Security is a hot topic today. Only a few years ago, security was on the back burner of most IT departments, seen as a necessary evil with few executives ever exposed to it. With the recent spate of high-profile attacks and ensuing losses, IT security is now viewed as the difference between an organization’s ability to carry out its mission and going out of business. This is why security is a topic frequently appearing on board meeting agendas and piquing the interest of C-suite executives.
While funding and awareness have increased, it is unclear if organizations are making investments in keeping up with the evolving security landscape. A lot of the newly available funding and resources have been allocated to the existing funding gaps and “perceived” deficiencies in an organization’s security posture. This is why IT security is a $58B market today but organizations are not any safer than they were a few years ago. In this slideshow, Shel Sharma, marketing manager at security startup Cyphort, discusses the evolution in the security landscape and how to align new security budgets and resources with this new paradigm vs. investing in more of the same old security.
The Evolution of Security
Click through for a closer look at how the security landscape has changed and suggestions for how organizations can better protect themselves, as identified by Shel Sharma, marketing manager at security startup Cyphort.
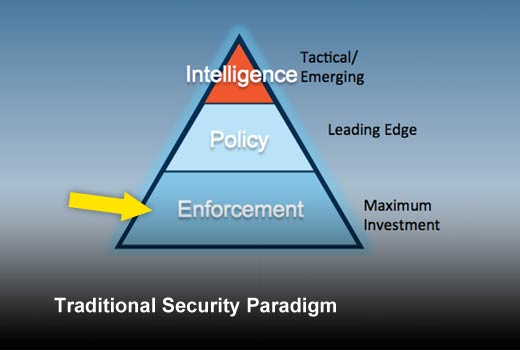
Traditional Security Paradigm
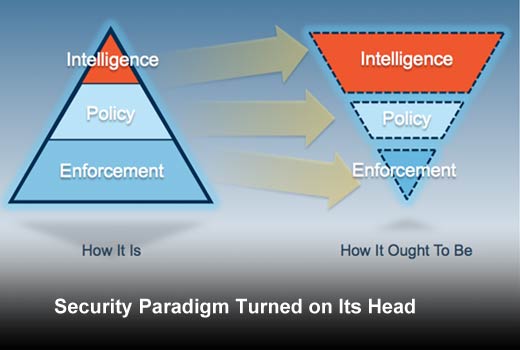
The security paradigm as most organizations view it.
Looking at resource and funding trends, it is clear that most mainstream organizations view IT security requirements as follows. (Please note that some of the solutions and projects listed under one category will span across more than one category but they are listed under the category they fit the best. As an example, Firewalls are primarily an enforcement point but they do have policy control functions and sometimes intelligence functionalities as well.)
Enforcement: Enforcement takes the lion’s share of IT budgets and resources. Investments in antivirus software, IPS/IDS, firewalls, web gateways and email anti-spam solutions can be categorized as primarily enforcement centric. This area of IT security is quickly commoditizing with focus moving to policy management and in some cases to intelligence functions.
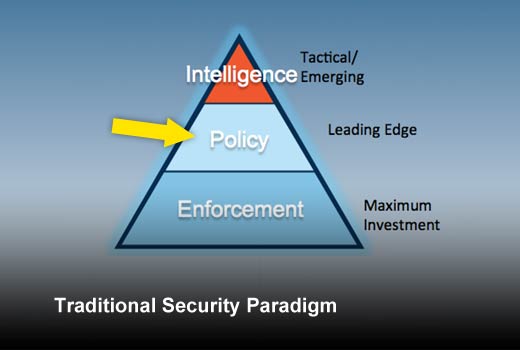
Traditional Security Paradigm
Policy management and access control: These technologies provide a layer over enforcement in order to drive it with pre-configured knowledge of what should be allowed and what shouldn’t be. Identity and access management, “Next Gen” part of NGFW, policy control functionality of secure web gateway provide the backbone of this section.
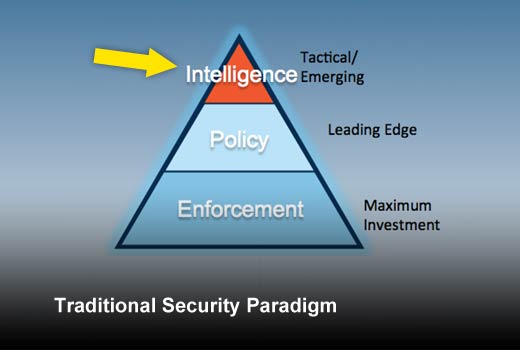
Traditional Security Paradigm
Intelligence: Intelligence is the new kid on the block. This refers to the investments in understanding the security threats to your organization and capabilities to respond to these threats. There are solutions and services in the market that pertain to continuous monitoring; threat and attack detection, incident response and forensics fall into this category. While few leading organizations have embraced these, most organizations are still dabbling in these areas, trying to build an understanding of how these technologies can help. As with any emerging technology, lots of seemingly different options are available and that creates confusion in the market.
