriate countermeasures as attackers and threats evolve.