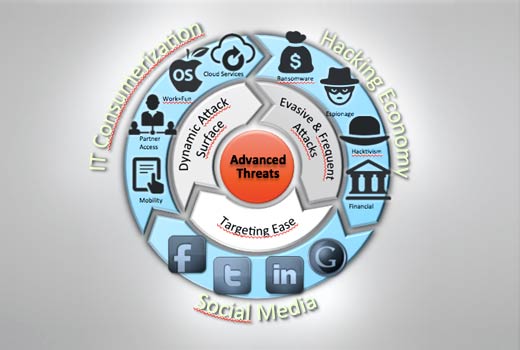
The Changing IT Security Landscape
IT security needs aren’t what they used to be just a few years ago. The latest IT trends of consumerization and social media, combined with readily available funding for malicious actors from profit-minded criminal organizations and nation states, has completely transformed the landscape. Hackers have figured out ways to bypass most security enforcement techniques. Additionally, consumerization of IT has blurred the lines between what’s within the purview of the IT organization and what isn’t, making policy control challenging and ineffective. Finally, social media has made it much easier to find and target people and organizations accurately, reducing hurdles for malicious actors. This is why Gartner stated that “Security organizations must assume they are compromised and invest in detective capabilities that provide continuous monitoring.”
Security Paradigm Turned on Its Head
The changing security landscape has made it clear that enforcement and policy control, while essential to security needs, are not sufficient when dealing with some of the biggest risks for IT. The biggest risks come from the actors that have the know-how and will to defeat these controls. This is why the existing security paradigm needs to be turned on its head with a focus on finding and rooting out these threats.
Organizations need to reevaluate their IT security investments to see whether they match this new reality or if they are geared toward maintaining the status quo. The following slides include pointers that will help you evaluate new projects and align your activities with the new landscape.
Solution and Service Investments
This should be the biggest area of focus. When procuring new solutions or services, ask: Will this purchase enhance my understanding of new threats or is it just a better enforcement/policy mousetrap? When upgrading an existing security portfolio, seek solutions that are heavily tilted toward intelligence while providing the necessary policy/enforcement as simple add-ons or freebies. One example would be investment in endpoint AV software; instead of upgrading the existing AV software, see if it makes sense to use free AV solutions from reputed vendors and combine it with investment in next-generation network or endpoint malware detection and response tools.
Another area to look after is compliance. Compliance directives take years to catch up to the new realities. If required by the compliance directives, seek products that would also help in the “intelligence” bucket while satisfying the old compliance requirements. One example of this would be IDS/IPS products. Instead of investing further in these areas, look at network-based threat detection technologies that may provide this functionality as a simple add-on or base capability.
In general, if you are writing a large check for endpoint antivirus, Firewall, IDS/IPS etc., pause and ask if this investment improves your “intelligence” capabilities. If not, consider how this investment can be minimized in order to align the remaining funding with the security needs of today.
Security Automation
Automation is another area that can help stretch security dollars to focus on the higher order security demands of today. This will also help deal with skills and qualified personnel challenges that exist in the field. When procuring new security products ask what people and skill requirements exist to operate these. When upgrading existing enforcement/policy infrastructure, focus on products that automate a large number of routine manual tasks to divert investment where it is needed.
Headcount Investments
Take a close look at your overall security hiring and skills portfolio. If you are doing it right, the share of skills required for forensics, threat investigation and incident response would increase while reducing regular operational roles that can be automated.
Reporting and Metrics
Security reporting is an area that has largely been compliance driven. A new security paradigm requires changes to the metrics and reports you focus on. When adding new capabilities in this area, ask if this will help you answer questions in the boardroom. Does the new reporting enhance your understanding of advanced attacks in your organization? Does it provide information on how you are doing against your peers?
Some of the key things to look for are existing and emerging attacks and trends over time and against industry averages — when there are shifts in trends, root causes for those, the time it takes to discover threats from when they first penetrated your organization, the time to containment and remediation from first discovery and trends as they relate to new investments in these areas.
Summary
As you can see, security requirements have changed dramatically over the past few years, while investments and focus have not. Today’s executives need to follow closely where the new investments are going and what new capabilities are being created within organizations that will help align better with the new security landscape. Better security outcomes belong to those who are able to change with the security landscape.